- Dec 29, 2014
- 1,717
- 7,419
- 2,679
- 63
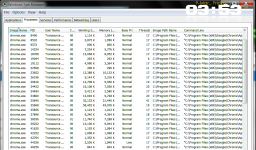
On one machine I noticed the PC was racing. It had been doing this for some time, but I wasn't aware because I have streaming video running behind the scenes much of the time on this one PC. Then I noticed that under the same conditions the problem wasn't present on another computer with the video running. That led me to be curious if there were some kind of crypto activity going on with a page. I shut down the video page and sure enough the processor was still racing, so then I really started to wonder.
Some things about this episode (there are lots of things):
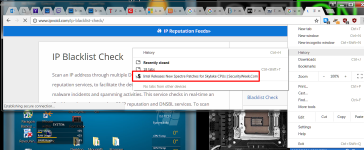
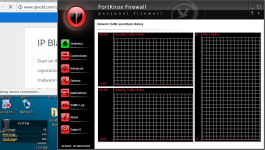
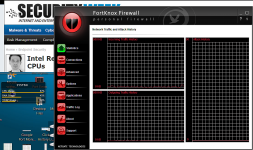
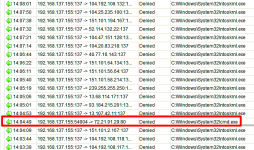
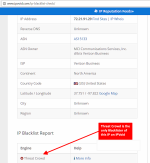
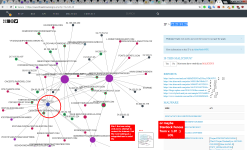
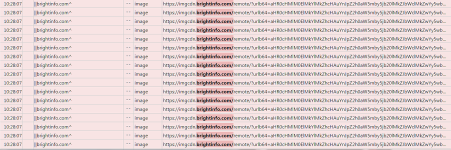
-I noticed an unusual IP listed in connections list in FortKnox Firewall on both PCs. It's a local type connection that o/c IPVoid returns no information for. This IP is 192.0.73.2:443. Anyone else see this when using Chrome or anything similar?
-My bandwidth is not affected by the processor usage, meaning no extra traffic is coming in or out of the PC over the internet. Glad for that.
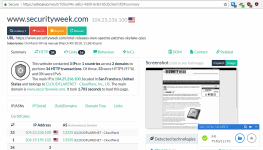
-The racing processor issue only happens with one page. It's a page I linked through a thread here.
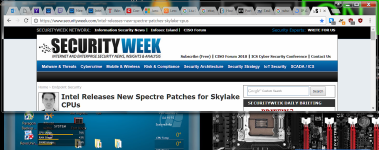
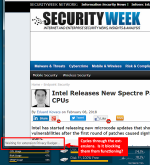
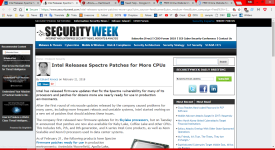
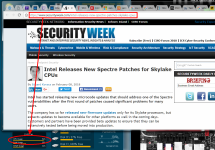
Intel Releases Spectre Patches for More CPUs
The first link in the first post titled "Skylake processors".
OK, so back to this episode. Because of the list of symptoms, I have some speculation, and I would like any input:
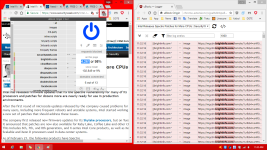
1. Only the single page on a single PC. It happens no matter how I link the page. However, it's not happening on any other page on the site or anywhere else. This is strange. This tab was open for probably two weeks, because of Meltdown and Spectre issues I have. So it almost seems like something hand picked this page to attempt to abuse from this PC or somehow. Again, traffic is normal...if the video is off it's nil, even with Chrome open. Weird.
2. Could this site be partially hacked as in given time (a link open for a long time), some kind of cryptominer can use the site and steal my processor bandwidth?
3. One thing I though of about a malicious activity that maybe exists, idk. I thought, OK everyone knows how Chrome updates. When it does, hashes change. Security programs notice and adjust o/c. Well, that in mind, could malware change files in Chrome when it updates and not be caught since the legit update had just happened (or is still happening) etc.? Imagining what could happen if some reverse engineered and altered files were placed in place of Chrome files. Like, you will help me infect sites for crypto etc. Kind of scary.
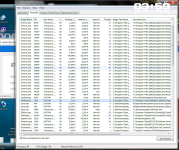
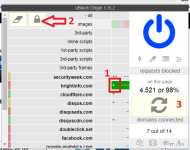
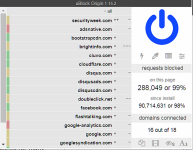
Guys FortKnox Firewall gets better with each minute I use the app. I am even using it with Comodo Firewall at the same time with both Firewalls running. So far no conflicts. The presentation takes I guess a couple of weeks to maybe a month to get used to, but then you start to learn what can be done with the Advanced rules. OK, no IP ranges, but I can block a single IP for all apps in a single rule etc. Also, I can monitor local if I am willing to enter 10-15 local addresses for allows in individual rules. Very nice. Still can monitor svchost spefically for other traffic by just setting it to ask. Same for kernel or any other vulnerable app.
Some things about this episode (there are lots of things):
-I noticed an unusual IP listed in connections list in FortKnox Firewall on both PCs. It's a local type connection that o/c IPVoid returns no information for. This IP is 192.0.73.2:443. Anyone else see this when using Chrome or anything similar?
-My bandwidth is not affected by the processor usage, meaning no extra traffic is coming in or out of the PC over the internet. Glad for that.
-The racing processor issue only happens with one page. It's a page I linked through a thread here.
Intel Releases Spectre Patches for More CPUs
The first link in the first post titled "Skylake processors".
OK, so back to this episode. Because of the list of symptoms, I have some speculation, and I would like any input:
1. Only the single page on a single PC. It happens no matter how I link the page. However, it's not happening on any other page on the site or anywhere else. This is strange. This tab was open for probably two weeks, because of Meltdown and Spectre issues I have. So it almost seems like something hand picked this page to attempt to abuse from this PC or somehow. Again, traffic is normal...if the video is off it's nil, even with Chrome open. Weird.


2. Could this site be partially hacked as in given time (a link open for a long time), some kind of cryptominer can use the site and steal my processor bandwidth?
3. One thing I though of about a malicious activity that maybe exists, idk. I thought, OK everyone knows how Chrome updates. When it does, hashes change. Security programs notice and adjust o/c. Well, that in mind, could malware change files in Chrome when it updates and not be caught since the legit update had just happened (or is still happening) etc.? Imagining what could happen if some reverse engineered and altered files were placed in place of Chrome files. Like, you will help me infect sites for crypto etc. Kind of scary.
Guys FortKnox Firewall gets better with each minute I use the app. I am even using it with Comodo Firewall at the same time with both Firewalls running. So far no conflicts. The presentation takes I guess a couple of weeks to maybe a month to get used to, but then you start to learn what can be done with the Advanced rules. OK, no IP ranges, but I can block a single IP for all apps in a single rule etc. Also, I can monitor local if I am willing to enter 10-15 local addresses for allows in individual rules. Very nice. Still can monitor svchost spefically for other traffic by just setting it to ask. Same for kernel or any other vulnerable app.
Last edited: