Gandalf_The_Grey
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
- Apr 24, 2016
- 7,871
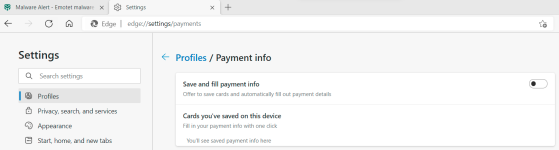
The Emotet botnet is now attempting to infect potential victims with a credit card stealer module designed to harvest credit card information stored in Google Chrome user profiles.
After stealing the credit card info (i.e., name, expiration month and year, card numbers), the malware will send it to command-and-control (C2) servers different than the ones the Emotet card stealer module.
"On June 6th, Proofpoint observed a new #Emotet module being dropped by the E4 botnet," the Proofpoint Threat Insights team revealed.
"To our surprise it was a credit card stealer that was solely targeting the Chrome browser. Once card details were collected they were exfiltrated to different C2 servers than the module loader."
This behavior change comes after increasing activity during April and a switch to 64-bit modules, as the Cryptolaemus security research group spotted.
One week later, Emotet started using Windows shortcut files (.LNK) to execute PowerShell commands to infect victims' devices, moving away from Microsoft Office macros now disabled by default starting with early April 2022.