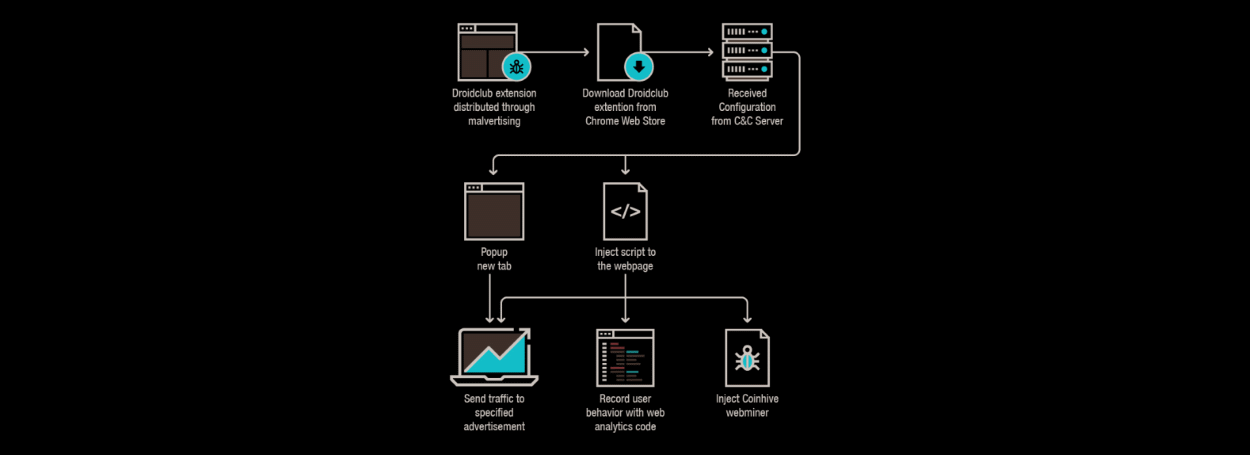
Just three months after Princeton researchers were warning users of the dangers of
"session replay" attacks, developers of malicious Chrome extensions have incorporated this "trick" into their latest "releases."
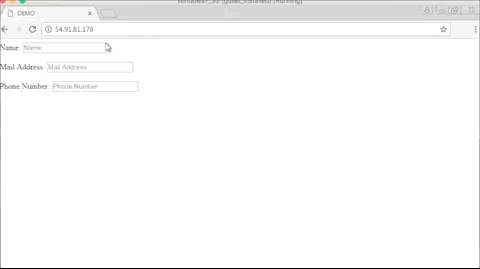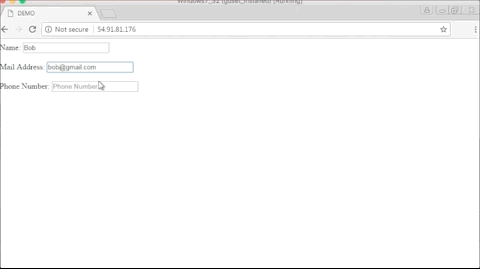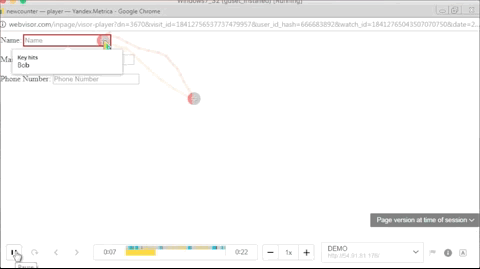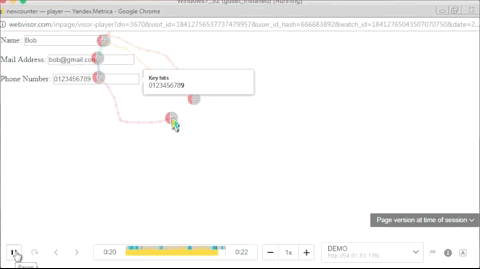
The term "session replay" refers to JavaScript code that records user activity and then plays it back in exact detail. Over the past several years, web analytics firms have added support for "session replay" features in their dashboard, allowing website owners to analyze how users were utilizing their website. These are valuable A/B testing tools if used for legitimate reasons.
Crooks abusing Yandex Metrica "session replay" script
Over the past several weeks, several malicious Chrome extensions have started embedding a JavaScript library provided by web analytics provider Yandex Metrica, which records user actions on all the sites they surf.
While Yandex Metrica does not record text entered in password fields, the script can still log various sorts of details, such as names, credit card numbers, CVV numbers, email addresses, and phone numbers.
Below is a GIF of what the operators of these malicious Chrome extensions are seeing when replaying a user session.