- Apr 17, 2016
- 36
Understanding Angler Exploit Kit - Part 2: Examining Angler EK - Palo Alto Networks Blog
...In August 2014, Angler EK introduced a “fileless” infection technique to avoid detection by executing the payload from memory instead of storing it to disk. This technique is most often associated with Bedep payloads. Such fileless infections leave no artifacts from Bedep on the infected system’s disk. Fortunately, any post-infection activity usually leaves clues, since follow-up malware must be stored somewhere on the system in order to stay persistent and survive a reboot....
MY REMARK : "post-infection activity usually leaves clues" : i case of Cyptoxyz it leaves a lot of infected clues i am afraid ....
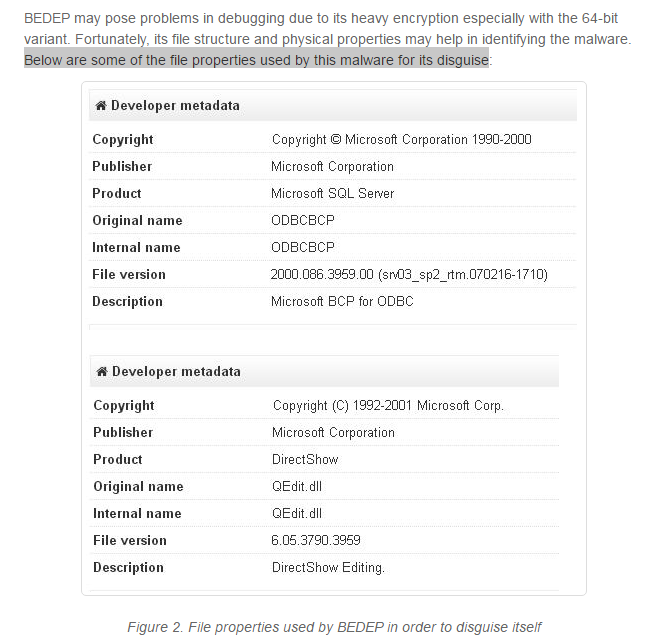
... For example, in June 2015 a previously unknown Flash vulnerability (later identified as CVE-2015-5119) was part of some 400 gigabytes of data dumped on the Internet as part of the infamous Hacking Team breach. A Flash exploit based on CVE-2015-5119 was integrated into Angler EK hours after the data dump was publicly available. It was a zero-day exploit at least 24 hours in the wild before Adobe issued a patch for it....
... By August 2015, Angler EK implemented an exploit for Internet Explorer (IE) vulnerability CVE-2015-2419 that Microsoft had patched the previous month....
...In August 2014, Angler EK introduced a “fileless” infection technique to avoid detection by executing the payload from memory instead of storing it to disk. This technique is most often associated with Bedep payloads. Such fileless infections leave no artifacts from Bedep on the infected system’s disk. Fortunately, any post-infection activity usually leaves clues, since follow-up malware must be stored somewhere on the system in order to stay persistent and survive a reboot....
MY REMARK : "post-infection activity usually leaves clues" : i case of Cyptoxyz it leaves a lot of infected clues i am afraid ....

... For example, in June 2015 a previously unknown Flash vulnerability (later identified as CVE-2015-5119) was part of some 400 gigabytes of data dumped on the Internet as part of the infamous Hacking Team breach. A Flash exploit based on CVE-2015-5119 was integrated into Angler EK hours after the data dump was publicly available. It was a zero-day exploit at least 24 hours in the wild before Adobe issued a patch for it....
... By August 2015, Angler EK implemented an exploit for Internet Explorer (IE) vulnerability CVE-2015-2419 that Microsoft had patched the previous month....
Last edited:
