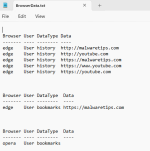
Possible Powershell Password Stealer I came across. Marked as clean via multiple online analysis sites but in the code it appears to take passwords and upload them to discord. Might be broken as multiple errors are displayed.
Could someone take a deeper look?
 www.hybrid-analysis.com
www.hybrid-analysis.com
 tria.ge
tria.ge
 opentip.kaspersky.com
opentip.kaspersky.com
Could someone take a deeper look?
Free Automated Malware Analysis Service - powered by Falcon Sandbox - Viewing online file analysis results for 'browserData.ps1'
Submit malware for free analysis with Falcon Sandbox and Hybrid Analysis technology. Hybrid Analysis develops and licenses analysis tools to fight malware.
Triage | Behavioral Report
Have a look at the Hatching Triage automated malware analysis report for this sample, with a score of 1 out of 10.
Kaspersky Threat Intelligence Portal
Kaspersky Threat Intelligence Portal allows you to scan files, domains, IP addresses, and URLs for threats, malware, viruses