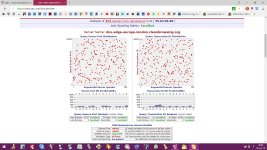
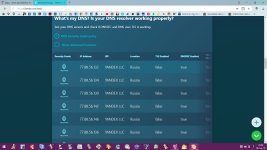
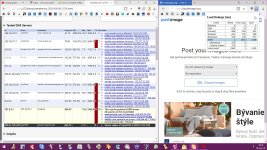
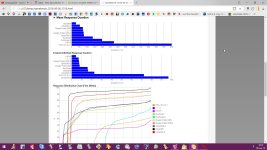
Today, I've just tested some public dns for their susceptibility to Kaminsky-style spoofing & got some interesting results.Now,I would like to share those results to other members of MT & would like to get some analysis,comments or feedbacks. & if possible please tell what dns server you use & why?
The list of public dns servers which undergone test namely Google,Quad9,DNS.WATCH,Comodo Secure DNS,OpenDNS Home,Norton ConnectSafe,OpenNIC,FreeDNS,Alternate DNS,Yandex.DNS,Adguard dns beta,UncensoredDNS,Cloudfare.
Adguard DNS beta Alternate DNS Cloudfare Comodo Secure DNS DNS.WATCH FreeDNS Google Public DNS Norton ConnectSafe OpenDNS Home OpenNIC
Quad9 DNS UncensoredDNS Yandex.DNS
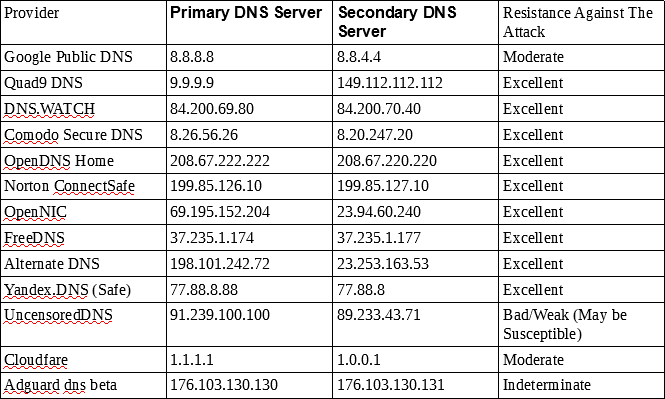
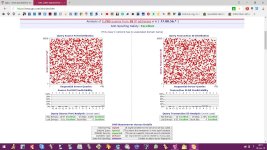
The list of public dns servers which undergone test namely Google,Quad9,DNS.WATCH,Comodo Secure DNS,OpenDNS Home,Norton ConnectSafe,OpenNIC,FreeDNS,Alternate DNS,Yandex.DNS,Adguard dns beta,UncensoredDNS,Cloudfare.
Adguard DNS beta Alternate DNS Cloudfare Comodo Secure DNS DNS.WATCH FreeDNS Google Public DNS Norton ConnectSafe OpenDNS Home OpenNIC
Quad9 DNS UncensoredDNS Yandex.DNS
Last edited: