FBI MoneyPak Removal
- Thread starter Gerry
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Status
- Not open for further replies.
I had already decided to copy the items to a flash and just move them to the desk to run on the infected PC, just in case. I once had a virus that I thought I cleaned but as soon as IE started it would too.
My infected PC booted up OK!!! I got two warning messages that zutro and dxlat could not be found.
Ran the reg fix. and Combofix is running now. Will post the log afterwards.
I read on another webpage that I would have to change the options in IE to uncheck "use Proxy Server" with this virus. Would I still have to do that here.
My infected PC booted up OK!!! I got two warning messages that zutro and dxlat could not be found.
Ran the reg fix. and Combofix is running now. Will post the log afterwards.
I read on another webpage that I would have to change the options in IE to uncheck "use Proxy Server" with this virus. Would I still have to do that here.
Here is the Combofix Log
ComboFix 13-01-27.03 - Gerry 01/27/2013 9:23.1.2 - x86
Running from: c:\documents and settings\Gerry\Desktop\ComboFix.exe
* Created a new restore point
.
.
((((((((((((((((((((((((((((((((((((((( Other Deletions )))))))))))))))))))))))))))))))))))))))))))))))))
.
.
c:\documents and settings\All Users\Application Data\TEMP
c:\documents and settings\Gerry\Application Data\Ikysa
c:\documents and settings\Gerry\Application Data\Ikysa\zuaz.tim
c:\documents and settings\Gerry\My Documents\~WRL0493.tmp
c:\documents and settings\Gerry\My Documents\~WRL1070.tmp
c:\documents and settings\Gerry\WINDOWS
c:\windows\assembly\GAC\Desktop.ini
c:\windows\system32\11478.exe
c:\windows\system32\15724.exe
c:\windows\system32\19169.exe
c:\windows\system32\21328.exe
c:\windows\system32\26500.exe
c:\windows\system32\Cache
c:\windows\system32\Cache\272512937d9e61a4.fb
c:\windows\system32\Cache\287204568329e189.fb
c:\windows\system32\Cache\28bc8f716fd76a47.fb
c:\windows\system32\Cache\2c53092c95605355.fb
c:\windows\system32\Cache\35a21c7f198a4b72.fb
c:\windows\system32\Cache\3917078cb68ec657.fb
c:\windows\system32\Cache\590ba23ce359fd0c.fb
c:\windows\system32\Cache\610289e025a3ee9a.fb
c:\windows\system32\Cache\651c5d3cdbfb8bd1.fb
c:\windows\system32\Cache\6c59ac5e7e7a3ad0.fb
c:\windows\system32\Cache\a8556537add6dfc5.fb
c:\windows\system32\Cache\ad10a52aff5e038d.fb
c:\windows\system32\Cache\c4d28dca2e7648be.fb
c:\windows\system32\Cache\d201ef9910cd39de.fb
c:\windows\system32\Cache\d2e94710a5708128.fb
c:\windows\system32\Cache\d79b9dfe81484ec4.fb
c:\windows\system32\Cache\e0de16f883bea794.fb
c:\windows\system32\dds_trash_log.cmd
c:\windows\system32\drivers\npf.sys
c:\windows\system32\Packet.dll
c:\windows\system32\windrv.sys
c:\windows\system32\wpcap.dll
c:\windows\wininit.ini
.
.
((((((((((((((((((((((((((((((((((((((( Drivers/Services )))))))))))))))))))))))))))))))))))))))))))))))))
.
.
-------\Legacy_NPF
-------\Legacy_USNJSVC
-------\Service_.mrxsmb
-------\Service_NPF
-------\Service_usnjsvc
.
.
((((((((((((((((((((((((( Files Created from 2012-12-27 to 2013-01-27 )))))))))))))))))))))))))))))))
.
.
2013-01-27 02:05 . 2011-07-13 02:55 2237440 ----a-r- C:\OTLPE.exe
2013-01-27 01:56 . 2013-01-27 01:56 -------- d-----w- C:\_OTL
2013-01-26 22:34 . 2013-01-26 22:34 -------- d-----w- C:\FRST
2013-01-26 20:59 . 2013-01-26 22:11 -------- d-----w- C:\NBRT
2013-01-26 00:14 . 2013-01-26 00:14 40776 ----a-w- c:\windows\system32\drivers\mbamswissarmy.sys
2013-01-20 00:58 . 2013-01-20 00:58 697864 ----a-w- c:\windows\system32\FlashPlayerApp.exe
.
.
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2013-01-20 00:58 . 2011-06-19 23:54 74248 ----a-w- c:\windows\system32\FlashPlayerCPLApp.cpl
2012-12-16 12:23 . 2008-08-21 12:00 290560 ----a-w- c:\windows\system32\atmfd.dll
2012-12-15 00:49 . 2009-12-29 21:19 21104 ----a-w- c:\windows\system32\drivers\mbam.sys
2012-11-13 01:25 . 2008-08-21 12:00 1866368 ----a-w- c:\windows\system32\win32k.sys
2012-11-06 02:01 . 2008-08-21 12:00 1371648 ----a-w- c:\windows\system32\msxml6.dll
2012-11-02 02:02 . 2008-08-21 12:00 375296 ----a-w- c:\windows\system32\dpnet.dll
2012-11-01 12:17 . 2008-08-21 12:00 916992 ----a-w- c:\windows\system32\wininet.dll
2012-11-01 12:17 . 2008-08-21 12:00 43520 ------w- c:\windows\system32\licmgr10.dll
2012-11-01 12:17 . 2008-08-21 12:00 1469440 ------w- c:\windows\system32\inetcpl.cpl
2012-11-01 00:35 . 2008-08-21 12:00 385024 ------w- c:\windows\system32\html.iec
.
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
.
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"SpybotSD TeaTimer"="c:\program files\Spybot - Search & Destroy\TeaTimer.exe" [2009-03-06 2260480]
"Sony PC Companion"="c:\program files\Sony\Sony PC Companion\PCCompanion.exe" [2012-09-12 445624]
"AnyDVD"="c:\program files\DVD\AnyDVD\AnyDVDtray.exe" [2012-12-20 6750448]
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"QuickTime Task"="c:\program files\QuickTime\qttask.exe" [2009-11-11 417792]
"Adobe Reader Speed Launcher"="c:\program files\Adobe\Reader 9.0\Reader\Reader_sl.exe" [2012-12-19 41208]
"Adobe ARM"="c:\program files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" [2012-12-03 946352]
.
c:\documents and settings\Gerry\Start Menu\Programs\Startup\
KatMouse.lnk - c:\program files\KatMouse\KatMouse.exe [2007-5-30 50688]
.
c:\documents and settings\All Users\Start Menu\Programs\Startup\
Microsoft Office.lnk - c:\program files\Microsoft Office\Office\OSA9.EXE [1999-2-17 65588]
.
[HKEY_USERS\.default\software\microsoft\windows\currentversion\policies\explorer]
"NoSetActiveDesktop"= 1 (0x1)
.
[HKEY_LOCAL_MACHINE\system\currentcontrolset\control\session manager]
BootExecute REG_MULTI_SZ autocheck autochk *\0????????
.
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\hitmanpro37]
@=""
.
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\hitmanpro37.sys]
@=""
.
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\MSIServer]
@="Service"
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\Adobe ARM]
2012-12-03 07:35 946352 ----a-w- c:\program files\Common Files\Adobe\ARM\1.0\AdobeARM.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\Adobe Reader Speed Launcher]
2012-12-19 14:39 41208 ----a-w- c:\program files\Adobe\Reader 9.0\Reader\reader_sl.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\QuickTime Task]
2009-11-11 07:08 417792 ----a-w- c:\program files\QuickTime\QTTask.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\SunJavaUpdateSched]
2010-01-16 00:14 149280 ----a-w- c:\program files\Java\jre6\bin\jusched.exe
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List]
"%windir%\\system32\\sessmgr.exe"=
.
R3 ggflt;SEMC USB Flash Driver Filter;c:\windows\system32\DRIVERS\ggflt.sys [x]
R3 hitmanpro35;Hitman Pro 3.5 Support Driver;c:\windows\system32\drivers\hitmanpro36.sys [x]
R3 MBAMSwissArmy;MBAMSwissArmy;c:\windows\system32\drivers\mbamswissarmy.sys [x]
R3 s0016bus;Sony Ericsson Device 0016 driver (WDM);c:\windows\system32\DRIVERS\s0016bus.sys [x]
R3 s0016mdfl;Sony Ericsson Device 0016 USB WMC Modem Filter;c:\windows\system32\DRIVERS\s0016mdfl.sys [x]
R3 s0016mdm;Sony Ericsson Device 0016 USB WMC Modem Driver;c:\windows\system32\DRIVERS\s0016mdm.sys [x]
R3 s0016mgmt;Sony Ericsson Device 0016 USB WMC Device Management Drivers (WDM);c:\windows\system32\DRIVERS\s0016mgmt.sys [x]
R3 s0016nd5;Sony Ericsson Device 0016 USB Ethernet Emulation SEMC0016 (NDIS);c:\windows\system32\DRIVERS\s0016nd5.sys [x]
R3 s0016obex;Sony Ericsson Device 0016 USB WMC OBEX Interface;c:\windows\system32\DRIVERS\s0016obex.sys [x]
R3 s0016unic;Sony Ericsson Device 0016 USB Ethernet Emulation SEMC0016 (WDM);c:\windows\system32\DRIVERS\s0016unic.sys [x]
R3 Sony PC Companion;Sony PC Companion;c:\program files\Sony\Sony PC Companion\PCCService.exe [x]
S3 seehcri;Sony Ericsson seehcri Device Driver;c:\windows\system32\DRIVERS\seehcri.sys [x]
.
.
--- Other Services/Drivers In Memory ---
.
*NewlyCreated* - WUAUSERV
.
Contents of the 'Scheduled Tasks' folder
.
2010-03-30 c:\windows\Tasks\FRU Task 2003-04-06 08:52ewlett-Packard2003-04-06 08:52p psc 1200 series5E771253C1676EBED677BF361FDFC537825E15B8262045774.job
- c:\program files\Hewlett-Packard\Digital Imaging\Bin\hpqfrucl.exe [2003-04-06 05:52]
.
2013-01-27 c:\windows\Tasks\GoogleUpdateTaskMachineCore.job
- c:\program files\Google\Update\GoogleUpdate.exe [2010-01-13 19:50]
.
2013-01-26 c:\windows\Tasks\GoogleUpdateTaskMachineUA.job
- c:\program files\Google\Update\GoogleUpdate.exe [2010-01-13 19:50]
.
2013-01-27 c:\windows\Tasks\User_Feed_Synchronization-{4AE1076F-09C2-44D0-8AEA-647C5037DFD3}.job
- c:\windows\system32\msfeedssync.exe [2009-03-08 12:31]
.
.
------- Supplementary Scan -------
.
uStart Page = hxxp://www.bing.com/
uInternet Settings,ProxyOverride = <local>
TCP: DhcpNameServer = 192.168.1.1 4.2.2.2
.
- - - - ORPHANS REMOVED - - - -
.
WebBrowser-{FB0C9FD7-6768-4913-BD40-B4DD07D16AF2} - (no file)
HKLM-Run-zutro - c:\documents and settings\Gerry\Application Data\zutro.dll
HKLM-Run-dxlat - c:\documents and settings\Gerry\Application Data\dxlat.dll
SafeBoot-17240770.sys
SafeBoot-73432066.sys
SafeBoot-Wdf01000.sys
.
.
.
**************************************************************************
.
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net
Rootkit scan 2013-01-27 09:44
Windows 5.1.2600 Service Pack 3 NTFS
.
scanning hidden processes ...
.
scanning hidden autostart entries ...
.
scanning hidden files ...
.
scan completed successfully
hidden files: 0
.
**************************************************************************
.
--------------------- LOCKED REGISTRY KEYS ---------------------
.
[HKEY_LOCAL_MACHINE\software\Classes\CLSID\{73C9DFA0-750D-11E1-B0C4-0800200C9A66}]
@Denied: (A 2) (Everyone)
@="FlashBroker"
"LocalizedString"="@c:\\WINDOWS\\system32\\Macromed\\Flash\\FlashUtil32_11_5_502_146_ActiveX.exe,-101"
.
[HKEY_LOCAL_MACHINE\software\Classes\CLSID\{73C9DFA0-750D-11E1-B0C4-0800200C9A66}\Elevation]
"Enabled"=dword:00000001
.
[HKEY_LOCAL_MACHINE\software\Classes\CLSID\{73C9DFA0-750D-11E1-B0C4-0800200C9A66}\LocalServer32]
@="c:\\WINDOWS\\system32\\Macromed\\Flash\\FlashUtil32_11_5_502_146_ActiveX.exe"
.
[HKEY_LOCAL_MACHINE\software\Classes\CLSID\{73C9DFA0-750D-11E1-B0C4-0800200C9A66}\TypeLib]
@="{FAB3E735-69C7-453B-A446-B6823C6DF1C9}"
.
[HKEY_LOCAL_MACHINE\software\Classes\Interface\{6AE38AE0-750C-11E1-B0C4-0800200C9A66}]
@Denied: (A 2) (Everyone)
@="IFlashBroker5"
.
[HKEY_LOCAL_MACHINE\software\Classes\Interface\{6AE38AE0-750C-11E1-B0C4-0800200C9A66}\ProxyStubClsid32]
@="{00020424-0000-0000-C000-000000000046}"
.
[HKEY_LOCAL_MACHINE\software\Classes\Interface\{6AE38AE0-750C-11E1-B0C4-0800200C9A66}\TypeLib]
@="{FAB3E735-69C7-453B-A446-B6823C6DF1C9}"
"Version"="1.0"
.
--------------------- DLLs Loaded Under Running Processes ---------------------
.
- - - - - - - > 'explorer.exe'(4088)
c:\windows\system32\WININET.dll
c:\program files\DVD\AnyDVD\ADvdDiscHlp.dll
c:\program files\KatMouse\KatMouseS.dll
c:\windows\system32\ieframe.dll
c:\windows\system32\webcheck.dll
c:\windows\system32\WPDShServiceObj.dll
c:\windows\system32\PortableDeviceTypes.dll
c:\windows\system32\PortableDeviceApi.dll
.
------------------------ Other Running Processes ------------------------
.
c:\windows\system32\savedump.exe
c:\program files\Java\jre6\bin\jqs.exe
c:\program files\Yahoo!\SoftwareUpdate\YahooAUService.exe
c:\windows\system32\wscntfy.exe
.
**************************************************************************
.
Completion time: 2013-01-27 09:48:42 - machine was rebooted
ComboFix-quarantined-files.txt 2013-01-27 17:48
.
Pre-Run: 333,054,345,216 bytes free
Post-Run: 332,902,453,248 bytes free
.
WindowsXP-KB310994-SP2-Home-BootDisk-ENU.exe
[boot loader]
timeout=2
default=multi(0)disk(0)rdisk(0)partition(1)\WINDOWS
[operating systems]
c:\cmdcons\BOOTSECT.DAT="Microsoft Windows Recovery Console" /cmdcons
UnsupportedDebug="do not select this" /debug
multi(0)disk(0)rdisk(0)partition(1)\WINDOWS="Microsoft Windows XP Professional" /noexecute=optin /fastdetect
.
- - End Of File - - 5B7F2E6DA4C2B0AD95FECA86477A05F8
I read on another webpage that I would have to change the options in IE to uncheck "use Proxy Server" with this virus. Would I still have to do that now?
ComboFix 13-01-27.03 - Gerry 01/27/2013 9:23.1.2 - x86
Running from: c:\documents and settings\Gerry\Desktop\ComboFix.exe
* Created a new restore point
.
.
((((((((((((((((((((((((((((((((((((((( Other Deletions )))))))))))))))))))))))))))))))))))))))))))))))))
.
.
c:\documents and settings\All Users\Application Data\TEMP
c:\documents and settings\Gerry\Application Data\Ikysa
c:\documents and settings\Gerry\Application Data\Ikysa\zuaz.tim
c:\documents and settings\Gerry\My Documents\~WRL0493.tmp
c:\documents and settings\Gerry\My Documents\~WRL1070.tmp
c:\documents and settings\Gerry\WINDOWS
c:\windows\assembly\GAC\Desktop.ini
c:\windows\system32\11478.exe
c:\windows\system32\15724.exe
c:\windows\system32\19169.exe
c:\windows\system32\21328.exe
c:\windows\system32\26500.exe
c:\windows\system32\Cache
c:\windows\system32\Cache\272512937d9e61a4.fb
c:\windows\system32\Cache\287204568329e189.fb
c:\windows\system32\Cache\28bc8f716fd76a47.fb
c:\windows\system32\Cache\2c53092c95605355.fb
c:\windows\system32\Cache\35a21c7f198a4b72.fb
c:\windows\system32\Cache\3917078cb68ec657.fb
c:\windows\system32\Cache\590ba23ce359fd0c.fb
c:\windows\system32\Cache\610289e025a3ee9a.fb
c:\windows\system32\Cache\651c5d3cdbfb8bd1.fb
c:\windows\system32\Cache\6c59ac5e7e7a3ad0.fb
c:\windows\system32\Cache\a8556537add6dfc5.fb
c:\windows\system32\Cache\ad10a52aff5e038d.fb
c:\windows\system32\Cache\c4d28dca2e7648be.fb
c:\windows\system32\Cache\d201ef9910cd39de.fb
c:\windows\system32\Cache\d2e94710a5708128.fb
c:\windows\system32\Cache\d79b9dfe81484ec4.fb
c:\windows\system32\Cache\e0de16f883bea794.fb
c:\windows\system32\dds_trash_log.cmd
c:\windows\system32\drivers\npf.sys
c:\windows\system32\Packet.dll
c:\windows\system32\windrv.sys
c:\windows\system32\wpcap.dll
c:\windows\wininit.ini
.
.
((((((((((((((((((((((((((((((((((((((( Drivers/Services )))))))))))))))))))))))))))))))))))))))))))))))))
.
.
-------\Legacy_NPF
-------\Legacy_USNJSVC
-------\Service_.mrxsmb
-------\Service_NPF
-------\Service_usnjsvc
.
.
((((((((((((((((((((((((( Files Created from 2012-12-27 to 2013-01-27 )))))))))))))))))))))))))))))))
.
.
2013-01-27 02:05 . 2011-07-13 02:55 2237440 ----a-r- C:\OTLPE.exe
2013-01-27 01:56 . 2013-01-27 01:56 -------- d-----w- C:\_OTL
2013-01-26 22:34 . 2013-01-26 22:34 -------- d-----w- C:\FRST
2013-01-26 20:59 . 2013-01-26 22:11 -------- d-----w- C:\NBRT
2013-01-26 00:14 . 2013-01-26 00:14 40776 ----a-w- c:\windows\system32\drivers\mbamswissarmy.sys
2013-01-20 00:58 . 2013-01-20 00:58 697864 ----a-w- c:\windows\system32\FlashPlayerApp.exe
.
.
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2013-01-20 00:58 . 2011-06-19 23:54 74248 ----a-w- c:\windows\system32\FlashPlayerCPLApp.cpl
2012-12-16 12:23 . 2008-08-21 12:00 290560 ----a-w- c:\windows\system32\atmfd.dll
2012-12-15 00:49 . 2009-12-29 21:19 21104 ----a-w- c:\windows\system32\drivers\mbam.sys
2012-11-13 01:25 . 2008-08-21 12:00 1866368 ----a-w- c:\windows\system32\win32k.sys
2012-11-06 02:01 . 2008-08-21 12:00 1371648 ----a-w- c:\windows\system32\msxml6.dll
2012-11-02 02:02 . 2008-08-21 12:00 375296 ----a-w- c:\windows\system32\dpnet.dll
2012-11-01 12:17 . 2008-08-21 12:00 916992 ----a-w- c:\windows\system32\wininet.dll
2012-11-01 12:17 . 2008-08-21 12:00 43520 ------w- c:\windows\system32\licmgr10.dll
2012-11-01 12:17 . 2008-08-21 12:00 1469440 ------w- c:\windows\system32\inetcpl.cpl
2012-11-01 00:35 . 2008-08-21 12:00 385024 ------w- c:\windows\system32\html.iec
.
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
.
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"SpybotSD TeaTimer"="c:\program files\Spybot - Search & Destroy\TeaTimer.exe" [2009-03-06 2260480]
"Sony PC Companion"="c:\program files\Sony\Sony PC Companion\PCCompanion.exe" [2012-09-12 445624]
"AnyDVD"="c:\program files\DVD\AnyDVD\AnyDVDtray.exe" [2012-12-20 6750448]
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"QuickTime Task"="c:\program files\QuickTime\qttask.exe" [2009-11-11 417792]
"Adobe Reader Speed Launcher"="c:\program files\Adobe\Reader 9.0\Reader\Reader_sl.exe" [2012-12-19 41208]
"Adobe ARM"="c:\program files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" [2012-12-03 946352]
.
c:\documents and settings\Gerry\Start Menu\Programs\Startup\
KatMouse.lnk - c:\program files\KatMouse\KatMouse.exe [2007-5-30 50688]
.
c:\documents and settings\All Users\Start Menu\Programs\Startup\
Microsoft Office.lnk - c:\program files\Microsoft Office\Office\OSA9.EXE [1999-2-17 65588]
.
[HKEY_USERS\.default\software\microsoft\windows\currentversion\policies\explorer]
"NoSetActiveDesktop"= 1 (0x1)
.
[HKEY_LOCAL_MACHINE\system\currentcontrolset\control\session manager]
BootExecute REG_MULTI_SZ autocheck autochk *\0????????
.
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\hitmanpro37]
@=""
.
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\hitmanpro37.sys]
@=""
.
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\MSIServer]
@="Service"
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\Adobe ARM]
2012-12-03 07:35 946352 ----a-w- c:\program files\Common Files\Adobe\ARM\1.0\AdobeARM.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\Adobe Reader Speed Launcher]
2012-12-19 14:39 41208 ----a-w- c:\program files\Adobe\Reader 9.0\Reader\reader_sl.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\QuickTime Task]
2009-11-11 07:08 417792 ----a-w- c:\program files\QuickTime\QTTask.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\SunJavaUpdateSched]
2010-01-16 00:14 149280 ----a-w- c:\program files\Java\jre6\bin\jusched.exe
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List]
"%windir%\\system32\\sessmgr.exe"=
.
R3 ggflt;SEMC USB Flash Driver Filter;c:\windows\system32\DRIVERS\ggflt.sys [x]
R3 hitmanpro35;Hitman Pro 3.5 Support Driver;c:\windows\system32\drivers\hitmanpro36.sys [x]
R3 MBAMSwissArmy;MBAMSwissArmy;c:\windows\system32\drivers\mbamswissarmy.sys [x]
R3 s0016bus;Sony Ericsson Device 0016 driver (WDM);c:\windows\system32\DRIVERS\s0016bus.sys [x]
R3 s0016mdfl;Sony Ericsson Device 0016 USB WMC Modem Filter;c:\windows\system32\DRIVERS\s0016mdfl.sys [x]
R3 s0016mdm;Sony Ericsson Device 0016 USB WMC Modem Driver;c:\windows\system32\DRIVERS\s0016mdm.sys [x]
R3 s0016mgmt;Sony Ericsson Device 0016 USB WMC Device Management Drivers (WDM);c:\windows\system32\DRIVERS\s0016mgmt.sys [x]
R3 s0016nd5;Sony Ericsson Device 0016 USB Ethernet Emulation SEMC0016 (NDIS);c:\windows\system32\DRIVERS\s0016nd5.sys [x]
R3 s0016obex;Sony Ericsson Device 0016 USB WMC OBEX Interface;c:\windows\system32\DRIVERS\s0016obex.sys [x]
R3 s0016unic;Sony Ericsson Device 0016 USB Ethernet Emulation SEMC0016 (WDM);c:\windows\system32\DRIVERS\s0016unic.sys [x]
R3 Sony PC Companion;Sony PC Companion;c:\program files\Sony\Sony PC Companion\PCCService.exe [x]
S3 seehcri;Sony Ericsson seehcri Device Driver;c:\windows\system32\DRIVERS\seehcri.sys [x]
.
.
--- Other Services/Drivers In Memory ---
.
*NewlyCreated* - WUAUSERV
.
Contents of the 'Scheduled Tasks' folder
.
2010-03-30 c:\windows\Tasks\FRU Task 2003-04-06 08:52ewlett-Packard2003-04-06 08:52p psc 1200 series5E771253C1676EBED677BF361FDFC537825E15B8262045774.job
- c:\program files\Hewlett-Packard\Digital Imaging\Bin\hpqfrucl.exe [2003-04-06 05:52]
.
2013-01-27 c:\windows\Tasks\GoogleUpdateTaskMachineCore.job
- c:\program files\Google\Update\GoogleUpdate.exe [2010-01-13 19:50]
.
2013-01-26 c:\windows\Tasks\GoogleUpdateTaskMachineUA.job
- c:\program files\Google\Update\GoogleUpdate.exe [2010-01-13 19:50]
.
2013-01-27 c:\windows\Tasks\User_Feed_Synchronization-{4AE1076F-09C2-44D0-8AEA-647C5037DFD3}.job
- c:\windows\system32\msfeedssync.exe [2009-03-08 12:31]
.
.
------- Supplementary Scan -------
.
uStart Page = hxxp://www.bing.com/
uInternet Settings,ProxyOverride = <local>
TCP: DhcpNameServer = 192.168.1.1 4.2.2.2
.
- - - - ORPHANS REMOVED - - - -
.
WebBrowser-{FB0C9FD7-6768-4913-BD40-B4DD07D16AF2} - (no file)
HKLM-Run-zutro - c:\documents and settings\Gerry\Application Data\zutro.dll
HKLM-Run-dxlat - c:\documents and settings\Gerry\Application Data\dxlat.dll
SafeBoot-17240770.sys
SafeBoot-73432066.sys
SafeBoot-Wdf01000.sys
.
.
.
**************************************************************************
.
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net
Rootkit scan 2013-01-27 09:44
Windows 5.1.2600 Service Pack 3 NTFS
.
scanning hidden processes ...
.
scanning hidden autostart entries ...
.
scanning hidden files ...
.
scan completed successfully
hidden files: 0
.
**************************************************************************
.
--------------------- LOCKED REGISTRY KEYS ---------------------
.
[HKEY_LOCAL_MACHINE\software\Classes\CLSID\{73C9DFA0-750D-11E1-B0C4-0800200C9A66}]
@Denied: (A 2) (Everyone)
@="FlashBroker"
"LocalizedString"="@c:\\WINDOWS\\system32\\Macromed\\Flash\\FlashUtil32_11_5_502_146_ActiveX.exe,-101"
.
[HKEY_LOCAL_MACHINE\software\Classes\CLSID\{73C9DFA0-750D-11E1-B0C4-0800200C9A66}\Elevation]
"Enabled"=dword:00000001
.
[HKEY_LOCAL_MACHINE\software\Classes\CLSID\{73C9DFA0-750D-11E1-B0C4-0800200C9A66}\LocalServer32]
@="c:\\WINDOWS\\system32\\Macromed\\Flash\\FlashUtil32_11_5_502_146_ActiveX.exe"
.
[HKEY_LOCAL_MACHINE\software\Classes\CLSID\{73C9DFA0-750D-11E1-B0C4-0800200C9A66}\TypeLib]
@="{FAB3E735-69C7-453B-A446-B6823C6DF1C9}"
.
[HKEY_LOCAL_MACHINE\software\Classes\Interface\{6AE38AE0-750C-11E1-B0C4-0800200C9A66}]
@Denied: (A 2) (Everyone)
@="IFlashBroker5"
.
[HKEY_LOCAL_MACHINE\software\Classes\Interface\{6AE38AE0-750C-11E1-B0C4-0800200C9A66}\ProxyStubClsid32]
@="{00020424-0000-0000-C000-000000000046}"
.
[HKEY_LOCAL_MACHINE\software\Classes\Interface\{6AE38AE0-750C-11E1-B0C4-0800200C9A66}\TypeLib]
@="{FAB3E735-69C7-453B-A446-B6823C6DF1C9}"
"Version"="1.0"
.
--------------------- DLLs Loaded Under Running Processes ---------------------
.
- - - - - - - > 'explorer.exe'(4088)
c:\windows\system32\WININET.dll
c:\program files\DVD\AnyDVD\ADvdDiscHlp.dll
c:\program files\KatMouse\KatMouseS.dll
c:\windows\system32\ieframe.dll
c:\windows\system32\webcheck.dll
c:\windows\system32\WPDShServiceObj.dll
c:\windows\system32\PortableDeviceTypes.dll
c:\windows\system32\PortableDeviceApi.dll
.
------------------------ Other Running Processes ------------------------
.
c:\windows\system32\savedump.exe
c:\program files\Java\jre6\bin\jqs.exe
c:\program files\Yahoo!\SoftwareUpdate\YahooAUService.exe
c:\windows\system32\wscntfy.exe
.
**************************************************************************
.
Completion time: 2013-01-27 09:48:42 - machine was rebooted
ComboFix-quarantined-files.txt 2013-01-27 17:48
.
Pre-Run: 333,054,345,216 bytes free
Post-Run: 332,902,453,248 bytes free
.
WindowsXP-KB310994-SP2-Home-BootDisk-ENU.exe
[boot loader]
timeout=2
default=multi(0)disk(0)rdisk(0)partition(1)\WINDOWS
[operating systems]
c:\cmdcons\BOOTSECT.DAT="Microsoft Windows Recovery Console" /cmdcons
UnsupportedDebug="do not select this" /debug
multi(0)disk(0)rdisk(0)partition(1)\WINDOWS="Microsoft Windows XP Professional" /noexecute=optin /fastdetect
.
- - End Of File - - 5B7F2E6DA4C2B0AD95FECA86477A05F8
I read on another webpage that I would have to change the options in IE to uncheck "use Proxy Server" with this virus. Would I still have to do that now?
I ran IE on the affected PC and the "use Proxy Server" is not checked so that is a mute point. It seems everything is working ok now. Running a Malwarebytes scan to see if it finds anything.
Can't thank you enough. Your help was great!!!!!!!
Can't thank you enough. Your help was great!!!!!!!
Gerry said:I read on another webpage that I would have to change the options in IE to uncheck "use Proxy Server" with this virus. Would I still have to do that now?
If you are able to access Internet in the infected computer there will not be a proxy server settings... In the log also it seems clean only...
Now please send me the MalwareBytes Log.
Click on Start --> Run --> Type CMD in the Run Window and press on OK.
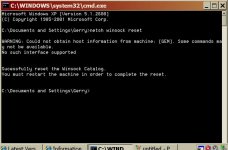
Now you will get a black Command Window.... Inside that black command window type NETSH WINSOCK RESET and hit on enter. Then if you are getting any prompt to click on Ok let me know...
I ran HiJackThis and here is the log. So far everything seems to be good. Do I leave the _OTL folder on my C drive or delete it?
Logfile of Trend Micro HijackThis v2.0.3 (BETA)
Scan saved at 3:37:32 PM, on 1/28/2013
Platform: Windows XP SP3 (WinNT 5.01.2600)
MSIE: Internet Explorer v8.00 (8.00.6001.18702)
Boot mode: Normal
Running processes:
C:\WINDOWS\System32\smss.exe
C:\WINDOWS\system32\winlogon.exe
C:\WINDOWS\system32\services.exe
C:\WINDOWS\system32\lsass.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\System32\svchost.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\Explorer.EXE
C:\WINDOWS\system32\spoolsv.exe
C:\Program Files\Java\jre6\bin\jqs.exe
C:\WINDOWS\system32\svchost.exe
C:\Program Files\Yahoo!\SoftwareUpdate\YahooAUService.exe
C:\WINDOWS\system32\wscntfy.exe
C:\Program Files\Spybot - Search & Destroy\TeaTimer.exe
C:\Program Files\DVD\AnyDVD\AnyDVDtray.exe
C:\WINDOWS\system32\ctfmon.exe
C:\WINDOWS\system32\svchost.exe
C:\Program Files\KatMouse\KatMouse.exe
C:\Program Files\Sony\Sony PC Companion\PCCompanion.exe
C:\Program Files\Sony\Sony PC Companion\PCCompanionInfo.exe
C:\Program Files\Sony\Sony PC Companion\PCCService.exe
C:\Program Files\HiJack\TrendMicro\HiJackThis\HiJackThis.exe
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://www.bing.com/
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://go.microsoft.com/fwlink/?LinkId=69157
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft.com/fwlink/?LinkId=54896
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896
R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://go.microsoft.com/fwlink/?LinkId=69157
O2 - BHO: AcroIEHelperStub - {18DF081C-E8AD-4283-A596-FA578C2EBDC3} - C:\Program Files\Common Files\Adobe\Acrobat\ActiveX\AcroIEHelperShim.dll
O2 - BHO: Spybot-S&D IE Protection - {53707962-6F74-2D53-2644-206D7942484F} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O2 - BHO: Java(tm) Plug-In 2 SSV Helper - {DBC80044-A445-435b-BC74-9C25C1C588A9} - C:\Program Files\Java\jre6\bin\jp2ssv.dll
O2 - BHO: JQSIEStartDetectorImpl - {E7E6F031-17CE-4C07-BC86-EABFE594F69C} - C:\Program Files\Java\jre6\lib\deploy\jqs\ie\jqs_plugin.dll
O2 - BHO: SingleInstance Class - {FDAD4DA1-61A2-4FD8-9C17-86F7AC245081} - C:\Program Files\Yahoo!\Companion\Installs\cpn0\YTSingleInstance.dll
O4 - HKLM\..\Run: [QuickTime Task] "C:\Program Files\QuickTime\qttask.exe" -atboottime
O4 - HKLM\..\Run: [Adobe Reader Speed Launcher] "C:\Program Files\Adobe\Reader 9.0\Reader\Reader_sl.exe"
O4 - HKLM\..\Run: [Adobe ARM] "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe"
O4 - HKCU\..\Run: [SpybotSD TeaTimer] C:\Program Files\Spybot - Search & Destroy\TeaTimer.exe
O4 - HKCU\..\Run: [Sony PC Companion] "C:\Program Files\Sony\Sony PC Companion\PCCompanion.exe" /Background
O4 - HKCU\..\Run: [AnyDVD] C:\Program Files\DVD\AnyDVD\AnyDVDtray.exe
O4 - HKCU\..\Run: [ctfmon.exe] C:\WINDOWS\system32\ctfmon.exe
O4 - HKUS\S-1-5-21-3240264975-1964901538-269542980-1007\..\Run: [SpybotSD TeaTimer] C:\Program Files\Spybot - Search & Destroy\TeaTimer.exe (User '?')
O4 - HKUS\S-1-5-21-3240264975-1964901538-269542980-1007\..\Run: [Sony PC Companion] "C:\Program Files\Sony\Sony PC Companion\PCCompanion.exe" /Background (User '?')
O4 - HKUS\S-1-5-21-3240264975-1964901538-269542980-1007\..\Run: [AnyDVD] C:\Program Files\DVD\AnyDVD\AnyDVDtray.exe (User '?')
O4 - HKUS\S-1-5-21-3240264975-1964901538-269542980-1007\..\Run: [ctfmon.exe] C:\WINDOWS\system32\ctfmon.exe (User '?')
O4 - S-1-5-21-3240264975-1964901538-269542980-1007 Startup: KatMouse.lnk = C:\Program Files\KatMouse\KatMouse.exe (User '?')
O4 - Startup: KatMouse.lnk = C:\Program Files\KatMouse\KatMouse.exe
O4 - Global Startup: Microsoft Office.lnk = C:\Program Files\Microsoft Office\Office\OSA9.EXE
O9 - Extra button: (no name) - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O9 - Extra 'Tools' menuitem: Spybot - Search & Destroy Configuration - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O9 - Extra button: (no name) - {e2e2dd38-d088-4134-82b7-f2ba38496583} - C:\WINDOWS\Network Diagnostic\xpnetdiag.exe
O9 - Extra 'Tools' menuitem: @xpsp3res.dll,-20001 - {e2e2dd38-d088-4134-82b7-f2ba38496583} - C:\WINDOWS\Network Diagnostic\xpnetdiag.exe
O16 - DPF: {6414512B-B978-451D-A0D8-FCFDF33E833C} (WUWebControl Class) - http://www.update.microsoft.com/windowsupdate/v6/V5Controls/en/x86/client/wuweb_site.cab?1358643604078
O16 - DPF: {D27CDB6E-AE6D-11CF-96B8-444553540000} (Shockwave Flash Object) - http://fpdownload2.macromedia.com/get/shockwave/cabs/flash/swflash.cab
O16 - DPF: {E2883E8F-472F-4FB0-9522-AC9BF37916A7} - http://platformdl.adobe.com/NOS/getPlusPlus/1.6/gp.cab
O22 - SharedTaskScheduler: Browseui preloader - {438755C2-A8BA-11D1-B96B-00A0C90312E1} - C:\WINDOWS\system32\browseui.dll
O22 - SharedTaskScheduler: Component Categories cache daemon - {8C7461EF-2B13-11d2-BE35-3078302C2030} - C:\WINDOWS\system32\browseui.dll
O23 - Service: Google Update Service (gupdate) (gupdate) - Google Inc. - C:\Program Files\Google\Update\GoogleUpdate.exe
O23 - Service: Google Update Service (gupdatem) (gupdatem) - Google Inc. - C:\Program Files\Google\Update\GoogleUpdate.exe
O23 - Service: Java Quick Starter (JavaQuickStarterService) - Sun Microsystems, Inc. - C:\Program Files\Java\jre6\bin\jqs.exe
O23 - Service: Sony PC Companion - Avanquest Software - C:\Program Files\Sony\Sony PC Companion\PCCService.exe
O23 - Service: Yahoo! Updater (YahooAUService) - Yahoo! Inc. - C:\Program Files\Yahoo!\SoftwareUpdate\YahooAUService.exe
--
End of file - 5648 bytes
Logfile of Trend Micro HijackThis v2.0.3 (BETA)
Scan saved at 3:37:32 PM, on 1/28/2013
Platform: Windows XP SP3 (WinNT 5.01.2600)
MSIE: Internet Explorer v8.00 (8.00.6001.18702)
Boot mode: Normal
Running processes:
C:\WINDOWS\System32\smss.exe
C:\WINDOWS\system32\winlogon.exe
C:\WINDOWS\system32\services.exe
C:\WINDOWS\system32\lsass.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\System32\svchost.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\Explorer.EXE
C:\WINDOWS\system32\spoolsv.exe
C:\Program Files\Java\jre6\bin\jqs.exe
C:\WINDOWS\system32\svchost.exe
C:\Program Files\Yahoo!\SoftwareUpdate\YahooAUService.exe
C:\WINDOWS\system32\wscntfy.exe
C:\Program Files\Spybot - Search & Destroy\TeaTimer.exe
C:\Program Files\DVD\AnyDVD\AnyDVDtray.exe
C:\WINDOWS\system32\ctfmon.exe
C:\WINDOWS\system32\svchost.exe
C:\Program Files\KatMouse\KatMouse.exe
C:\Program Files\Sony\Sony PC Companion\PCCompanion.exe
C:\Program Files\Sony\Sony PC Companion\PCCompanionInfo.exe
C:\Program Files\Sony\Sony PC Companion\PCCService.exe
C:\Program Files\HiJack\TrendMicro\HiJackThis\HiJackThis.exe
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://www.bing.com/
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://go.microsoft.com/fwlink/?LinkId=69157
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft.com/fwlink/?LinkId=54896
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896
R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://go.microsoft.com/fwlink/?LinkId=69157
O2 - BHO: AcroIEHelperStub - {18DF081C-E8AD-4283-A596-FA578C2EBDC3} - C:\Program Files\Common Files\Adobe\Acrobat\ActiveX\AcroIEHelperShim.dll
O2 - BHO: Spybot-S&D IE Protection - {53707962-6F74-2D53-2644-206D7942484F} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O2 - BHO: Java(tm) Plug-In 2 SSV Helper - {DBC80044-A445-435b-BC74-9C25C1C588A9} - C:\Program Files\Java\jre6\bin\jp2ssv.dll
O2 - BHO: JQSIEStartDetectorImpl - {E7E6F031-17CE-4C07-BC86-EABFE594F69C} - C:\Program Files\Java\jre6\lib\deploy\jqs\ie\jqs_plugin.dll
O2 - BHO: SingleInstance Class - {FDAD4DA1-61A2-4FD8-9C17-86F7AC245081} - C:\Program Files\Yahoo!\Companion\Installs\cpn0\YTSingleInstance.dll
O4 - HKLM\..\Run: [QuickTime Task] "C:\Program Files\QuickTime\qttask.exe" -atboottime
O4 - HKLM\..\Run: [Adobe Reader Speed Launcher] "C:\Program Files\Adobe\Reader 9.0\Reader\Reader_sl.exe"
O4 - HKLM\..\Run: [Adobe ARM] "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe"
O4 - HKCU\..\Run: [SpybotSD TeaTimer] C:\Program Files\Spybot - Search & Destroy\TeaTimer.exe
O4 - HKCU\..\Run: [Sony PC Companion] "C:\Program Files\Sony\Sony PC Companion\PCCompanion.exe" /Background
O4 - HKCU\..\Run: [AnyDVD] C:\Program Files\DVD\AnyDVD\AnyDVDtray.exe
O4 - HKCU\..\Run: [ctfmon.exe] C:\WINDOWS\system32\ctfmon.exe
O4 - HKUS\S-1-5-21-3240264975-1964901538-269542980-1007\..\Run: [SpybotSD TeaTimer] C:\Program Files\Spybot - Search & Destroy\TeaTimer.exe (User '?')
O4 - HKUS\S-1-5-21-3240264975-1964901538-269542980-1007\..\Run: [Sony PC Companion] "C:\Program Files\Sony\Sony PC Companion\PCCompanion.exe" /Background (User '?')
O4 - HKUS\S-1-5-21-3240264975-1964901538-269542980-1007\..\Run: [AnyDVD] C:\Program Files\DVD\AnyDVD\AnyDVDtray.exe (User '?')
O4 - HKUS\S-1-5-21-3240264975-1964901538-269542980-1007\..\Run: [ctfmon.exe] C:\WINDOWS\system32\ctfmon.exe (User '?')
O4 - S-1-5-21-3240264975-1964901538-269542980-1007 Startup: KatMouse.lnk = C:\Program Files\KatMouse\KatMouse.exe (User '?')
O4 - Startup: KatMouse.lnk = C:\Program Files\KatMouse\KatMouse.exe
O4 - Global Startup: Microsoft Office.lnk = C:\Program Files\Microsoft Office\Office\OSA9.EXE
O9 - Extra button: (no name) - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O9 - Extra 'Tools' menuitem: Spybot - Search & Destroy Configuration - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O9 - Extra button: (no name) - {e2e2dd38-d088-4134-82b7-f2ba38496583} - C:\WINDOWS\Network Diagnostic\xpnetdiag.exe
O9 - Extra 'Tools' menuitem: @xpsp3res.dll,-20001 - {e2e2dd38-d088-4134-82b7-f2ba38496583} - C:\WINDOWS\Network Diagnostic\xpnetdiag.exe
O16 - DPF: {6414512B-B978-451D-A0D8-FCFDF33E833C} (WUWebControl Class) - http://www.update.microsoft.com/windowsupdate/v6/V5Controls/en/x86/client/wuweb_site.cab?1358643604078
O16 - DPF: {D27CDB6E-AE6D-11CF-96B8-444553540000} (Shockwave Flash Object) - http://fpdownload2.macromedia.com/get/shockwave/cabs/flash/swflash.cab
O16 - DPF: {E2883E8F-472F-4FB0-9522-AC9BF37916A7} - http://platformdl.adobe.com/NOS/getPlusPlus/1.6/gp.cab
O22 - SharedTaskScheduler: Browseui preloader - {438755C2-A8BA-11D1-B96B-00A0C90312E1} - C:\WINDOWS\system32\browseui.dll
O22 - SharedTaskScheduler: Component Categories cache daemon - {8C7461EF-2B13-11d2-BE35-3078302C2030} - C:\WINDOWS\system32\browseui.dll
O23 - Service: Google Update Service (gupdate) (gupdate) - Google Inc. - C:\Program Files\Google\Update\GoogleUpdate.exe
O23 - Service: Google Update Service (gupdatem) (gupdatem) - Google Inc. - C:\Program Files\Google\Update\GoogleUpdate.exe
O23 - Service: Java Quick Starter (JavaQuickStarterService) - Sun Microsystems, Inc. - C:\Program Files\Java\jre6\bin\jqs.exe
O23 - Service: Sony PC Companion - Avanquest Software - C:\Program Files\Sony\Sony PC Companion\PCCService.exe
O23 - Service: Yahoo! Updater (YahooAUService) - Yahoo! Inc. - C:\Program Files\Yahoo!\SoftwareUpdate\YahooAUService.exe
--
End of file - 5648 bytes
Okay. All this Logs Seems to be Good.. 
Do you try my last Steps NETSH WINSOCK RESET ???
What was the result ?
Do you try my last Steps NETSH WINSOCK RESET ???
What was the result ?
Is it possible to send me the screen shot of what you are getting now?
To Take Screen Of Your Screen.
To Take Screen Of Your Screen.
- Press PRINT SCREEN (Print Scr) key on Your Keyboard.
- Now Open MS Paint
- Open Paint by clicking the Start button
, clicking All Programs, clicking Accessories, and then clicking Paint.

- In MS Paint Click Edit, and then click Paste.
- After this Save the File on your computer by Clicking on File --> Save
Click on Start --> Run --> Type CMD in the Run Window and press on OK.
Now you will get a black Command Window.... Inside that black command window type NETSH WINSOCK RESET and hit on enter. Then if you are getting any prompt to click on Ok Send me the Screenshots of that one....
Now you will get a black Command Window.... Inside that black command window type NETSH WINSOCK RESET and hit on enter. Then if you are getting any prompt to click on Ok Send me the Screenshots of that one....
Okay Cool...  Follow the other steps as well...
Follow the other steps as well...
STEP 1: Run a scan with ESET Online Scanner
<ol>
<li>Download ESET Online Scanner utility from the below link
<><a title="External link" href="http://download.eset.com/special/eos/esetsmartinstaller_enu.exe" rel="nofollow">ESET ONLINE SCANNER DOWNLOAD LINK</a></> <em>(This link will automatically download ESET Online Scanner on your computer.)</em></li>
<li>Double click on the Eset installer program (esetsmartinstaller_enu.exe).</li>
<li>Check <>Yes, I accept the Terms of Use</></li>
<li>Click the <>Start</> button.</li>
<li>Check <>Scan archives</></li>
<li>Push the <>Start</> button.</li>
<li>ESET will then download updates for itself, install itself, and begin scanning your computer. Please be patient as this can take some time.</li>
<li>When the scan completes, push <>List of found threats</></li>
<li>Push <>Export to Text file </> and save the file to your desktop using a unique name, such as <>ESET Scan</>. Include the contents of this report in your next reply.Note - when ESET doesn't find any threats, no report will be created.</li>
<li>Push the <>back</> button.</li>
<li>Push <>Finish</></li>
</ol>
<hr />
STEP 2: Run Temp File Cleaner by OldTimer
<ol>
<li>You can download the TFC utility from the below link
<a title="External link" href="http://oldtimer.geekstogo.com/TFC.exe" rel="nofollow external"><>TFC DOWNLOAD LINK</></a> <em>(This link will automatically download Temp File Cleaner on your computer)</em></li>
<li>Please double-click <>TFC.exe</> to run it. (<>Note:</> If you are running on Vista or 7, right-click on the file and choose <>Run As Administrator</>).</li>
<li>It <>will close all programs</> when run, so make sure you have <>saved all your work</> before you begin.</li>
<li>Click the <>Start</> button to begin the process. Depending on how often you clean temp files, execution time should be anywhere from a few seconds to a minute or two. <>Let it run uninterrupted to completion</>.</li>
<li>Once it's finished it should <>reboot your machine</>. If it does not, please <>manually reboot the machine</> yourself to ensure a complete clean.</li>
</ol>
<hr />
STEP 3: Run a scan with AdwCleaner
<ol><li>Download AdwCleaner from the below link.
<><a href="http://general-changelog-team.fr/fr/downloads/finish/20-outils-de-xplode/2-adwcleaner" target="_blank">ADWCLEANER DOWNLAOD LINK</a></> (This link will automatically download Security Check on your computer)</li>
<li>Close all open programs and internet browsers.</li>
<li>Double click on <>adwcleaner.exe</> to run the tool.</li>
<li>Click on <>Delete</>,then confirm each time with <>Ok</>.</li>
<li>Your computer will be rebooted automatically. A text file will open after the restart.</li>
<li>Please post the contents of that logfile with your next reply.</li>
<li>You can find the logfile at <>C:\AdwCleaner[S1].txt</> as well.</li>
</ol>
<hr/>
STEP 1: Run a scan with ESET Online Scanner
<ol>
<li>Download ESET Online Scanner utility from the below link
<><a title="External link" href="http://download.eset.com/special/eos/esetsmartinstaller_enu.exe" rel="nofollow">ESET ONLINE SCANNER DOWNLOAD LINK</a></> <em>(This link will automatically download ESET Online Scanner on your computer.)</em></li>
<li>Double click on the Eset installer program (esetsmartinstaller_enu.exe).</li>
<li>Check <>Yes, I accept the Terms of Use</></li>
<li>Click the <>Start</> button.</li>
<li>Check <>Scan archives</></li>
<li>Push the <>Start</> button.</li>
<li>ESET will then download updates for itself, install itself, and begin scanning your computer. Please be patient as this can take some time.</li>
<li>When the scan completes, push <>List of found threats</></li>
<li>Push <>Export to Text file </> and save the file to your desktop using a unique name, such as <>ESET Scan</>. Include the contents of this report in your next reply.Note - when ESET doesn't find any threats, no report will be created.</li>
<li>Push the <>back</> button.</li>
<li>Push <>Finish</></li>
</ol>
<hr />
STEP 2: Run Temp File Cleaner by OldTimer
<ol>
<li>You can download the TFC utility from the below link
<a title="External link" href="http://oldtimer.geekstogo.com/TFC.exe" rel="nofollow external"><>TFC DOWNLOAD LINK</></a> <em>(This link will automatically download Temp File Cleaner on your computer)</em></li>
<li>Please double-click <>TFC.exe</> to run it. (<>Note:</> If you are running on Vista or 7, right-click on the file and choose <>Run As Administrator</>).</li>
<li>It <>will close all programs</> when run, so make sure you have <>saved all your work</> before you begin.</li>
<li>Click the <>Start</> button to begin the process. Depending on how often you clean temp files, execution time should be anywhere from a few seconds to a minute or two. <>Let it run uninterrupted to completion</>.</li>
<li>Once it's finished it should <>reboot your machine</>. If it does not, please <>manually reboot the machine</> yourself to ensure a complete clean.</li>
</ol>
<hr />
STEP 3: Run a scan with AdwCleaner
<ol><li>Download AdwCleaner from the below link.
<><a href="http://general-changelog-team.fr/fr/downloads/finish/20-outils-de-xplode/2-adwcleaner" target="_blank">ADWCLEANER DOWNLAOD LINK</a></> (This link will automatically download Security Check on your computer)</li>
<li>Close all open programs and internet browsers.</li>
<li>Double click on <>adwcleaner.exe</> to run the tool.</li>
<li>Click on <>Delete</>,then confirm each time with <>Ok</>.</li>
<li>Your computer will be rebooted automatically. A text file will open after the restart.</li>
<li>Please post the contents of that logfile with your next reply.</li>
<li>You can find the logfile at <>C:\AdwCleaner[S1].txt</> as well.</li>
</ol>
<hr/>
Last edited by a moderator:
Gerry all those logs seems fine... Are you facing any other particular issues on the computer now?
STEP 1: Run a HitmanPro scan
<ol>
<li><>Download the latest official version of HitmanPro</>.
<a href="http://www.surfright.nl/en/hitmanpro/" rel="nofollow" target="_blank"> <>HITMANPRO DOWNLOAD LINK</></a> <em>(This link will open a download page in a new window from where you can download HitmanPro)</em></li>
<li>Start HitmanPro by <>double clicking on the previously downloaded file.</> and then following the prompts.
<img src="http://malwaretips.com/images/removalguide/hpro4.png" alt="[Image: hitmanproscan4.png]" border="0" /></li>
<li>Once the scan is complete, a screen displaying all the malicious files that the program found will be shown as seen in the image below.After reviewing each malicious object click <>Next</> .
<img src="http://malwaretips.com/blogs/wp-content/uploads/2012/02/rsz_hpro5.png" alt="[Image: hitmanproscan5.png]" border="0" /></li>
<li>Click <>Activate free license</> to start the free 30 days trial and remove the malicious files.
<img src="http://malwaretips.com/images/removalguide/hpro6.png" alt="[Image: hitmanproscan6.png]" border="0" /></li>
<li>HitmanPro will now start removing the infected objects, and in some instances, may suggest a reboot in order to completely remove the malware from your system. In this scenario, always confirm the reboot action to be on the safe side.
</ol>
Add to your next reply, any log that HitmanPro might generate.
<hr />
You should be able to run both scans while in Normal mode...
STEP 2: Run a scan with Malwarebytes Anti-Malware in Chamelon mode
<ol>
<li>Download <>Malwarebytes Chameleon from <a title="External link" href="http://downloads.malwarebytes.org/file/chameleon" rel="nofollow external">here</a> </>and extract it to a folder in a convenient location</li>
<li>Make certain that your PC is connected to the internet and then open the folder where you extracted Chameleon to and double-click on the Chameleon help file and then follow the onscreen instructions to use it.</li>
<li>If the Chameleon help file itself will not open, then double-click each file one by one until you find one that works, which will be indicated by a black DOS/command prompt window <em><>Note:</> Do not attempt to open <>mbam-killer</> as that is not a Chameleon executable and serves a different purpose)</em></li>
<li>Follow the onscreen instructions to press a key to continue and Chameleon will proceed to download and install Malwarebytes Anti-Malware for yo</li>
<li>Once it has done this, it will attempt to update Malwarebytes Anti-Malware, click <>OK</> when it says that the database was updated successful</li>
<li>Next, Malwarebytes Anti-Malware will automatically open and perform a Quick scan</li>
<li>Upon completion of the scan, if anything has been detected, click on <>Show Result</></li>
<li>Have Malwarebytes Anti-Malware remove any threats that are detected and click <>Yes</> if prompted to reboot your computer to allow the removal process to complete</li>
<li>After your computer restarts, open <>Malwarebytes Anti-Malware</> and perform a Full System scan to verify that there are no remaining threats</li>
Please add both logs in your next reply.
</ol>
<hr />
STEP 1: Run a HitmanPro scan
<ol>
<li><>Download the latest official version of HitmanPro</>.
<a href="http://www.surfright.nl/en/hitmanpro/" rel="nofollow" target="_blank"> <>HITMANPRO DOWNLOAD LINK</></a> <em>(This link will open a download page in a new window from where you can download HitmanPro)</em></li>
<li>Start HitmanPro by <>double clicking on the previously downloaded file.</> and then following the prompts.
<img src="http://malwaretips.com/images/removalguide/hpro4.png" alt="[Image: hitmanproscan4.png]" border="0" /></li>
<li>Once the scan is complete, a screen displaying all the malicious files that the program found will be shown as seen in the image below.After reviewing each malicious object click <>Next</> .
<img src="http://malwaretips.com/blogs/wp-content/uploads/2012/02/rsz_hpro5.png" alt="[Image: hitmanproscan5.png]" border="0" /></li>
<li>Click <>Activate free license</> to start the free 30 days trial and remove the malicious files.
<img src="http://malwaretips.com/images/removalguide/hpro6.png" alt="[Image: hitmanproscan6.png]" border="0" /></li>
<li>HitmanPro will now start removing the infected objects, and in some instances, may suggest a reboot in order to completely remove the malware from your system. In this scenario, always confirm the reboot action to be on the safe side.
</ol>
Add to your next reply, any log that HitmanPro might generate.
<hr />
You should be able to run both scans while in Normal mode...
STEP 2: Run a scan with Malwarebytes Anti-Malware in Chamelon mode
<ol>
<li>Download <>Malwarebytes Chameleon from <a title="External link" href="http://downloads.malwarebytes.org/file/chameleon" rel="nofollow external">here</a> </>and extract it to a folder in a convenient location</li>
<li>Make certain that your PC is connected to the internet and then open the folder where you extracted Chameleon to and double-click on the Chameleon help file and then follow the onscreen instructions to use it.</li>
<li>If the Chameleon help file itself will not open, then double-click each file one by one until you find one that works, which will be indicated by a black DOS/command prompt window <em><>Note:</> Do not attempt to open <>mbam-killer</> as that is not a Chameleon executable and serves a different purpose)</em></li>
<li>Follow the onscreen instructions to press a key to continue and Chameleon will proceed to download and install Malwarebytes Anti-Malware for yo</li>
<li>Once it has done this, it will attempt to update Malwarebytes Anti-Malware, click <>OK</> when it says that the database was updated successful</li>
<li>Next, Malwarebytes Anti-Malware will automatically open and perform a Quick scan</li>
<li>Upon completion of the scan, if anything has been detected, click on <>Show Result</></li>
<li>Have Malwarebytes Anti-Malware remove any threats that are detected and click <>Yes</> if prompted to reboot your computer to allow the removal process to complete</li>
<li>After your computer restarts, open <>Malwarebytes Anti-Malware</> and perform a Full System scan to verify that there are no remaining threats</li>
Please add both logs in your next reply.
</ol>
<hr />
Last edited by a moderator:
No problems seen as of now. I was concerned about ComboFix being compromised and if I should delete the _OTL folder on my C Drive.
I already used my 30 day free trial of HitManPro so can not use it again.
I already run Malwarebytes Anti-Malware and found nothing. What is the Chameleon mode and do I need to do Step 2?
I already used my 30 day free trial of HitManPro so can not use it again.
I already run Malwarebytes Anti-Malware and found nothing. What is the Chameleon mode and do I need to do Step 2?
Hi Just Run the ESET Online Scanner once again so that we can confirm the Combofix didn't infected your computer files.
Upload the Combofix file on your computer to https://www.virustotal.com/ and let me know what is the Scan Result....
STEP 1: Run a scan with ESET Online Scanner
<ol>
<li>Download ESET Online Scanner utility from the below link
<><a title="External link" href="http://download.eset.com/special/eos/esetsmartinstaller_enu.exe" rel="nofollow">ESET ONLINE SCANNER DOWNLOAD LINK</a></> <em>(This link will automatically download ESET Online Scanner on your computer.)</em></li>
<li>Double click on the Eset installer program (esetsmartinstaller_enu.exe).</li>
<li>Check <>Yes, I accept the Terms of Use</></li>
<li>Click the <>Start</> button.</li>
<li>Check <>Scan archives</></li>
<li>Push the <>Start</> button.</li>
<li>ESET will then download updates for itself, install itself, and begin scanning your computer. Please be patient as this can take some time.</li>
<li>When the scan completes, push <>List of found threats</></li>
<li>Push <>Export to Text file </> and save the file to your desktop using a unique name, such as <>ESET Scan</>. Include the contents of this report in your next reply.Note - when ESET doesn't find any threats, no report will be created.</li>
<li>Push the <>back</> button.</li>
<li>Push <>Finish</></li>
</ol>
<hr />
After Uploading & Scan The Combofix File to Virus Total go with Step-2
STEP 2: Remove the OTL utility from your computer
Run OTL and hit the <>CleanUp</> button. It will remove all the programmes we have used plus itself. We will now confirm that your hidden files are set to that, as some of the tools I use will change that
<ol>
<li>Go to control panel</li>
<li>Select folder options (Appearance > Folder options in category view)</li>
<li>Select the View Tab.</li>
<li>Under the Hidden files and folders heading select <>Do not show hidden files and folders</>.</li>
<li>Click Yes to confirm.</li>
<li>Click OK.</li>
</ol>
<hr />
Upload the Combofix file on your computer to https://www.virustotal.com/ and let me know what is the Scan Result....
STEP 1: Run a scan with ESET Online Scanner
<ol>
<li>Download ESET Online Scanner utility from the below link
<><a title="External link" href="http://download.eset.com/special/eos/esetsmartinstaller_enu.exe" rel="nofollow">ESET ONLINE SCANNER DOWNLOAD LINK</a></> <em>(This link will automatically download ESET Online Scanner on your computer.)</em></li>
<li>Double click on the Eset installer program (esetsmartinstaller_enu.exe).</li>
<li>Check <>Yes, I accept the Terms of Use</></li>
<li>Click the <>Start</> button.</li>
<li>Check <>Scan archives</></li>
<li>Push the <>Start</> button.</li>
<li>ESET will then download updates for itself, install itself, and begin scanning your computer. Please be patient as this can take some time.</li>
<li>When the scan completes, push <>List of found threats</></li>
<li>Push <>Export to Text file </> and save the file to your desktop using a unique name, such as <>ESET Scan</>. Include the contents of this report in your next reply.Note - when ESET doesn't find any threats, no report will be created.</li>
<li>Push the <>back</> button.</li>
<li>Push <>Finish</></li>
</ol>
<hr />
After Uploading & Scan The Combofix File to Virus Total go with Step-2
STEP 2: Remove the OTL utility from your computer
Run OTL and hit the <>CleanUp</> button. It will remove all the programmes we have used plus itself. We will now confirm that your hidden files are set to that, as some of the tools I use will change that
<ol>
<li>Go to control panel</li>
<li>Select folder options (Appearance > Folder options in category view)</li>
<li>Select the View Tab.</li>
<li>Under the Hidden files and folders heading select <>Do not show hidden files and folders</>.</li>
<li>Click Yes to confirm.</li>
<li>Click OK.</li>
</ol>
<hr />
Last edited by a moderator:
- Status
- Not open for further replies.
You may also like...
-
Question I had to use a few second opinion scanners alongside Kaspersky premium. Any chance of Kaspersky corruption.
- Started by nonamebob567
- Replies: 18
-
moresearchhh.com redirect malware
- Started by TheFatBready
- Replies: 10
-
Help Needed: Suspicious Activity & Possible Malware on Windows 10 PC
- Started by Thomas Ellias
- Replies: 4
-
-
Solved Help to remove a virus
- Started by Jone Doh
- Replies: 31