Nice testing. Yes post that on their forum. They would ask you to provide your samples and make their case after testing.Good point! I'll make an account there and see if I can learn more about their behavior blocking.
I am impressed with their static scanning though. Seems very low on false positives but identifies variants well. I just had an hour before work to start gaining my first impressions on the suite as a whole.
Eset 13.0.22.0 Final
- Thread starter SpectraShadow83
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Did you managed to post your results in the forum?Good point! I'll make an account there and see if I can learn more about their behavior blocking.
I am impressed with their static scanning though. Seems very low on false positives but identifies variants well. I just had an hour before work to start gaining my first impressions on the suite as a whole.
Did you managed to post your results in the forum?
Tried to create an account twice this morning with Chrome; got through the CAPTCHA and then ended up at a page saying "Sorry you need to fill in all the fields". Then signing up again with the same email says the email has already been taken. Seems like there's something going on with the registration form at the moment. Will try again later this weekend when I get more time.
Finally got through. Posting one sample at a time so we can get some explanations piecewise....
Trying to get HIPS / Antiransomware to trigger on generic samples (pending moderation)
EDIT: Got a response basically saying it's not real ransomware therefore not detected and that it's unethical to create real ransomware.
In other words, ESET does not have a behavior blocker for zero-days the way that most other AV's do. Honestly I'm not thrilled with that response but it does match my testing results. Personally I would rather pair it with an actual behavior blocker.
Trying to get HIPS / Antiransomware to trigger on generic samples (pending moderation)
EDIT: Got a response basically saying it's not real ransomware therefore not detected and that it's unethical to create real ransomware.
In other words, ESET does not have a behavior blocker for zero-days the way that most other AV's do. Honestly I'm not thrilled with that response but it does match my testing results. Personally I would rather pair it with an actual behavior blocker.
Last edited:
Sadly that's a typical response from them. Like I said in a previous comment that they often prioritize false positives over detection and this is one of that example. But in a way their logic for not detecting simulation is understandable too.Finally got through. Posting one sample at a time so we can get some explanations piecewise....
Trying to get HIPS / Antiransomware to trigger on generic samples (pending moderation)
EDIT: Got a response basically saying it's not real ransomware therefore not detected and that it's unethical to create real ransomware.
In other words, ESET does not have a behavior blocker for zero-days the way that most other AV's do. Honestly I'm not thrilled with that response but it does match my testing results. Personally I would rather pair it with an actual behavior blocker.
Can you please check the same with Kaspersky? If Kaspersky lets you encrypt files only then I would agree with ESET. Kaspersky's System Watcher is the best behavior blocker there is so try testing it if you can.
Sadly that's a typical response from them. Like I said in a previous comment that they often prioritize false positives over detection and this is one of that example. But in a way their logic for not detecting simulation is understandable too.
Can you please check the same with Kaspersky? If Kaspersky lets you encrypt files only then I would agree with ESET. Kaspersky's System Watcher is the best behavior blocker there is so try testing it if you can.
I will try that next. I wrote another relocate-and-add-to-startup variant and Emsi and F-Secure both block it. So far those two are tied in my testing. Norton actually isn't doing a great job at behavior blocking. SONAR sometimes flags these binaries when delivered via a web browser (simply as low reputation under Aggressive) and deleting user documents triggers it, but the other sketchy behavior like downloading+executing a secondary payload or moving itself to a randomly generated temp file name and then registering as startup item is less likely to trigger Norton.
EDIT: Honestly I'm okay with ESET's response. They have their reasons of not making a general behavior blocker. Just customers need to understand that despite their advertising about "deep behavior" blocking and HIPS being automatic, in reality those components don't really react to zero days quite the same way that other BB's do.
Can you please check the same with Kaspersky? If Kaspersky lets you encrypt files only then I would agree with ESET. Kaspersky's System Watcher is the best behavior blocker there is so try testing it if you can.
Seems like KSW also allows the zipping and deletion of files in documents too. It also allows my binary that replicates itself to a random temp directory and registers itself to run at startup via the registry.
I'm going to play around a bit more with KSW to see what behaviors it triggers on... I am a bit surprised here too.
Interesting to know that about SONAR.I will try that next. I wrote another relocate-and-add-to-startup variant and Emsi and F-Secure both block it. So far those two are tied in my testing. Norton actually isn't doing a great job at behavior blocking. SONAR sometimes flags these binaries when delivered via a web browser (simply as low reputation under Aggressive) and deleting user documents triggers it, but the other sketchy behavior like downloading+executing a secondary payload or moving itself to a randomly generated temp file name and then registering as startup item is less likely to trigger Norton.
EDIT: Honestly I'm okay with ESET's response. They have their reasons of not making a general behavior blocker. Just customers need to understand that despite their advertising about "deep behavior" blocking and HIPS being automatic, in reality those components don't really react to zero days quite the same way that other BB's do.
Yes, I understand ESET's point of view. Detecting all those things would result in a great amount of false positives. In my personal experience Emsisoft's behavior blocker annoyed me a lot with false positives that's why I stopped using it but I have a license for it so might try again later. I also saw ESET's ransomware shield and Deep behavior shield in action once while testing malware packs on the hub so it's not like they're completely useless.
So it seems like ESET, Kaspersky don't react to such simulations as well. Keep posted.Seems like KSW also allows the zipping and deletion of files in documents too. It also allows my binary that replicates itself to a random temp directory and registers itself to run at startup via the registry.
I'm going to play around a bit more with KSW to see what behaviors it triggers on... I am a bit surprised here too.
File by file, KIS complained too about it and even offered to roll back the changes that the app did!
Meanwhile in ESET-land.....
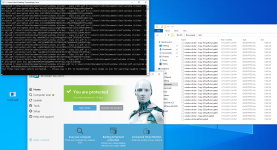
At this point I don't know how much more blatantly ransomware-y this could get. This is pretty much what ransomware fundamentally does.
(F-Secure calls it Trojan:W32/CryptoRansomwareBehavior.B!DeepGuard, leaves behind 1 .encrypted file, but was blocked from deleting the original copy... Even if I disable the "Ransomware Protection" or remove My Documents from the protected directories list, DeepGuard still triggers, suggesting it's more than just blocking any access to My Documents)

Meanwhile in ESET-land.....

At this point I don't know how much more blatantly ransomware-y this could get. This is pretty much what ransomware fundamentally does.
(F-Secure calls it Trojan:W32/CryptoRansomwareBehavior.B!DeepGuard, leaves behind 1 .encrypted file, but was blocked from deleting the original copy... Even if I disable the "Ransomware Protection" or remove My Documents from the protected directories list, DeepGuard still triggers, suggesting it's more than just blocking any access to My Documents)
Last edited:
Yeah to be clear I expect that an actual in the wild variant of an existing form of ransomware will probably get caught by ESET. Their static scanner is excellent at finding variants of things they have signatures for.You probably would need to find an actual ransomware sample on the wild...
My testing here is just on the scope of a true zero-day, something that nobody would have signatures for since I made the executable 5 minutes ago as if I were a for-hire malware writer to target an individual. It's purely meant as a behavior blocker test for antimalware solutions that claim to have a behavior blocker component. I'm not even going to claim that AV's that ace this test provide better protection -- I don't know enough to say that.
Just as a software engineer, behavior blockers are particularly interesting to me as a test target since it's relatively simple to whip up a program that pretends to do something bad.
I just read through this. In relation to ransomware, I'll quote this portion:
This technology monitors and evaluates all executed applications using behavioral and reputationbased heuristics. Whenever a behavior that resembles ransomware is identified or the potential malware tries to make unwanted modifications to existing files (i.e. to encrypt them), our feature notifies user who can block the activity. Ransomware Shield is finetuned to offer the highest possible level of ransomware protection together with other ESET technologies including Cloud Malware Protection System, Network Attack Protection and DNA Detections.
Honestly, this is similar to the language used in the DeepGuard whitepaper or Bitdefender antiransomware description, and based off that, I really would expect that home-cooked ransomware should trigger this too since it doesn't have reputation and it is making unwanted modifications.
I mean none of this negates all the other great things about ESET. It's lightweight, has a great heuristic scanner, and the developers seem very responsive! Its performance in the Malware Hub has been excellent. I'll keep testing it as time goes on, just in case this is some fluke of the brand new 13.0 version.
I just read through this. In relation to ransomware, I'll quote this portion:
Honestly, this is similar to the language used in the DeepGuard whitepaper or Bitdefender antiransomware description, and based off that, I really would expect that home-cooked ransomware should trigger this too since it doesn't have reputation and it is making unwanted modifications.
I mean none of this negates all the other great things about ESET. It's lightweight, has a great heuristic scanner, and the developers seem very responsive! Its performance in the Malware Hub has been excellent. I'll keep testing it as time goes on, just in case this is some fluke of the brand new 13.0 version.
In my experience features described in a paper placed on a manufacturers website aren't at all indicative of real world performance.
I would agree. That’s why I like to test things or look at test results rather than marketing materials. It’s still fun to read these whitepapers though but yeah what ends up being practical and enabled can be very different.In my experience features described in a paper placed on a manufacturers website aren't at all indicative of real world performance.
MacDefender So, like you said, ESET is able find unknown variants of malware that they already have signatures for but if it's something brand new it doesn't detect that. I expected at least something from the newly implemented ML/Augur but nothing from that either. ESET is great the way it is but behavior blocking has never been really a feature of ESET and that's still the same.
Anyway excellent testing. Can you check Windows Defender next? Most people use Windows Defender nowadays and it would be interesting to if it can detect such things. I think it would be better to test as many product as you can and create a separate thread and post your results there.
Anyway excellent testing. Can you check Windows Defender next? Most people use Windows Defender nowadays and it would be interesting to if it can detect such things. I think it would be better to test as many product as you can and create a separate thread and post your results there.
File by file, KIS complained too about it and even offered to roll back the changes that the app did!
View attachment 229574
Meanwhile in ESET-land.....
View attachment 229575
At this point I don't know how much more blatantly ransomware-y this could get. This is pretty much what ransomware fundamentally does.
(F-Secure calls it Trojan:W32/CryptoRansomwareBehavior.B!DeepGuard, leaves behind 1 .encrypted file, but was blocked from deleting the original copy... Even if I disable the "Ransomware Protection" or remove My Documents from the protected directories list, DeepGuard still triggers, suggesting it's more than just blocking any access to My Documents)
Does ESET have any setting to allow only executables cleared from its cloud ?
I'm thinking along the lines of WD's ASR rule: Block executable files from running unless they meet a prevalence age or trusted list criteria. This is not what you are testing for, as it would not help evaluate the BB, but would prevent the simulated malware to run.
Is it really or is this the ongoing myth about their software? Coz writing in assembly is incredibly inefficient for today's standards.
Time wise yes, but writing in assembly is still way more efficient today than using various compilers to do it for you (if you just know how). Of course, one must be well versed assembly programmer, but just cause there aren't many around doesn't mean there aren't any. Would be interesting to know though how much is true of ESET being mainly written in assembly.
You're comparing lightness with ram usage only which is wrong. There are many other parameters beside ram usage.
AV-Comparative does an excellent job at testing this. Check this: Performance Test April 2019
ESET is the lightest in their test as well so my and many other user's personal experience + this result surely verifies it.
Yep. I just don't get how people still mistakenly use RAM usage as reference to how light or heavy a program is. Its down to CPU and disk usage more than RAM usage. Few 10s of MB here and there mean absolutely nothing today. ESET uses extremely few resources. Just testing their internet security version out of curiosity and its considerably lighter than Windows Defender from my testing. Pretty impressive I must say, I might end up using ESET for longer period of time simply due to its lightness.
German magazine PC-Welt hands out trial licenses to its readers:

 www.eset.com
Code: PCWESET2019
www.eset.com
Code: PCWESET2019
120 day keys
The license expires from the moment of activation.

DACH
Sichern Sie Ihre digitale Welt mit unserem umfassenden Virenschutz. ESET Antivirus ist die perfekte Sicherheitssoftware für Privatpersonen und Unternehmen.
120 day keys
The license expires from the moment of activation.
You may also like...
-
Serious Discussion TuxTalk - Eset Smart Security Premium Thread
- Started by TuxTalk
- Replies: 167
-
-
On Sale! ESET Home Security Essential: 1-Year Subscription $14.99
- Started by Brownie2019
- Replies: 1
-
On Sale! McAfee Total Protection 5-Device: 1-Year Subscription
- Started by Brownie2019
- Replies: 2