Attackers can easily craft third party scripts to imitate Google to trick users into granting authorisation to their email accounts, says infosec chap Andrew Cantino.
The Mavenlink engineer said Mountain View did not make it sufficiently clear when users were approving third party access to their data, thus making social engineering attacks easy.
"A malicious person could make a [Google] Apps Script that performs almost any action against a user's Google data, then share the link in the guise of a helpful tool," Cantino said.
"Since the URL will be to script.google.com, it looks legitimate and even savvy users will likely be fooled.
"My particular script actually just makes a new Gmail label but it could have deleted data, emailed a link to the script to everyone in the user's contact list, manipulated personal information, or stolen data and sent it to a third party."
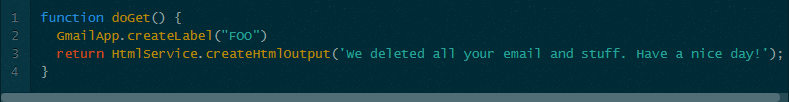
Andrew Cantino's proof of concept app
He said Google "in no way" made clear that his app was the product of a third party, adding that Mountain View did not intend on fixing what he said was a flaw.
The company took his suggestion "into consideration" but did not regard it as a technical vulnerability.
Cantino created an app dubbed 'Google Security Upgrader' to demonstrate how attackers could compromise Google accounts without being flagged as a third party. Google did, as it does for its Android platform, show the permissions that a given app had sought – which included actions such as the ability to view and manage email.
Cantino argued that the use of the 'accounts.google.com' URL added to the legitimacy of fake malicious applications.
He said Google should at minimum warn users that a given app was a third party product when it requested permissions, and noted the irony of its email sent after installation explaining that the user had installed a third party app.
"As it is, I feel it is unreasonable to expect that users would understand the possibility that malicious code could be executed while remaining entirely within the Google domain."
The Mavenlink engineer said Mountain View did not make it sufficiently clear when users were approving third party access to their data, thus making social engineering attacks easy.
"A malicious person could make a [Google] Apps Script that performs almost any action against a user's Google data, then share the link in the guise of a helpful tool," Cantino said.
"Since the URL will be to script.google.com, it looks legitimate and even savvy users will likely be fooled.
"My particular script actually just makes a new Gmail label but it could have deleted data, emailed a link to the script to everyone in the user's contact list, manipulated personal information, or stolen data and sent it to a third party."

Andrew Cantino's proof of concept app
He said Google "in no way" made clear that his app was the product of a third party, adding that Mountain View did not intend on fixing what he said was a flaw.
The company took his suggestion "into consideration" but did not regard it as a technical vulnerability.
Cantino created an app dubbed 'Google Security Upgrader' to demonstrate how attackers could compromise Google accounts without being flagged as a third party. Google did, as it does for its Android platform, show the permissions that a given app had sought – which included actions such as the ability to view and manage email.
Cantino argued that the use of the 'accounts.google.com' URL added to the legitimacy of fake malicious applications.
He said Google should at minimum warn users that a given app was a third party product when it requested permissions, and noted the irony of its email sent after installation explaining that the user had installed a third party app.
"As it is, I feel it is unreasonable to expect that users would understand the possibility that malicious code could be executed while remaining entirely within the Google domain."