- Feb 11, 2017
- 264
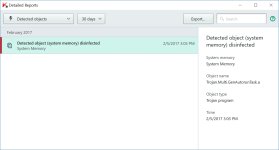
Called "fileless malware" attacks because the malware resides only in memory and is mostly hidden, these exploits have been used by unknown cyberthieves to steal from ATMs and customer accounts. However, the full extent of damages isn't always known.