Windows_Security
Level 24
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
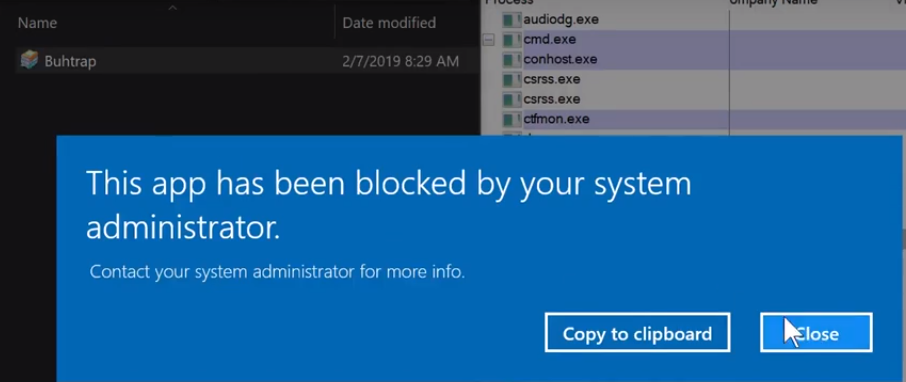
Picture explains it all. In one of the test videos the testers response after this block is to run the sample as admin and passes SRP. And hard-configurator allows it (because it is set up that way). Next ransomware with admin rights destroys the system. What is the consensus of the members. Block or Fail