- Apr 17, 2020
- 542
Google Chrome will no longer show whether a site you are visiting is secure and only show when you visit an insecure website.
For years, Google has been making a concerted effort to push websites into using HTTPS to provide a more secure browsing experience.
To further push web developers into only using HTTPS on their sites, Google introduced the protocol as a ranking factor. Those not hosting a secure site got a potentially minor hit in their Google search results rankings.
It has appeared to have worked as according to the 'HTTPS encryption on the web' of Google's Transparency Report, over 90% of all browser connections in Google Chrome currently use an HTTPS connection.
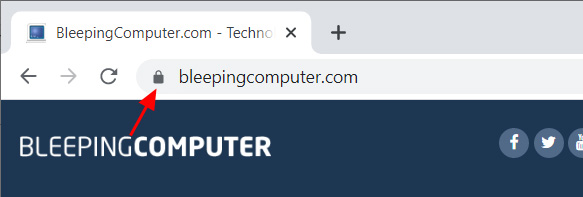
Currently, when you visit a secure site, Google Chrome will display a little locked icon indicating that your communication with the site is encrypted, as shown below.
As most website communication is now secure, Google is testing a new feature that removes the lock icon for secure sites. This feature is available to test in Chrome 93 Beta, and Chrome 94 Canary builds by enabling the 'Omnibox Updated connection security indicators' flag.

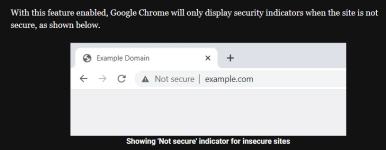
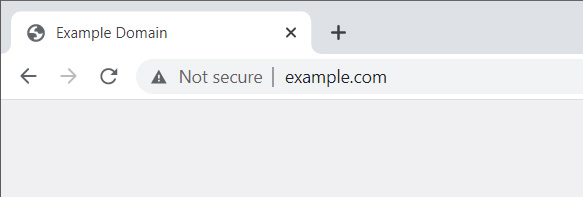
With this feature enabled, Google Chrome will only display security indicators when the site is not secure, as shown below.

 www.bleepingcomputer.com
www.bleepingcomputer.com
For years, Google has been making a concerted effort to push websites into using HTTPS to provide a more secure browsing experience.
To further push web developers into only using HTTPS on their sites, Google introduced the protocol as a ranking factor. Those not hosting a secure site got a potentially minor hit in their Google search results rankings.
It has appeared to have worked as according to the 'HTTPS encryption on the web' of Google's Transparency Report, over 90% of all browser connections in Google Chrome currently use an HTTPS connection.
Currently, when you visit a secure site, Google Chrome will display a little locked icon indicating that your communication with the site is encrypted, as shown below.

As most website communication is now secure, Google is testing a new feature that removes the lock icon for secure sites. This feature is available to test in Chrome 93 Beta, and Chrome 94 Canary builds by enabling the 'Omnibox Updated connection security indicators' flag.

With this feature enabled, Google Chrome will only display security indicators when the site is not secure, as shown below.


Google Chrome to no longer show secure website indicators
Google Chrome will no longer show whether a site you are visiting is secure and only show when you visit an insecure website.