omidomi
Level 71
Thread author
Verified
Honorary Member
Top Poster
Malware Hunter
Well-known
Forum Veteran
- Content source
- http://news.drweb.com/show/?i=10003&lng=en&c=9
Among today’s malware programs, we can mention a category of so called “fileless” Trojans. Their key feature lies in the fact that their payload is located not in a file but directly in the computer’s memory. Necessary files needed for their operation are stored in various containers—for example, the Windows system registry. In this paper, Doctor Web is going to focus on one of their representatives, which was named Trojan.Kovter.297.
Trojan.Kovter is known to be spread by another malicious application—Trojan.MulDrop6.42771 that is specially designed to install malware on computers. These associated Trojans are detected by Dr.Web Anti-virus as Trojan.Kovter.297. Simple though it may seem, Trojan.MulDrop6.42771 has a quite sophisticated architecture. Its code contains a lot of random lines and function calls, which makes it harder to analyze the Trojan, and its library is hidden among resources of Trojan.MulDrop6.42771 in the form of an image. The Trojan can determine whether virtual machines or other debugging tools, which security researchers use to examine malware samples, are running. If it finds any, it immediately terminates itself. Besides, it can show random text messages on the screen and disable the Windows user accounts control (UAC).
Trojan.MulDrop6.42771 uses seven different ways to enable its autorun in the system and can implement six different methods to launch itself—how the Trojan will be launched is stipulated in its configuration file. Besides, the malware application can copy itself to root folders of all connected drives and create the autorun.inf file, spreading itself like a worm.
As we have mentioned before, some samples of Trojan.MulDrop6.42771 are found to contain Trojan.Kovter, a fileless Trojan. As a rule, it is run by Trojan.MulDrop6.42771; yet, it has its own autorun mechanism. The malicious program creates several entries in system registry: the fist one is the Trojan’s body, the second—a script necessary for its decryption and loading to the computer’s memory. Names of these entries contain unreadable characters—thus, they cannot be displayed by the regedit program.
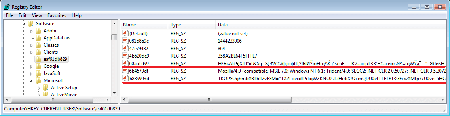
It turns out that Trojan.Kovter operates in the computer’s memory without copying itself on the disk in order to remain on the system as long as possible. Trojan.Kovter can be labeled as an adware Trojan because it runs several windows of Microsoft Internet Explorer simultaneously, visits websites specified by virus makers and generates traffic for them by following advertising links and banners. Therefore, attackers make money on affiliate programs and advertisers.
Despite the fact that Trojan.Kovter tries to hide its activity, Dr.Web Anti-virus successfully detects and removes the Trojan. We strongly recommend our users to timely update virus databases and regularly run scanning of the system if you think that your computer might be infected.
Trojan.Kovter is known to be spread by another malicious application—Trojan.MulDrop6.42771 that is specially designed to install malware on computers. These associated Trojans are detected by Dr.Web Anti-virus as Trojan.Kovter.297. Simple though it may seem, Trojan.MulDrop6.42771 has a quite sophisticated architecture. Its code contains a lot of random lines and function calls, which makes it harder to analyze the Trojan, and its library is hidden among resources of Trojan.MulDrop6.42771 in the form of an image. The Trojan can determine whether virtual machines or other debugging tools, which security researchers use to examine malware samples, are running. If it finds any, it immediately terminates itself. Besides, it can show random text messages on the screen and disable the Windows user accounts control (UAC).
Trojan.MulDrop6.42771 uses seven different ways to enable its autorun in the system and can implement six different methods to launch itself—how the Trojan will be launched is stipulated in its configuration file. Besides, the malware application can copy itself to root folders of all connected drives and create the autorun.inf file, spreading itself like a worm.
As we have mentioned before, some samples of Trojan.MulDrop6.42771 are found to contain Trojan.Kovter, a fileless Trojan. As a rule, it is run by Trojan.MulDrop6.42771; yet, it has its own autorun mechanism. The malicious program creates several entries in system registry: the fist one is the Trojan’s body, the second—a script necessary for its decryption and loading to the computer’s memory. Names of these entries contain unreadable characters—thus, they cannot be displayed by the regedit program.

It turns out that Trojan.Kovter operates in the computer’s memory without copying itself on the disk in order to remain on the system as long as possible. Trojan.Kovter can be labeled as an adware Trojan because it runs several windows of Microsoft Internet Explorer simultaneously, visits websites specified by virus makers and generates traffic for them by following advertising links and banners. Therefore, attackers make money on affiliate programs and advertisers.
Despite the fact that Trojan.Kovter tries to hide its activity, Dr.Web Anti-virus successfully detects and removes the Trojan. We strongly recommend our users to timely update virus databases and regularly run scanning of the system if you think that your computer might be infected.