Hi everybody, funny how you see a new thread of mine after some time and it's a story of how I suffered what I thought I'd never suffer again, since I've been malware free for more than a decade. I'm sharing this with you to let you know, and
specially let novice users how careful we must be, since it's not even hard to get infected.
Today I commited a mistake. One single mistake, that costed me an infection, even when I thought I was truly protected. May this be a lesson for everybody, that if you, the user, are not careful enough, there will not be enough software to protect you.
HOW IT STARTED
I had to download a specific software today. Since the version I needed to install wasn't on the official site anymore, I headed to a Youtube video that would let me download it via Mediafire or MEGA.
I clicked the video,
made a quick check of it, checked comments to see what users said about this download, and since everything was positive,
I downloaded the file.
- Norton Antivirus didn't pop when downloaded, so the first test was done.
- A right click context scan didn't show malware, so second test was done.
- I decided not to upload the file to VirusTotal, since Norton came clean and Youtube comments were positive.
THE INFECTION
I launched the executable file, and after some seconds, nothing happened. That's when I knew
something was wrong. I immediately opened Process Explorer and Task Manager to see any possible suspicious process, and before these two even open,
my theory became a reality.
View attachment 271441
Norton detected suspicious activity too. But here's the catch.
Norton didn't detect the malware process. What we're seeing up there is Norton Intrusion Prevention System, which is basically like a firewall. It scans network traffic for attack signatures, such as social threats and outbound attacks, that identify attempts to exploit vulnerabilities in your operating system or in a program that you use.
And here's the other catch.
The malware was still active in my system. and we had a loop. The malware process was a type of trojan that steals all the system's stored passwords. It was when this malware tried to contact home that Norton realised this was supicious activity and realised what was going on. But here are three problems:
- Norton wasn't smart enough to quarantine the file calling constantly home
- Each network connection malware tried to do was blocked, but malware was still active
- Neither Norton's "smart" or full scan were able to detect the malware, even when it was triggering Norton's IPS
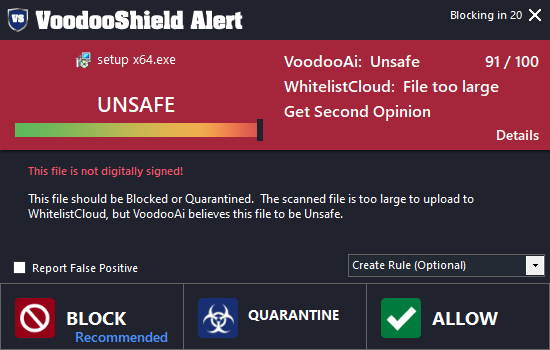
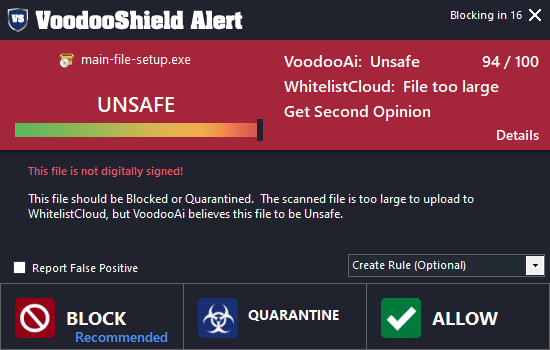
Wanna guess who did detect it?
RESOLUTION AND CONCLUSSION
Yup, probably guessed right.
View attachment 271442View attachment 271443
Long story short; malware neutralized, no information stolen and day saved.
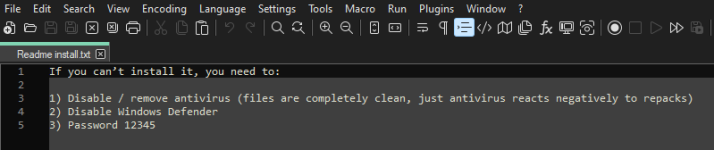
Once this was over, I headed to the Youtube video where I downloaded the file, and realised the mistake I had made:
everything was fake.
- Unknown author
- Literally posted 6 hours ago and already had 47 comments
- Video title was in spanish and all coments in english
- All comments were positive and posted at literally the same time
Yes, the cybercriminal had uploaded a fake video, paid for almost 50 bot comments and I slipped right in. I wasn't careful enough. I might be getting old.
Hopefully this is a lesson for everybody, most specially for me, that mistakes can be made and can cost us a lot. Luckily, I was spared to live some years more.
Also, after the semi-failure I saw today in Norton's protection, I might be re-thinking my comeback to Kaspersky.
 .
.