Gandalf_The_Grey
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
- Apr 24, 2016
- 7,871
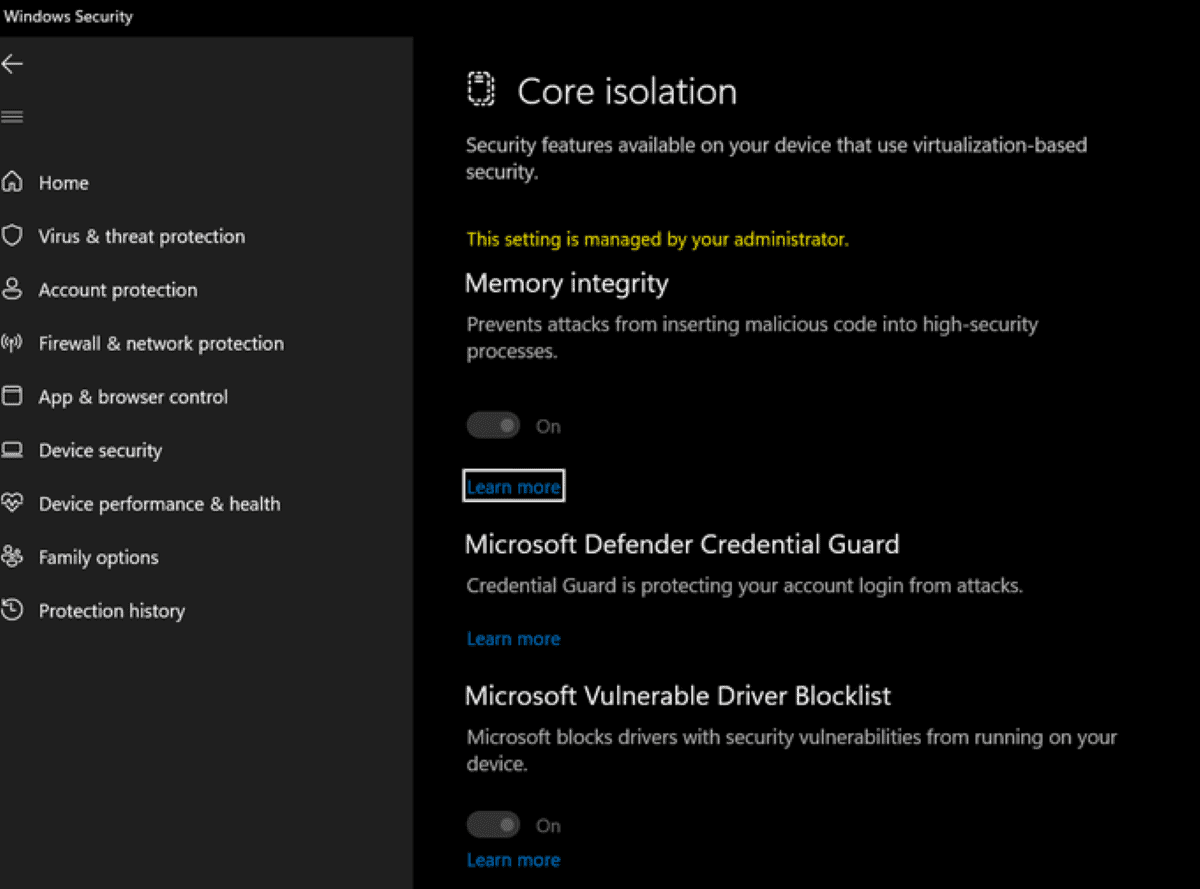
Windows Defender has very recently gained a new capability called "Microsoft Vulnerable Driver Blocklist". The feature is a part of Defender's Application Control option and will essentially protect devices from malicious drivers. Microsoft's Vice President of Enterprise and OS Security, David Weston, on Twitter, brought attention to the new feature.
The feature was added recently and in a blog post related to it, Microsoft has described how the new driver blocklist will help protect Windows devices:
The vulnerable driver blocklist is designed to help harden systems against third party-developed drivers across the Windows ecosystem with any of the following attributes:
Microsoft says that it identifies such harmful drivers by working with its various vendor partners and adds these to its "ecosystem block policy". These are then applied to Hypervisor-protected code integrity (HVCI)-enabled devices or those with S mode. The feature is available on Windows 11, 10, and Server 2016 and higher.
- Known security vulnerabilities that can be exploited by attackers to elevate privileges in the Windows kernel
- Malicious behaviors (malware) or certificates used to sign malware
- Behaviors that are not malicious but circumvent the Windows Security Model and can be exploited by attackers to elevate privileges in the Windows kernel
Microsoft has good reason to be on high alert against such drivers. In the past, as well as more recently too, plenty of Windows and Windows-signed drivers have been found to be compromised.

Defender will now protect against malicious drivers with new "Vulnerable Driver Blocklist"
Microsoft Defender now has a new feature that will protect Windows 11, Windows 10, and Windows Server devices from malicious drivers. The feature is termed "Microsoft Vulnerable Driver Blocklist".