- Feb 4, 2016
- 2,520
source (bleepingcomputer.com): Firefox Will Block Navigational Data URIs as Part of an Anti-Phishing Feature
Mozilla will soon block the loading of data URIs in the Firefox navigation bar as part of a crackdown on phishing sites that abuse this protocol.
The data: URI scheme (RFC 2397) was deployed in 1998 when developers were looking for ways to embed files in other files. What they came up with was the data: URI scheme that allows a developer to load a file represented as an ASCII-encoded octet stream inside another document.
Since then, the URI scheme has become very popular with website developers as it allows them to embed text-based (CSS or JS) files or image (PNG, JPEG) files inside HTML documents instead of loading each resource via a separate HTTP request.
This practice became hugely popular because search engines started ranking websites based on their page loading speed and the more HTTP requests a website made, the slower it loaded, and the more it affected a site's SERP position.
You don't have to look too far for websites that use data:image/png;base64 raw streams to embed images inside HTML or CSS files instead of loading resources via "Domain Name Registration and Web Hosting | Domain.com..." HTTP requests.
< img src="data:image/png;base64,iVBORw0KGgoAAA
ANSUhEUgAAAAUAAAAFCAYAAACNbyblAAAAHElEQVQI12P4
//8/w38GIAXDIBKE0DHxgljNBAAO9TXL0Y4OHwAAAABJRU
5ErkJggg==" alt="Red dot" / >
Data URIs are very popular with phishers, tech support scammers
But somewhere in the late 2000s, security researchers realized that data URIs could also be abused for phishing and XSS (cross-site scripting) attacks, a technique that was later perfected and better explained in 2012 by a researcher from the University of Oslo in Norway.
Since then, data URI-based phishing has become commonplace, with several phishing campaigns utilizing this tactic being reported almost every year [1, 2, 3, 4], and recently, even incorporated in tech support scams.
The most abused cases are "data:text/html;base64" and "data:application/x-javascript;base64" URIs, which provide a way to embed malicious HTML and JavaScript code inside legitimate sites.
Data URI blocking arriving in Firefox 59
Mozilla has already started rolling out the data URI blocking mechanisms since Firefox 56, but they are officially scheduled to go live for all users in Firefox 59.
Data URI blocking is already active in Firefox Nightly and Developer edition. The feature is not active in the recently released Firefox 57.
Users can enable data URI blocking in Firefox 56 and 57 by typing "about:config" in the URL bar and accessing Firefox's hidden configuration panel.
Here, they must search for "security.data_uri.block_toplevel_data_uri_navigations" and double-click to enable the feature in Firefox right now.
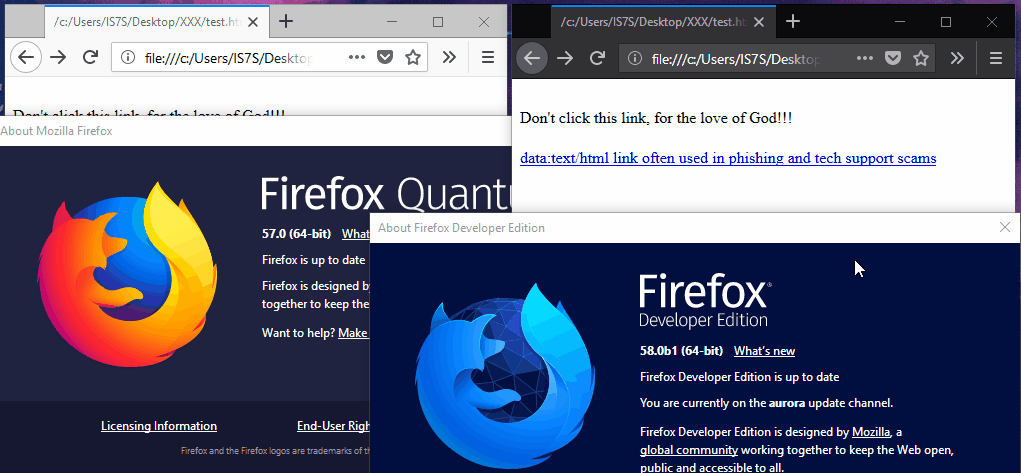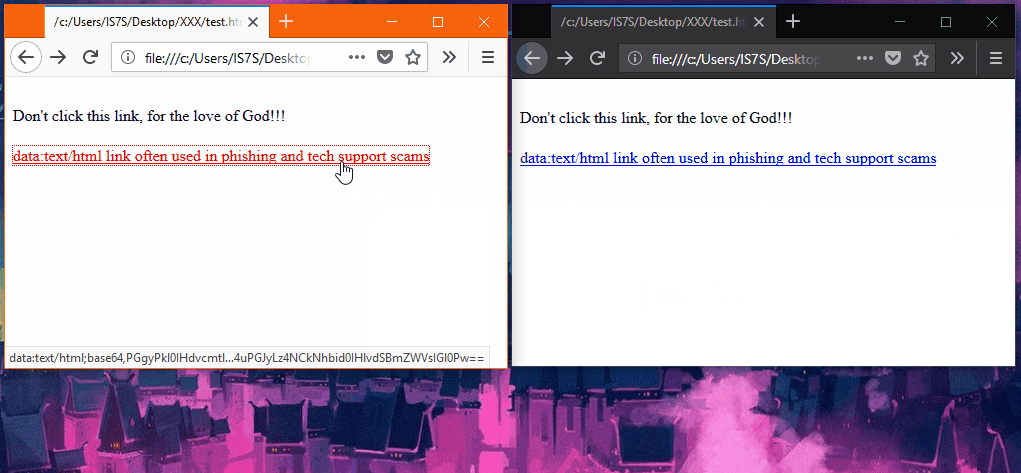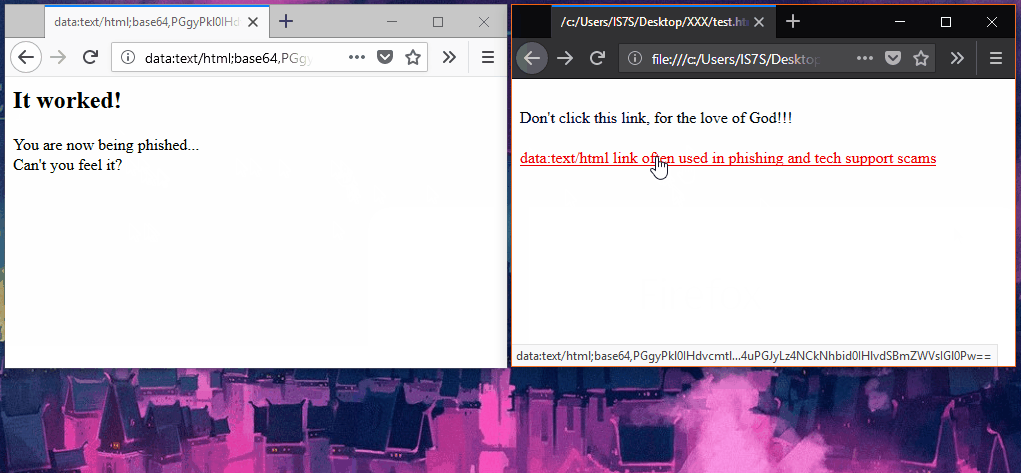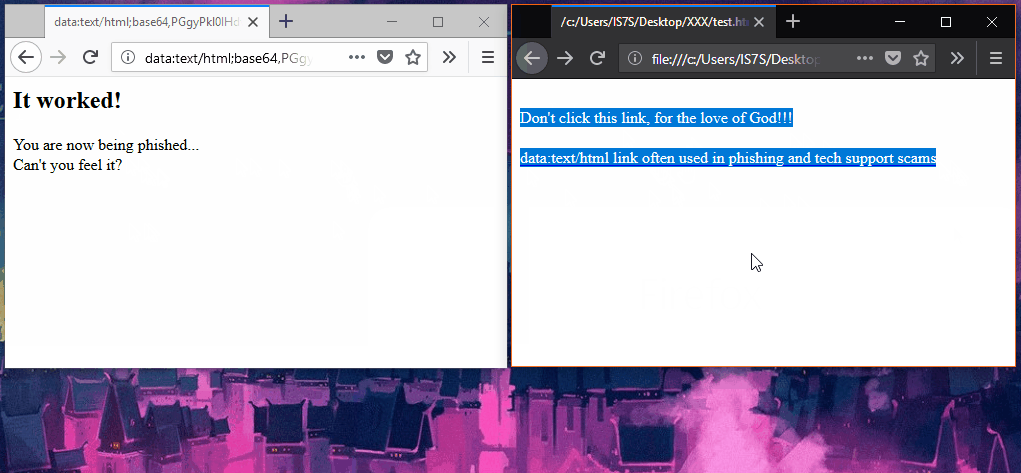
If all is successful, when you click on links that point to data URIs, the link will refuse to load, similar to the GIF below.