L
LabZero
Thread author
Test performed on Windows 7 Pro SP1 x64.
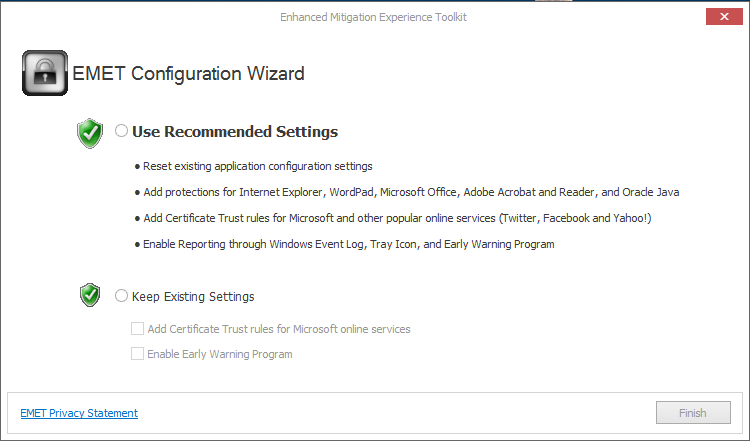
As you can see, select "Use recommended settings", EMET automatically configures even programs like Adobe Acrobat, Adobe Reader and Java so that use DEP, ASLR and other security technologies offered by the operating system.
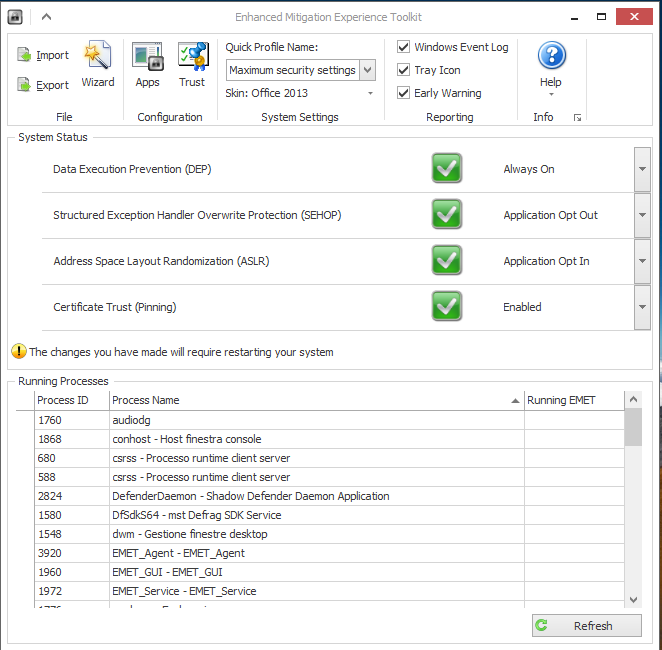
By clicking on "Apps", you can check which installed applications are using or will use, just running, the security features of Windows:
Thanks for reading.
As you can see, select "Use recommended settings", EMET automatically configures even programs like Adobe Acrobat, Adobe Reader and Java so that use DEP, ASLR and other security technologies offered by the operating system.
By clicking on "Apps", you can check which installed applications are using or will use, just running, the security features of Windows:
Thanks for reading.