- Nov 15, 2016
- 867
Botnet Also Pushes Ransomware, Cryptocurrency, 'Virtual Kisses'
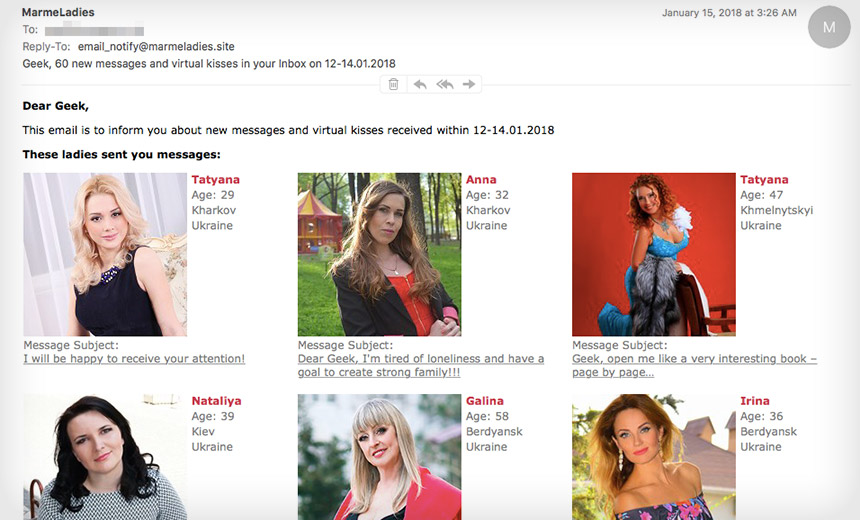
The Necurs botnet has recently been tied to Dridex malware phishing emails, dating site referrals (shown), cryptocurrency pumping schemes and more. (Source: Cisco Talos)
The operators of the venerable Necurs botnet appear to be up to their old tricks, including targeting victims with a variety of phishing campaigns designed to infect them with banking malware, ransomware and cryptocurrency fever as well as to generate profits via dating website referrals (see Necurs Botnet Shifts from Ransomware to Pump-and-Dump Scam).
See Also: Effective Cyber Threat Hunting Requires an Actor and Incident Centric Approach
Information security and law enforcement experts say that ransomware attacks are continuing to increase at a serious rate, leaving all other attacks behind (see 10 Cybersecurity Trends: What to Expect in 2018).
But criminals aren't betting the house on ransomware alone.
On Wednesday, for example, security researchers saw a "peculiar" new malicious email campaign launch and run for about seven hours; it attempted to infect endpoints with a variant of the Dridex banking Trojan.
The malware is primarily designed to target customers of U.S. and European banks. If it successfully infects a system, Dridex goes into hibernation until a user visits a specified website, then uses web injections and redirects to fake webpages to trick users into thinking they're logging into a legitimate site. In reality, however, attackers are likely intercepting their credentials and using them to drain accounts.
This latest Dridex campaign, however, differs from what's been seen before. "The campaign used compromised FTP sites instead of the more usual HTTP link as download locations for malicious documents, exposing the credentials of the compromised FTP sites in the process," say Roland Dela Paz and Ran Mosessco, both security researchers at Austin, Texas-based Forcepoint Security Labs, which is part of U.S. defense contractor Raytheon. The use of FTP sites for distributing attack code remains unusual, they add.
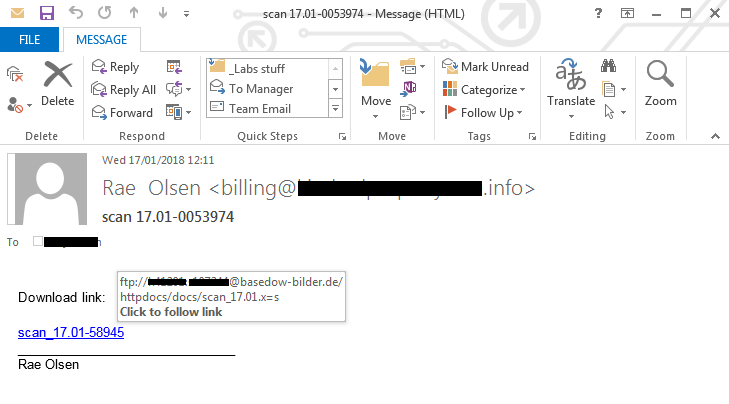
Malicious email sent by Necurs as part of Dridex campaign. (Source: Forcepoint)
Individuals in France appear to have been most targeted by this campaign. "The emails were sent primarily to .com top level domains with the second, third and fourth [most] affected TLDs suggesting that major regional targets were France, the U.K. and Australia respectively," they say in a blog post.
Malicious Office Files
The Forcepoint researchers say attackers sent malicious documents in one of two file types:
Attackers appear to be burning the FTP sites they're using, which suggests that they are legitimate resources that attackers are abusing. Using FTP sites is potentially a way to bypass "email gateways and network policies that may consider FTPs as trusted locations," the Forcepoint researchers say.
- Microsoft Word: A Word document - .doc file - designed to abuse DDE, a linking feature first built into Windows in 1987. Warnings about DDE as a potential entry point into enterprise networks for hackers first began appearing last March (see Locky Ransomware Spam Infects via Microsoft Office).
- Microsoft Excel: An Excel spreadsheet - .xls - includes a macro designed to download Dridex via an external site. Because macros are disabled by default in Office, due to the security risk they pose, many attackers use social engineering to attempt to trick recipients into enabling macros (see Hello! Can You Please Enable Macros?).
It's not clear how attackers have gained access to the FTP servers, but they potentially exploited servers running with default or weak credentials or else purchased lists of FTP server access credentials on darknet marketplaces (see Hackers Exploit Weak Remote Desktop Protocol Credentials).
"The presence of FTP credentials in the emails highlights the importance of regularly updating passwords: a compromised account may be abused multiple times by different actors as long as the credentials remain the same," the researchers say.
Necurs Connection
The attack appears to be coming from the Necurs botnet, given that some of the malware distribution domains were seen in previous Necurs attacks and that the downloaders and download locations for some files parallel ones previously used by the botnet. Necurs has also been tied to previous Dridex distribution.
Oddly, however, "the volume of this particular campaign is very low compared to typical Necurs campaigns," the researchers say. "Necurs typically sends out millions of emails per campaign, while this campaign was recorded sending just over 9,500 emails in total."
Necurs Botnet: Spam Cannon
But low-volume attacks tied to Necurs are not unusual. So say researchers at security firm Cisco Talos, who have studied 32 spam campaigns sent by Necurs from August to November of last year, amounting to more than 2.1 million spam messages, originating from nearly 1.2 million distinct sending IP addresses based in more than 200 different countries and territories.
"Necurs sends so much spam that at times Necurs' spam campaigns can make up more than 90 percent of the spam" seen by Cisco Talos in one day, says Jaeson Schultz, a technical leader for Cisco's Talos Security Intelligence & Research Group, in a blog post.
Cisco Talos found that Necurs tends to send high-volume campaigns on weekdays and low-volume, continuous campaigns on weekends, each targeted at different victims. "The mailing list database Necurs is using seems to be segmented, such that the high-volume campaigns use one subset of email addresses from the DB, and the low-volume campaigns use a different set of email addresses," Cisco Talos says.
Cryptocurrency Scam
Furthermore, phishing emails pushing Dridex would represent only a fraction of typical Necurs-promulgated attack traffic. In recent days, for example, the botnet appears to have been sending spam designed to entice email recipients into purchasing obscure cryptocurrency called Swisscoin, aka SIC, apparently as part of a pump-and-dump scheme, says Paul Burbage, a malware researcher at New York threat intelligence firm Flashpoint.


https://twitter.com/hexlax/status/952363412851486720
Paul Burbage@hexlax
Strange - #necurs #spambots now doing massive campaign coming from DGA seeds 5 & 9. Spam urging recipients to buy Swisscoin (SIC) on coinexchange[.]io. Could this be the start of a new trend for digital currency pump N dump?
9:15 PM - Jan 13, 2018
Twitter Ads info and privacy
But that accounts for just a fraction of what the botnet will be pumping out on any given day, researchers say. Other Necurs campaigns have included attempts to steal email recipients' cryptocurrency wallet access credentials, send them to dating sites, push penny stocks as well as trick them into installing ransomware - often Locky (see Phisher Refrain: We Will Crypto-Lock You).
Unfortunately for victims, even the dating site is a scam, Burbage tells Information Security Media Group.
https://twitter.com/hexlax/status/955470703452737536
Paul Burbage@hexlax
Replying to @euroinfosec and 4 others
Marme Ladies, like USSR-Star[.]net is an affiliated dating site. Affiliates get a percentage of profits from suckers purchasing credits to communicate with fake profiles. pic.twitter.com/Fg9lcDwkNk
11:02 AM - Jan 22, 2018
Twitter Ads info and privacy
And that's not all that attackers are skimping on. "Most of the time, very little investment is made in the design of the messages themselves," Schultz at Cisco Talos says, adding that these Locky infections can also be traced to Necurs because metadata in malware code references the affiliate ID - "Affid=3" - tied to the Necurs botnet.
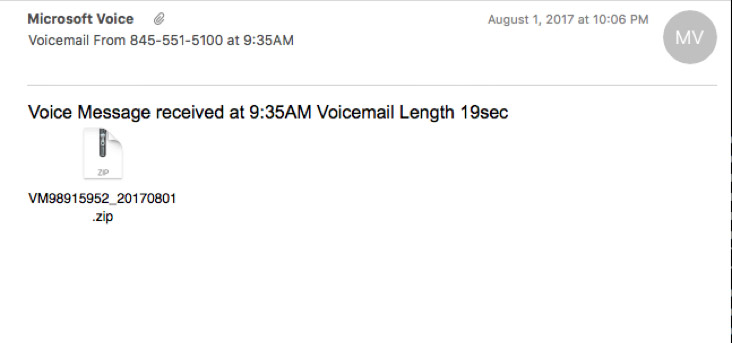
A typical ransomware campaign email from Necurs features almost no design effort. (Source: Cisco Talos)
"Necurs is responsible for emailing massive amounts of banking malware, ransomware, dating spam, pump-n-dump stock scams, work from home schemes and even cryptocurrency wallet credential phishing," Schultz says. At times, Necurs-promulgated spam accounts for 90 percent of all the spam seen in a day, he adds.
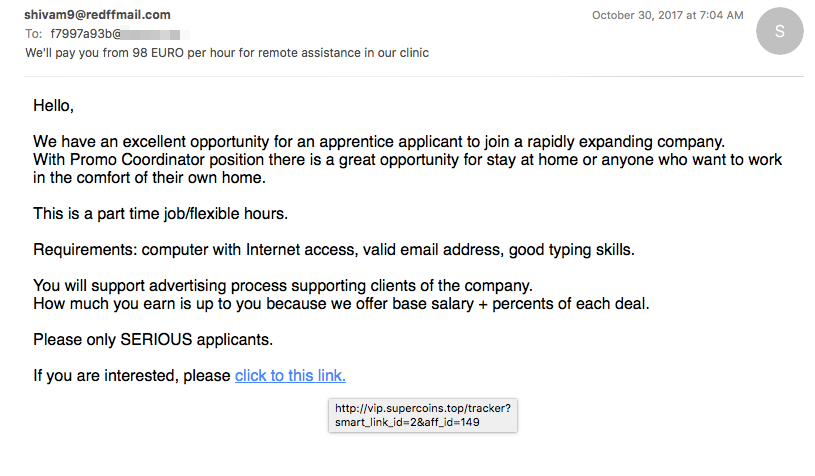
Email recently sent by Necurs as part of a low-volume, job-related spam campaign. (Source: Cisco Talos)
Auto-Generated Email Targets
Many of the recipient email addresses targeted by Necurs are auto-generated, with the addresses conforming to Project Honeypot's list of the Top Dictionary Attacker Usernames, "though it is unclear whether Necurs obtained their aliases from this list, or whether these aliases made Project Honeypot's list as a result of Necurs' spamming activity," Schultz says.
Top Usernames Guessed by Spammers
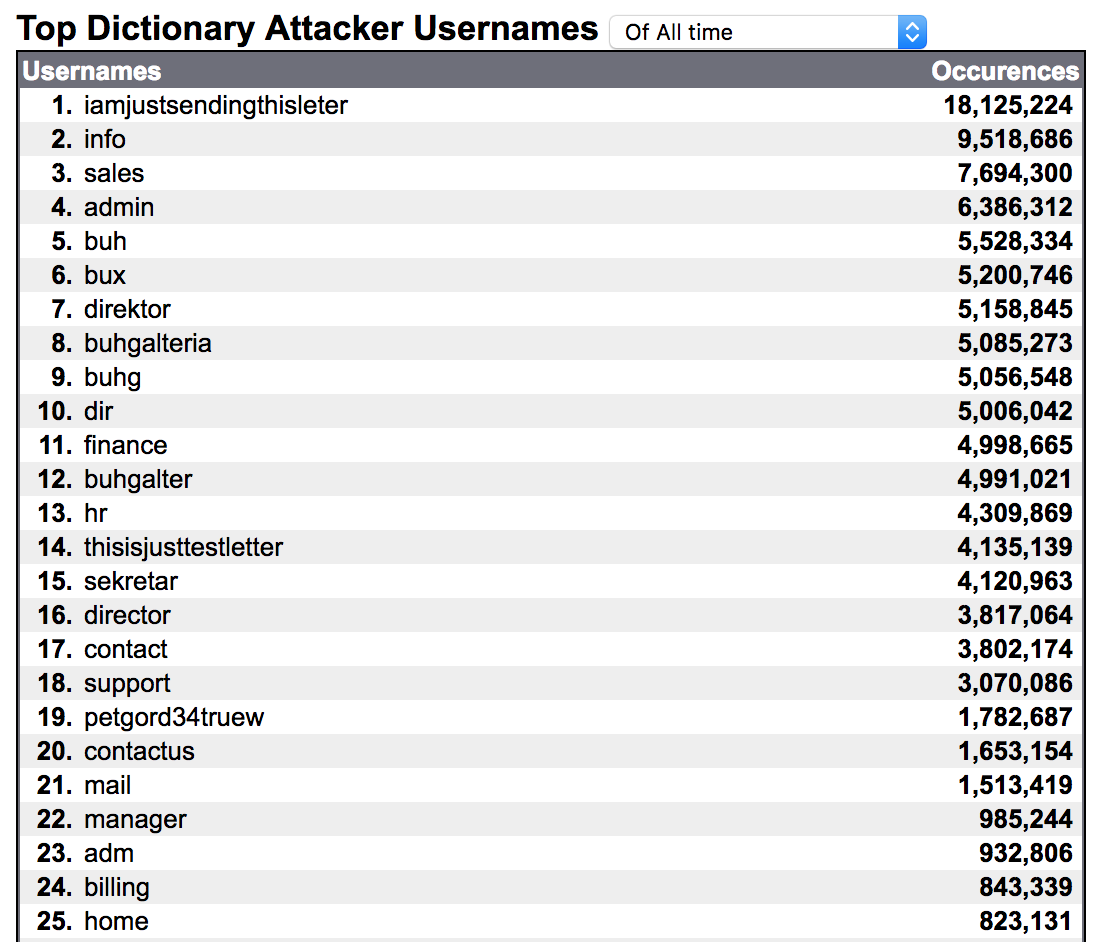
Top dictionary attacker usernames targeted by internet robots and the spammers. (Source: Project Honey Pot)
During the time period studied, 26 percent of all spam came from IP addresses based in India - presumably from malware-infected endpoints - followed by Vietnam at 20 percent and Iran at 7 percent, Cisco Talos says.
Of course, the attacking domains can be blacklisted. But Schultz says very little of the Necurs attack infrastructure appears to get reused. "This means that Necurs botnet is large enough to conduct attacks over several months without substantial reuse of most sending nodes - an impressive feat," he says.