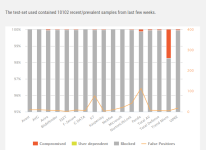
Please, look at this chart:
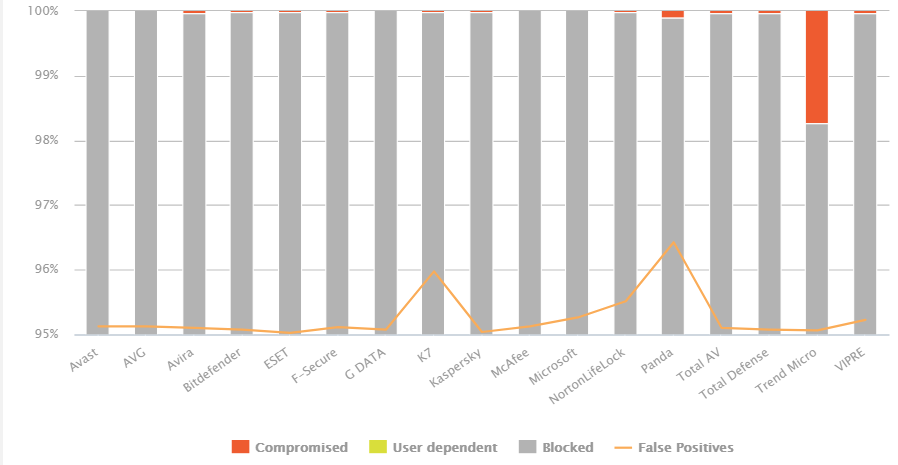
The above chart comes from the AV-Comparatives Malware Protection test (September 2020, over 10000 samples tested). We can see the extremely poor result for Trend Micro.
Similar results can be seen in the AV_Comparatives test from March 2020 and in the test made by AVLab in May 2020 (over 1000 samples tested):
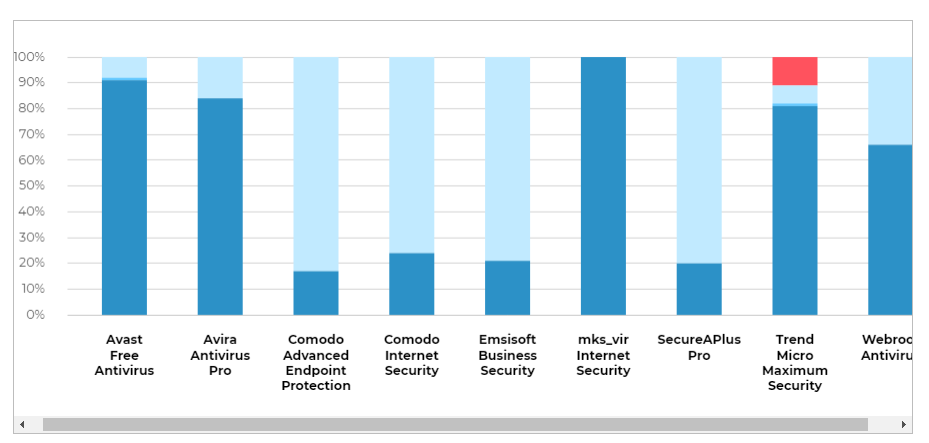
The test from AVLab is even more striking because all other AVs scored 100% detection (Trend Micro scored only 89%). I think that most people would quickly reach one of the below conclusions:
The first observation is that these results look like all tested AVs already knew the malware samples except Trend Micro. If so, then Trend Micro will get a poor result because it sees many malware samples as never-seen-before. But, how it can be possible? In the AV-Comparatives tests, the samples are mostly a few weeks old, and in the AVLab tests a few days old.
Here is an example. Many in-the-wild attacks start the infection chain from non-EXE files. Trend Micro can prevent these files from delivering and executing the EXE payloads by using a kind of file reputation - the signature of the EXE payload is not created.
Most AVs (on default settings) often allow the initial non-EXE malware to deliver and execute the EXE payloads. Next, these AVs are forced to fight EXE payloads. Some payloads are blocked. But some others can compromise the system and then AVs will create signatures. So, if the EXE payloads are tested after a few days (weeks) then they will be easily detected by most AVs except Trend Micro.
Furthermore, Trend Micro can protect better because the payloads will not enter the system. In such a scenario Trend Micro can provide better protection and still will get poor detection.
So, the strange results of Trend Micro can be related to the below factors:
Another AV that can have a similar detection problem is Microsoft Defender. For example, It often uses extended protection against MS Office macros (via AMSI and ASR rules in the business environment). The difference is that Defender has found a way to add the signatures for EXE payloads (that never compromised the real machines) much faster than Trend Micro. So, it can get a good detection while testing a few weeks EXE samples (like in the AV-Comparatives tests). But still, the clear difference can be seen in some AVLabs tests for a few days EXE samples, for example:
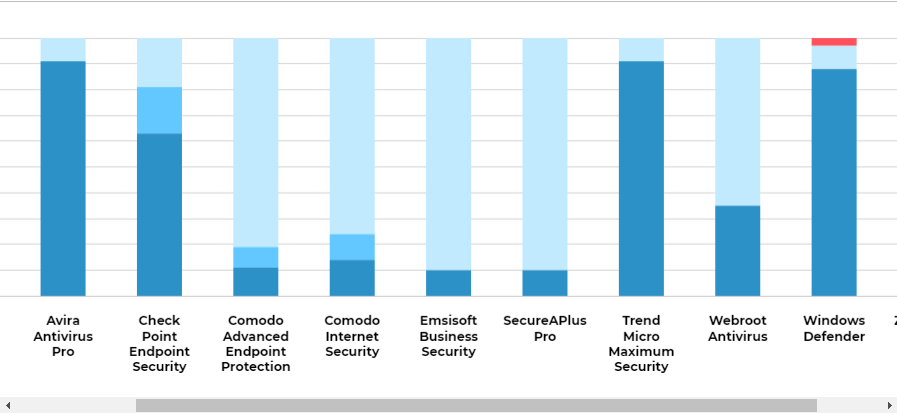
In this AVLab test from March 2020, the Defender scored 97% and all other AVs scored 100%.
The reason is similar to the case of Trend Micro. In many cases, the malicious attacks are blocked by AMSI and ASR rules + some other features, and Defender does not have to fight so many EXE payloads. The users are well protected in-the-wild, but the detection in some tests can be still worse as compared to other AVs. Of course, such detections have nothing to do with the protection in-the-wild.
The above chart comes from the AV-Comparatives Malware Protection test (September 2020, over 10000 samples tested). We can see the extremely poor result for Trend Micro.
Similar results can be seen in the AV_Comparatives test from March 2020 and in the test made by AVLab in May 2020 (over 1000 samples tested):
The test from AVLab is even more striking because all other AVs scored 100% detection (Trend Micro scored only 89%). I think that most people would quickly reach one of the below conclusions:
- Trend Micro is crap.
- The tests are unreliable.
- Trend Micro can provide better protection than many tested AVs and still get such poor detection results.
- The tests are correct (within the limits of testing procedures).
The first observation is that these results look like all tested AVs already knew the malware samples except Trend Micro. If so, then Trend Micro will get a poor result because it sees many malware samples as never-seen-before. But, how it can be possible? In the AV-Comparatives tests, the samples are mostly a few weeks old, and in the AVLab tests a few days old.
Here is an example. Many in-the-wild attacks start the infection chain from non-EXE files. Trend Micro can prevent these files from delivering and executing the EXE payloads by using a kind of file reputation - the signature of the EXE payload is not created.
Most AVs (on default settings) often allow the initial non-EXE malware to deliver and execute the EXE payloads. Next, these AVs are forced to fight EXE payloads. Some payloads are blocked. But some others can compromise the system and then AVs will create signatures. So, if the EXE payloads are tested after a few days (weeks) then they will be easily detected by most AVs except Trend Micro.
Furthermore, Trend Micro can protect better because the payloads will not enter the system. In such a scenario Trend Micro can provide better protection and still will get poor detection.
So, the strange results of Trend Micro can be related to the below factors:
- Most malware attacks do not start from EXE files.
- In Malware Protection tests the samples are mostly the EXE files.
- Some AVs have features that can prevent the initial non-EXE malware from delivering & executing the EXE payload (the signature is not created). These AVs can provide very good protection and still get poor detection in Malware Protection tests.
Another AV that can have a similar detection problem is Microsoft Defender. For example, It often uses extended protection against MS Office macros (via AMSI and ASR rules in the business environment). The difference is that Defender has found a way to add the signatures for EXE payloads (that never compromised the real machines) much faster than Trend Micro. So, it can get a good detection while testing a few weeks EXE samples (like in the AV-Comparatives tests). But still, the clear difference can be seen in some AVLabs tests for a few days EXE samples, for example:
In this AVLab test from March 2020, the Defender scored 97% and all other AVs scored 100%.
The reason is similar to the case of Trend Micro. In many cases, the malicious attacks are blocked by AMSI and ASR rules + some other features, and Defender does not have to fight so many EXE payloads. The users are well protected in-the-wild, but the detection in some tests can be still worse as compared to other AVs. Of course, such detections have nothing to do with the protection in-the-wild.
Last edited: