- Oct 23, 2012
- 12,527
Be careful about streaming some of those sexytime videos online on your smartphone-- your device might just end up getting locked up and held hostage, but certainly not of the kinky sort.
According to cybersecurity company ESET, fake Pornhub apps are out to infect Android smartphones, locking users out from using them, and then demanding ransom money to set the phone free.
While Pornhub does indeed have an Android app, Google does not allow pornographic content to be hosted on the Play Store. This then led consumers of the service into looking for the app on the vast web, potentially falling into dangerous and malicious content one way or another.
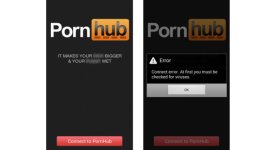
According to cybersecurity company ESET, fake Pornhub apps are out to infect Android smartphones, locking users out from using them, and then demanding ransom money to set the phone free.
While Pornhub does indeed have an Android app, Google does not allow pornographic content to be hosted on the Play Store. This then led consumers of the service into looking for the app on the vast web, potentially falling into dangerous and malicious content one way or another.

With the possibility of sideloading apps on Android, apps are made available via raw APK files. Since there is no official entry for Pornhub on the store, cybercriminals can easily cloak any app as the adult video service, inject malicious code, and then wait for unsuspecting victims to download the app.
If one of the rogue apps is installed, it will first say that it needs to check the phone for viruses before it can play any pornographic videos. However, during this process, it is silently installing a ransomware for Android, which will lock a user out of their device.

The lock screen demanding $100 to settle the case | via ESET
A "police ransomware" lock screen will be displayed subsequently, demanding that the victim pay $100 to be able to unlock the device. The message threatens to take legal action should the victim refuse to pay, but given that one of the lock screen messages has such bad grammar, as shown above, it can easily be seen that the legal issue is not legitimate.
To be able to rid the malware for good, ESET instructs victims to start their device in Safe mode, and then revoke the app's Device Administrator privileges. Once these steps are taken, those infected can now proceed with uninstalling the app through Settings. If all else fails, resetting the device to factory settings is still an option.
With these rogue software in consideration, it pays to stay away from third-party apps as much as possible. Exercise caution in sideloading APK files as well, as some might contain malware that can compromise you or your device's security.
Source: ESET (PDF) via The Next Web

