DefenseWall Personal Firewall
version: 3.13
http://www.softsphere.com/
When it comes to stopping malware the outbound protection a software firewall can offer is the last line of defense. If you have an antivirus installed it already failed to detect and block the threat. In fact, the malicious software is already present on your computer and it is running. At this point it is possible for the malicious process to access the Internet without triggering a firewall alert (for example by using applications that are normally allowed through a firewall, like the browser). To be really efficient at blocking malware from accessing the Internet, a software firewall needs something "extra". DefenseWall Firewall provides that extra protection with its policy-based sandboxing technology (without file/registry virtualization). It might sound complicated but this product is easy to use and unlike other similar applications it won't display numerous pop-ups requiring your assistance.
DefenseWall Firewall is not your average packet filtering application. It is intended to be used as an extra layer of protection for your system and it can run side by side with your antivirus product as well as simple firewall programs (as the default windows firewall).
DefenseWall devides your applications in two groups: Trusted and Untrusted. Applications allowed to access the Internet or the network as well as applications residing on removable drives or in Shared folders are considered to be opened doors than can provide a way for malware to reach your system. DefenseWall labels them as "Untrusted" and prevents them from altering your system. Every file created or process launched by an Untrusted application is also considered Untrusted.
First of all I should mention that it is recommended to install this product on a clean machine. It will only work on 32bit versions of Windows and there are currently no plans for 64bit support. Installation is extremely fast and easy. After a restart the product asks you if it should check for an updated version and it is ready to protect your system.
It has a minimalistic interface with 5 tabs. Some users might need some time to get accustomed to the interface. Although the applicationn provides great default settings I would recommend users to visit the second tab labeled "Untrusted applications" after intalation. As I mentioned above these are applications that DefenseWall considers to be threat gates. The list is already populated with the applications DefenseWall found on your system, however if you have an application that connects to the Internet and DefenseWall didn't identified it, I advise you to add it here: Internet browsers, P2P and IM clients, e-mail clients should all be here.
The second tab you might want to visit is the Advanced tab. Click the Secured Files button and in the list add files and folders where you store private/confidential data. DefenseWall will make sure that Untrusted applications will not have any kind of access to them (efficient against ransomware type of malware). This is pretty much all the configuration this application needs.
The first thing that you might notice is that the program adds overlays to your icons to suggest that the application will be launched as Untrusted. A Defense Wall entry gets added to the context menu and enables you to open the file as Trusted/Untrusted or to change its status among other things. The text inside the Title Bar of an Untrusted application indicates its status. However there is no border around the application or any other way to indicate that it runs as Untrusted if the Title Bar isn't visible. Not a big problem for me since I dislike those borders anyway but Firefox4, for example, has the title bar hidden under Windows 7 by default.
[attachment=328][attachment=329]
Back to the interface, the first tab (Stop Attack) has a button indicating the number of untrusted processes running and clicking it will allow you to kill individual processes. You can kill all untrusted processes at once by using the big red Stop Attack button. (Random thought: the title of this button might confuse novice users that there is something wrong happening). From the same tab you can rollback file and registry changes however this operation is reserved to Advanced Users. The Go Banking/Shopping button will close all untrusted processes and will start your browser thus ensuring that there is no keylogger running.
[attachment=327]
The Log tab displays previous events. According to the help file a maximum of 50 events can be displayed and the Filter button allows you to exclude certain events from appearing in the log next time they happen. I must admit that I was expecting it to do something else - allow me to search through existing events for example. The log can be exported as a text file.
DefenseWall has a great degree of flexibility that allows users to fix compatibility issues with existing software. In the Advanced tab you can add file and registry exclusions, allow some applications to act as screen recorders or restart the system. In my opinion this sort of flexibility is must have for sandboxing type applications. As a side-note, I encountered no compatibility issues with any of my installed applications.
As I mentioned in the beginning this application is not a pure firewall. If you are looking for complicated rules inside the Firewall tab you won't find any and the firewall is based on the same Trusted/Untrusted criteria.
[attachment=337]
The help file is a bit outdated but should be sufficient in most cases. Support is provided by e-mail and on the official forum.
Installing Popular Software
One problem with sandboxing type applications is that they sometimes block software from installing (since the installer runs as sandboxed). It is recommended to run installers that you are absolutely sure they are safe as Trusted. I've downloaded 8 random applications to a folder on my Desktop and ran the installers. The folder is important since in DefenseWall some locations are Download Areas (see Options > Download Areas) and threated differently: according to the help file, if installers downloaded in these areas are digitally signed by a Trusted Vendor the installer is re-started as Trusted and the installation occurs without any pop-ups from DefenseWall. This was the case with:
So with DefenseWall the user doesn't have to click Trusted/Untrusted every time he or she launches an installer. Digitally signed files from trusted vendors will run from the protected "Download Areas" automatically as Trusted. However, I am unable to confirm if DefenseWall treats all digitally signed files the same or actually has a list of Trusted Vendors. In any case, this list is not visible (editable) within the interface.
Stopping Malware
[attachment=334]
For what is worth I ran CLT (Comodo Leak Test) as Untrusted and DefenseWall managed to score 330/340. The only test failed was Invasion: FileDrop. This shouldn't be an issue however when it comes to real malware since the dropped files are treated as untrusted and can't affect the system. I should mention that this excellent score was achieved with only 4 pop-ups (including the one asking if CLT should start as Untrusted - screenshots bellow).
[attachment=331][attachment=332][attachment=333]
In a small test using malware samples DefenseWall managed to block all running malicious processes after clicking the Stop Attack button. Using the File and Registry Rollback feature I was able to remove traces malware left behind up to the point were Malwarebytes and HitmanPro couldn't find any sign of infection. This feature however is reserved to advanced users and it is not impossible for some malware to leave some traces behind. In any case, even if you don't rollback changes, all traces should be harmless to the system. Keep in mind that DefenseWall is not an antivirus replacement.
My wish-list:
version: 3.13
http://www.softsphere.com/
When it comes to stopping malware the outbound protection a software firewall can offer is the last line of defense. If you have an antivirus installed it already failed to detect and block the threat. In fact, the malicious software is already present on your computer and it is running. At this point it is possible for the malicious process to access the Internet without triggering a firewall alert (for example by using applications that are normally allowed through a firewall, like the browser). To be really efficient at blocking malware from accessing the Internet, a software firewall needs something "extra". DefenseWall Firewall provides that extra protection with its policy-based sandboxing technology (without file/registry virtualization). It might sound complicated but this product is easy to use and unlike other similar applications it won't display numerous pop-ups requiring your assistance.
DefenseWall Firewall is not your average packet filtering application. It is intended to be used as an extra layer of protection for your system and it can run side by side with your antivirus product as well as simple firewall programs (as the default windows firewall).
DefenseWall devides your applications in two groups: Trusted and Untrusted. Applications allowed to access the Internet or the network as well as applications residing on removable drives or in Shared folders are considered to be opened doors than can provide a way for malware to reach your system. DefenseWall labels them as "Untrusted" and prevents them from altering your system. Every file created or process launched by an Untrusted application is also considered Untrusted.
First of all I should mention that it is recommended to install this product on a clean machine. It will only work on 32bit versions of Windows and there are currently no plans for 64bit support. Installation is extremely fast and easy. After a restart the product asks you if it should check for an updated version and it is ready to protect your system.
It has a minimalistic interface with 5 tabs. Some users might need some time to get accustomed to the interface. Although the applicationn provides great default settings I would recommend users to visit the second tab labeled "Untrusted applications" after intalation. As I mentioned above these are applications that DefenseWall considers to be threat gates. The list is already populated with the applications DefenseWall found on your system, however if you have an application that connects to the Internet and DefenseWall didn't identified it, I advise you to add it here: Internet browsers, P2P and IM clients, e-mail clients should all be here.
The second tab you might want to visit is the Advanced tab. Click the Secured Files button and in the list add files and folders where you store private/confidential data. DefenseWall will make sure that Untrusted applications will not have any kind of access to them (efficient against ransomware type of malware). This is pretty much all the configuration this application needs.
The first thing that you might notice is that the program adds overlays to your icons to suggest that the application will be launched as Untrusted. A Defense Wall entry gets added to the context menu and enables you to open the file as Trusted/Untrusted or to change its status among other things. The text inside the Title Bar of an Untrusted application indicates its status. However there is no border around the application or any other way to indicate that it runs as Untrusted if the Title Bar isn't visible. Not a big problem for me since I dislike those borders anyway but Firefox4, for example, has the title bar hidden under Windows 7 by default.
[attachment=328][attachment=329]
Back to the interface, the first tab (Stop Attack) has a button indicating the number of untrusted processes running and clicking it will allow you to kill individual processes. You can kill all untrusted processes at once by using the big red Stop Attack button. (Random thought: the title of this button might confuse novice users that there is something wrong happening). From the same tab you can rollback file and registry changes however this operation is reserved to Advanced Users. The Go Banking/Shopping button will close all untrusted processes and will start your browser thus ensuring that there is no keylogger running.
[attachment=327]
The Log tab displays previous events. According to the help file a maximum of 50 events can be displayed and the Filter button allows you to exclude certain events from appearing in the log next time they happen. I must admit that I was expecting it to do something else - allow me to search through existing events for example. The log can be exported as a text file.
DefenseWall has a great degree of flexibility that allows users to fix compatibility issues with existing software. In the Advanced tab you can add file and registry exclusions, allow some applications to act as screen recorders or restart the system. In my opinion this sort of flexibility is must have for sandboxing type applications. As a side-note, I encountered no compatibility issues with any of my installed applications.
As I mentioned in the beginning this application is not a pure firewall. If you are looking for complicated rules inside the Firewall tab you won't find any and the firewall is based on the same Trusted/Untrusted criteria.
- By default, outbound connections from Trusted applications are allowed while inbound connections to them are prohibited (ports are closed).
- As for Untrusted processes, DefenseWall controls those that are connecting to web and warns you when a program is not under the outbound rules. Open listening ports are not an issue with Untrusted applications since they are already sandboxed and any possible exploit can't succeed.
[attachment=337]
The help file is a bit outdated but should be sufficient in most cases. Support is provided by e-mail and on the official forum.
Installing Popular Software
One problem with sandboxing type applications is that they sometimes block software from installing (since the installer runs as sandboxed). It is recommended to run installers that you are absolutely sure they are safe as Trusted. I've downloaded 8 random applications to a folder on my Desktop and ran the installers. The folder is important since in DefenseWall some locations are Download Areas (see Options > Download Areas) and threated differently: according to the help file, if installers downloaded in these areas are digitally signed by a Trusted Vendor the installer is re-started as Trusted and the installation occurs without any pop-ups from DefenseWall. This was the case with:
- Aida64 Extreme Edition
- CCleaner
- Defraggler
- Firefox 5 beta
- Power Archiver
- Sticky Password Manager
- VLC
- Adept PDF to Excel Converter
So with DefenseWall the user doesn't have to click Trusted/Untrusted every time he or she launches an installer. Digitally signed files from trusted vendors will run from the protected "Download Areas" automatically as Trusted. However, I am unable to confirm if DefenseWall treats all digitally signed files the same or actually has a list of Trusted Vendors. In any case, this list is not visible (editable) within the interface.
Stopping Malware
[attachment=334]
For what is worth I ran CLT (Comodo Leak Test) as Untrusted and DefenseWall managed to score 330/340. The only test failed was Invasion: FileDrop. This shouldn't be an issue however when it comes to real malware since the dropped files are treated as untrusted and can't affect the system. I should mention that this excellent score was achieved with only 4 pop-ups (including the one asking if CLT should start as Untrusted - screenshots bellow).
[attachment=331][attachment=332][attachment=333]
In a small test using malware samples DefenseWall managed to block all running malicious processes after clicking the Stop Attack button. Using the File and Registry Rollback feature I was able to remove traces malware left behind up to the point were Malwarebytes and HitmanPro couldn't find any sign of infection. This feature however is reserved to advanced users and it is not impossible for some malware to leave some traces behind. In any case, even if you don't rollback changes, all traces should be harmless to the system. Keep in mind that DefenseWall is not an antivirus replacement.
- MrXidus made an excellent prevention test video of DefenseWall Personal Firewall.
- DefenseWall gets excellent results in MRG Flash Tests.
- AV-Comparatives did a review of an older version of the product (See Single Product Reviews - good results, as usual).
My wish-list:
- Allow users have control over the list of Trusted Vendors.
- Add an option to allow Inbound connections only from certain trusted IP-s inside the network.
Attachments
-
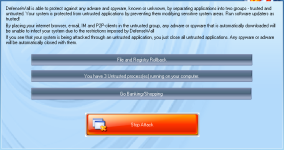 Image 063.png80.3 KB · Views: 858
Image 063.png80.3 KB · Views: 858 -
 Image 064.png8.3 KB · Views: 1,549
Image 064.png8.3 KB · Views: 1,549 -
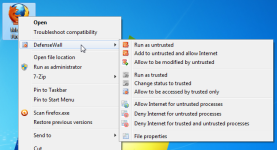 Image 066.png81.2 KB · Views: 843
Image 066.png81.2 KB · Views: 843 -
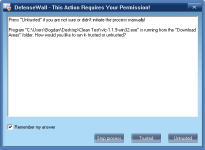 Image 058.png12.4 KB · Views: 1,059
Image 058.png12.4 KB · Views: 1,059 -
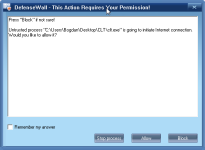 Image 059.png12.1 KB · Views: 832
Image 059.png12.1 KB · Views: 832 -
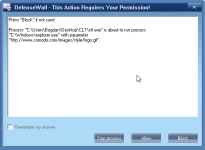 Image 060.png12.4 KB · Views: 810
Image 060.png12.4 KB · Views: 810 -
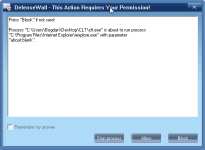 Image 061.png12.3 KB · Views: 812
Image 061.png12.3 KB · Views: 812 -
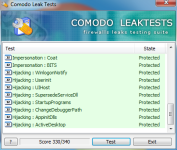 Image 068.png77.2 KB · Views: 865
Image 068.png77.2 KB · Views: 865 -
 Image 069.png24.3 KB · Views: 724
Image 069.png24.3 KB · Views: 724