"Microsoft hides file extensions in Windows by default even though it's a security risk that is commonly abused by phishing emails and malware distributors to trick people into opening malicious files.
A file extension is the letters immediately shown after the last period in a file name and is used by the operating system to determine what program is used to open, view, and utilize the file.
For example, the file report.txt has an extension of .txt, which is associated with the Windows Notepad program to open and view its contents.
By default, Microsoft decides to hide file extensions in Windows so that a file named 'report.txt' is simply shown in File Explorer as 'report'.
The original reason for this was probably to make it less confusing to users, but regardless of the reason, it is a security risk that attackers abuse.
Windows default settings abused by attackers
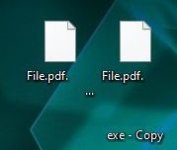
To illustrate how the hiding of file extensions is a security risk, let's take a look at the following folder containing two files.
With file extensions disabled, they look like the same PDF file as they both have the same name and the same icon.
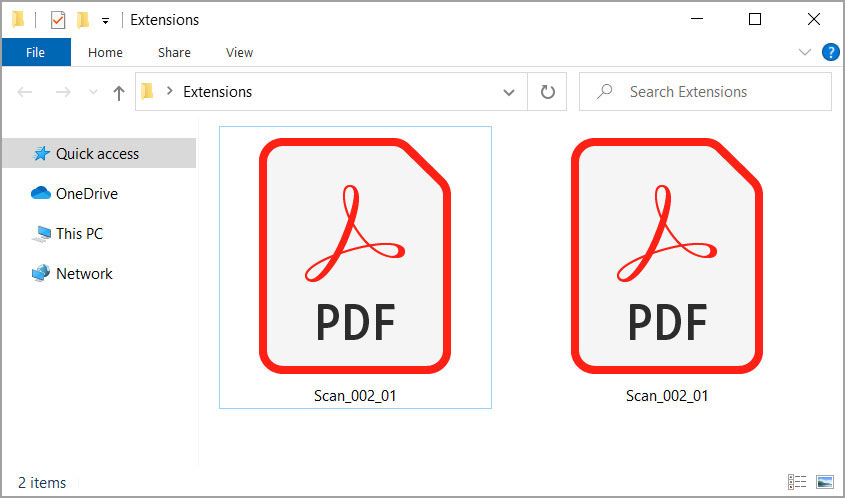
File extensions are hidden in Windows
If we enable extensions, though, we quickly see that these are two different files with one being a PDF as expected, but the other being an executable file that uses a PDF icon.
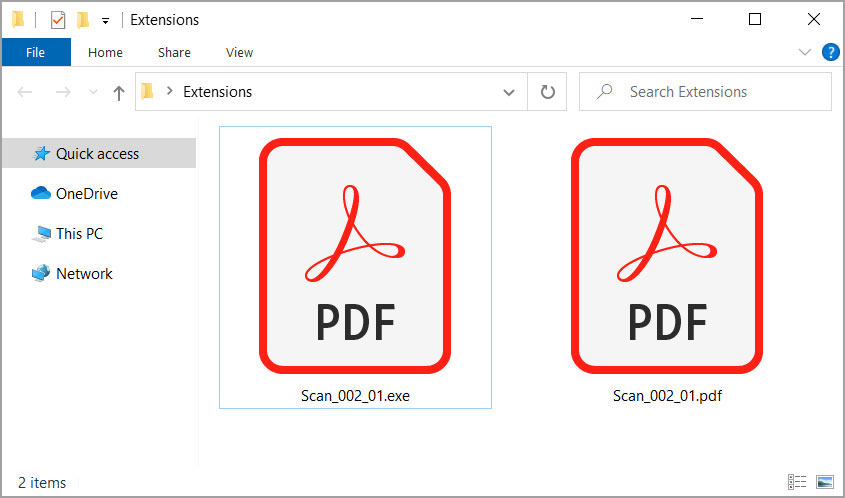
File extensions are now enabled
In this case, the malware executable purposely used the PDF icon normally shown by Adobe Reader to trick users who have file extensions disable that it is a PDF file.
This is not to say strange PDFs you receive via email cannot be a risk, but receiving executables disguised as PDFs should definitely raise more alarms."
......
A file extension is the letters immediately shown after the last period in a file name and is used by the operating system to determine what program is used to open, view, and utilize the file.
For example, the file report.txt has an extension of .txt, which is associated with the Windows Notepad program to open and view its contents.
By default, Microsoft decides to hide file extensions in Windows so that a file named 'report.txt' is simply shown in File Explorer as 'report'.
The original reason for this was probably to make it less confusing to users, but regardless of the reason, it is a security risk that attackers abuse.
Windows default settings abused by attackers
To illustrate how the hiding of file extensions is a security risk, let's take a look at the following folder containing two files.
With file extensions disabled, they look like the same PDF file as they both have the same name and the same icon.

File extensions are hidden in Windows
If we enable extensions, though, we quickly see that these are two different files with one being a PDF as expected, but the other being an executable file that uses a PDF icon.

File extensions are now enabled
In this case, the malware executable purposely used the PDF icon normally shown by Adobe Reader to trick users who have file extensions disable that it is a PDF file.
This is not to say strange PDFs you receive via email cannot be a risk, but receiving executables disguised as PDFs should definitely raise more alarms."
......