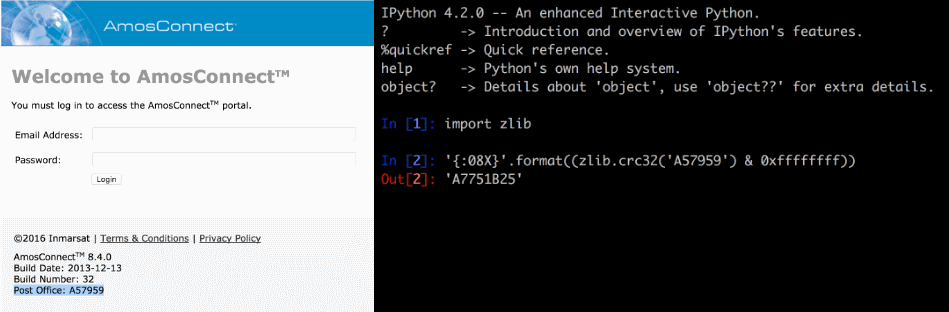
A popular satellite communications (SATCOM) system installed on ships across the world is affected by two serious security flaws — a hidden backdoor account with full system privileges access and an SQL injection in the login form.
These vulnerabilities affect the AmosConnect 8 designed and sold by Stratos Global, a company acquired in 2009 by mobile satellite services firm Inmarsat Group.
Flaws won't receive patches
The two vulnerabilities are part of a report released today by cyber-security and penetration testing firm IOActive, but they won't receive any patches because Stratos retired the AtmosConnect 8 product just months before, in June 2017, according to an
end-of-life announcement on the company's site.
"Effective 30 June 2017 we will be discontinuing the availability and support of AmosConnect 8," the company said. "AmosConnect 7 will continue as the primary product offering."
The product's deprecation was not the direct consequence of the discovery of these two flaws but was announced back in November 2016.
AtmosConnect 8 boxes are SATCOM systems that are specifically designed to work on ships, oil rigs, and other isolated maritime environments.
The system provides Internet connectivity to ships via a satellite connection. AtmosConnect 8 is a password-protected platform that a ship's crew can use to access on-ship Internet services.