A pair of creative hackers have built a device capable of connecting to wireless networks and altering the Web content users access, as part of a project to demonstrate how news can be manipulated.
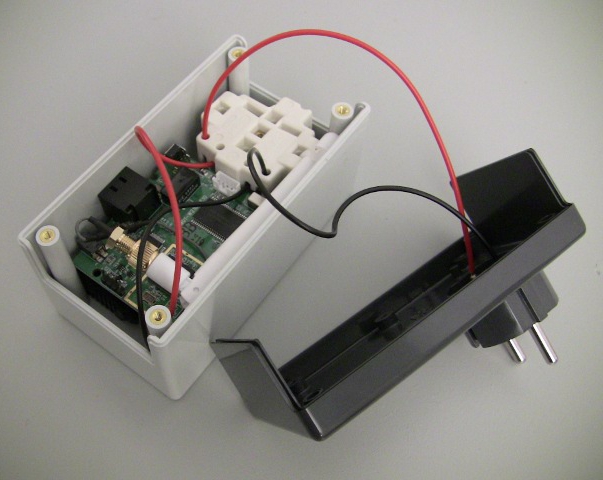
The device mimics a pass-through power socket, making it hard to observe, and has already been tested in cafe shops in Berlin, where its creators Julian Oliver and Danja Vasiliev are based.
Inside the 12 cm long casing there's a small circuit board with an Atheros chipset and an antenna. It's running a customized Linux distribution designed for embedded systems.
When powered on, the device automatically searches for wireless networks and connects using passwords supplied in advance.
A reverse SSH tunnel is established with a remote server, allowing attackers to control the device from a distance.
The tunnel uses 2048-bit encryption and is routed over Tor nodes, making it virtually impossible to determine where the attackers are located.
The device launches ARP (Address Resolution Protocol) spoofing attacks in order to position itself as a gateway between the other wireless clients and the real router.
This allows attackers to manipulate content passing through it. The research project, dubbed "Newstweek," demonstrates this by altering news headlines from popular websites.
More details - link
The device mimics a pass-through power socket, making it hard to observe, and has already been tested in cafe shops in Berlin, where its creators Julian Oliver and Danja Vasiliev are based.
Inside the 12 cm long casing there's a small circuit board with an Atheros chipset and an antenna. It's running a customized Linux distribution designed for embedded systems.

When powered on, the device automatically searches for wireless networks and connects using passwords supplied in advance.
A reverse SSH tunnel is established with a remote server, allowing attackers to control the device from a distance.
The tunnel uses 2048-bit encryption and is routed over Tor nodes, making it virtually impossible to determine where the attackers are located.
The device launches ARP (Address Resolution Protocol) spoofing attacks in order to position itself as a gateway between the other wireless clients and the real router.
This allows attackers to manipulate content passing through it. The research project, dubbed "Newstweek," demonstrates this by altering news headlines from popular websites.
More details - link