L
LabZero
Thread author
Source : https://community.qualys.com/blogs/laws-of-vulnerabilities/2015/01/27/the-ghost-vulnerability
GHOST is a serious vulnerability in the library glibc on Linux and allows attackers to execute code remotely (RCE - Remote Code Execution) without having any prior knowledge of the system credentials. This vulnerability has been assigned CVE-2015-0235.
The vulnerability was discovered by researchers at Qualys and affects the library from version 2.2, included in Linux systems by November 2000.
The bug has been fixed May 21, 2013 (between releases 2.17 and 2.18), but unfortunately the leak was not recognized as a threat to the security and, therefore, the most stable distributions, with long-term support, were exposed; Debian 7 (wheezy), Red Hat Enterprise Linux 6 & 7, CentOS 6 & 7, Ubuntu 12.04, are just a few examples.
What is your glibc?
Glibc is an implementation of the standard C library and critical part of the Linux operating system.
Technical analysis of the vulnerability GHOST
GHOST is vulnerable to a buffer overflow triggered by the gethostbyname () call. This function is used to resolve domain names to IP addresses (DNS) from various applications.
Through the function gethostbyname () or gethostbyname2 (), the overflow is present throughout the heap; while in functions gethostbyname_r () or gethostbyname2_r (), the overflow is defined by the "caller" (and can be located in the heap, the stack, .data, .bss, etc., but in practice have not been observed in this call general).
The overflow is long at most the size of, sizeof (char *), 4 bytes for 32-bit and 8 bytes on 64-bit machines; consisting only of numbers ('0' ... '9'), points ('.'), and null character ('\ 0'); Despite these limitations, the execution of arbitrary code can still be reached.
The function vulnerable __nss_hostname_digits_dots (), is called internally by glibc in nss / getXXbyYY.ce in nss / getXXbyYY_r.c.
The call is "protected" by the macro #ifdef HANDLE_DIGITS_DOTS, defined in:
inet / gethstbynm.c
inet / gethstbynm2.c
inet / gethstbynm_r.c
inet / gethstbynm2_r.c
nscd / gethstbynm3_r.c
These files implement gethostbyname () and are therefore the only way to reach __nss_hostname_digits_dots () and the buffer overflow.
The purpose of this function is to avoid costly inquiries DNS hostname if the topic is already an IPv4 or IPv6.
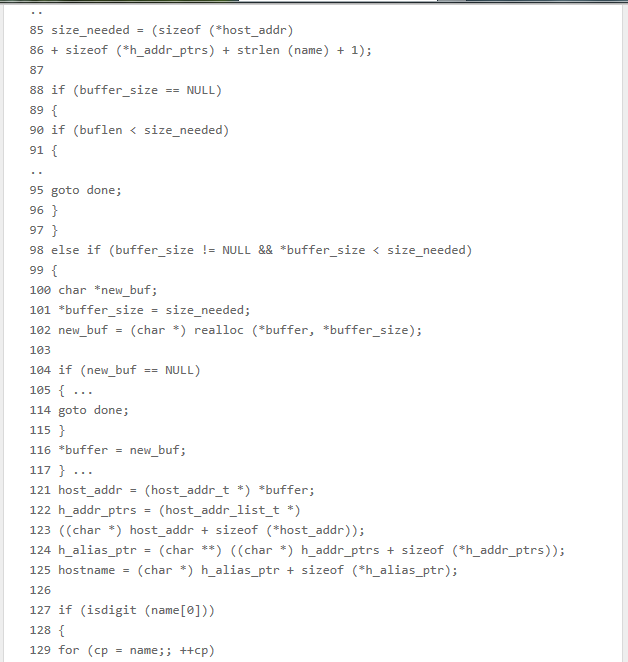
-Lines 85-86 calculates size_needed to store three separate entities in the buffer: host_addr, h_addr_ptrs, and name (hostname).
-Lines 88-117 ensure that the buffer is large enough.
-Lines 121-125 prepares the pointer to the buffer to store four entities: host_addr, h_addr_ptrs, h_alias_ptr and hostname. sizeof (* h_alias_ptr), the size of the character pointer, missing in the calculation size_needed.
The strcpy () in line 157 allows us to write past the end of the buffer, (depends strlen (name) and alignment) 4 bytes or 8 bytes by architecture.
To reach the overflow at line 157 the argument hostname must meet the following requirements:
Its first character must be a number (line 127).
The last character must not be a point (line 135).
Must include only numbers and periods (line 197).
It must be quite "long" to overwrite the buffer. For example, the function gethostbyname () initially allocates its buffer with a call to malloc (1024) (1KB).
Must be "parsed" properly as IPv4 address from inet_aton () (line 143), or IPv6 address inet_pton () (line 147); inet_aton () is not the only option to reach the overflow, and the hostname must be in one of the following forms: "abcd", "abc", "ab", or "a"; where: a, b, c, d must be unsigned integers, successfully converted to decimal or octal (not in hexadecimal, because 'x' and 'X' are prohibited).
In conclusion, if the name parameter contains an IP address in the function __nss_hostname_digits_dots () the IP is written in a buffer; the location to be written depends on the length of the name parameter passed to it. Therefore passing it as a parameter an IP address longer than normal (1024.10224.102224.1022224) will force the function to write the address "a rightmost byte", thus allowing a byte to be written out of the buffer.
Fortunately, for most users, there are many factors that mitigate the risks of GHOST, a closer examination reveals that this particular vulnerability, albeit serious, is not easily exploitable with only four or eight bytes as the initial vector of the exploit, gain additional access issue is highly dependent on the design of the application and memory usage.
Moreover, the functions subject of this vulnerability are obsolete, they can not be used to translate domain names into IPv6 addresses and the latest applications using the function getaddrinfo (), with the support IPv6.
The actual risk of exploits for GHOST is relatively modest compared with vulnerability as Shellshock, Heartbleed or POODLE.
Enjoy with malware analysis
GHOST is a serious vulnerability in the library glibc on Linux and allows attackers to execute code remotely (RCE - Remote Code Execution) without having any prior knowledge of the system credentials. This vulnerability has been assigned CVE-2015-0235.
The vulnerability was discovered by researchers at Qualys and affects the library from version 2.2, included in Linux systems by November 2000.
The bug has been fixed May 21, 2013 (between releases 2.17 and 2.18), but unfortunately the leak was not recognized as a threat to the security and, therefore, the most stable distributions, with long-term support, were exposed; Debian 7 (wheezy), Red Hat Enterprise Linux 6 & 7, CentOS 6 & 7, Ubuntu 12.04, are just a few examples.
What is your glibc?
Glibc is an implementation of the standard C library and critical part of the Linux operating system.
Technical analysis of the vulnerability GHOST
GHOST is vulnerable to a buffer overflow triggered by the gethostbyname () call. This function is used to resolve domain names to IP addresses (DNS) from various applications.
Through the function gethostbyname () or gethostbyname2 (), the overflow is present throughout the heap; while in functions gethostbyname_r () or gethostbyname2_r (), the overflow is defined by the "caller" (and can be located in the heap, the stack, .data, .bss, etc., but in practice have not been observed in this call general).
The overflow is long at most the size of, sizeof (char *), 4 bytes for 32-bit and 8 bytes on 64-bit machines; consisting only of numbers ('0' ... '9'), points ('.'), and null character ('\ 0'); Despite these limitations, the execution of arbitrary code can still be reached.
The function vulnerable __nss_hostname_digits_dots (), is called internally by glibc in nss / getXXbyYY.ce in nss / getXXbyYY_r.c.
The call is "protected" by the macro #ifdef HANDLE_DIGITS_DOTS, defined in:
inet / gethstbynm.c
inet / gethstbynm2.c
inet / gethstbynm_r.c
inet / gethstbynm2_r.c
nscd / gethstbynm3_r.c
These files implement gethostbyname () and are therefore the only way to reach __nss_hostname_digits_dots () and the buffer overflow.
The purpose of this function is to avoid costly inquiries DNS hostname if the topic is already an IPv4 or IPv6.
-Lines 85-86 calculates size_needed to store three separate entities in the buffer: host_addr, h_addr_ptrs, and name (hostname).
-Lines 88-117 ensure that the buffer is large enough.
-Lines 121-125 prepares the pointer to the buffer to store four entities: host_addr, h_addr_ptrs, h_alias_ptr and hostname. sizeof (* h_alias_ptr), the size of the character pointer, missing in the calculation size_needed.
The strcpy () in line 157 allows us to write past the end of the buffer, (depends strlen (name) and alignment) 4 bytes or 8 bytes by architecture.
To reach the overflow at line 157 the argument hostname must meet the following requirements:
Its first character must be a number (line 127).
The last character must not be a point (line 135).
Must include only numbers and periods (line 197).
It must be quite "long" to overwrite the buffer. For example, the function gethostbyname () initially allocates its buffer with a call to malloc (1024) (1KB).
Must be "parsed" properly as IPv4 address from inet_aton () (line 143), or IPv6 address inet_pton () (line 147); inet_aton () is not the only option to reach the overflow, and the hostname must be in one of the following forms: "abcd", "abc", "ab", or "a"; where: a, b, c, d must be unsigned integers, successfully converted to decimal or octal (not in hexadecimal, because 'x' and 'X' are prohibited).
In conclusion, if the name parameter contains an IP address in the function __nss_hostname_digits_dots () the IP is written in a buffer; the location to be written depends on the length of the name parameter passed to it. Therefore passing it as a parameter an IP address longer than normal (1024.10224.102224.1022224) will force the function to write the address "a rightmost byte", thus allowing a byte to be written out of the buffer.
Fortunately, for most users, there are many factors that mitigate the risks of GHOST, a closer examination reveals that this particular vulnerability, albeit serious, is not easily exploitable with only four or eight bytes as the initial vector of the exploit, gain additional access issue is highly dependent on the design of the application and memory usage.
Moreover, the functions subject of this vulnerability are obsolete, they can not be used to translate domain names into IPv6 addresses and the latest applications using the function getaddrinfo (), with the support IPv6.
The actual risk of exploits for GHOST is relatively modest compared with vulnerability as Shellshock, Heartbleed or POODLE.
Enjoy with malware analysis