L
LabZero
Thread author
Hello.
As already mentioned, the only malware scan does not represent the actual detection capability of an antivirus/antimalware.
Because all security technologies are enabled, it is necessary to launch the malware.
Many things here are already known but it's always better to remember them.
Before we begin, we need to create a complete image of the system to recover quickly and smoothly the initial state if malware bypass the virtual machine (extremely difficult, but prevention is better ).
).
Some good backup/restore apps.
Aomei
Paragon B&R Free
I will not explain how to backup because it is not the reason for this thread.
To be able to test safely it is necessary to have a dedicated PC without data or personal information that might be shared by maware.
Alternately it is necessary to use a virtual machine like VirtualBox or VMware.
Virtual Machine
A virtual machine is a PC emulated within a host operating system that can run another system.
Example: I can use Windows 10 as native host system, and start a virtual machine running Windows XP; so XP is the guest system. The advantage: you really see the effects of a malware while remaining within the virtual operating system.
However the best results are obtained in the real/physical system.
My favorite is Virtualbox
Once installed the system, extensions and guest additions (driver) be careful not to create links (network drives or otherwise) between the host system and virtualized (guest).
To avoid having to clean up, or at least not risk leaving any traces of malware, you can create a snapshot of the virtual disk so you will be sure that the virtual system will always return in the initial state : How to Save Time by Using Snapshots in VirtualBox
Light virtualization
Shadow Defender create a virtual copy of the system partition (light virtualization) where you can test malware and applications ... on reboot it will be as if it never happened.
Warning: I highly recommend, in lightweight virtualization, to disconnect the internet or hide and encrypt your personal data (for example using Wise Hide Folder) during your malware test in order to avoid loss of data that may be shared by the malware itself.
Testing
Many samples are in. bin extension (short for "binary") and the best antivirus should detect the malware in this extension but it is better to rename the file with the correct extension: .exe, .doc, . vbs, . js, etc.
For example on Malwr you can see the actual extension on the samples:
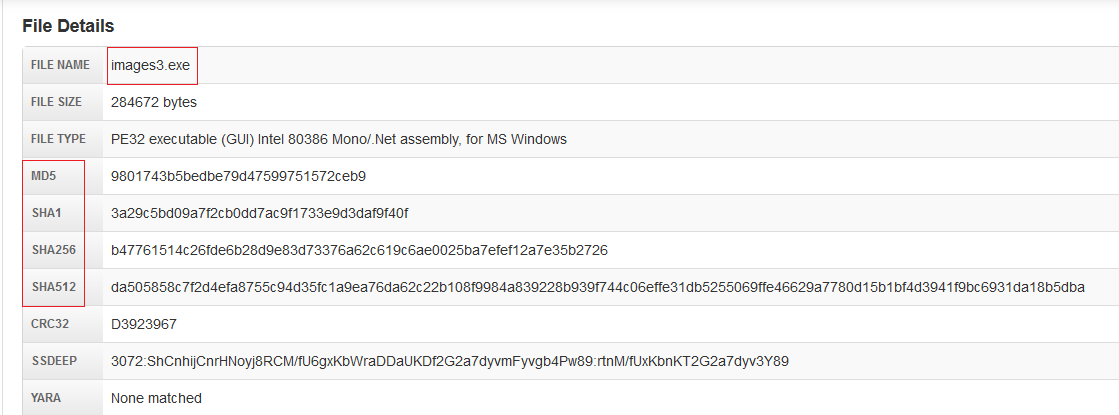
Other important information: hash to uniquely identify a file, which is important to avoid duplicate samples in Hub.
Many malware have "dropped files", then it is very important to start the malware because the primary file may not be recognized but if the file appears to be designed to install (or ' drop ') a second file, the skipped file could trigger a detection.
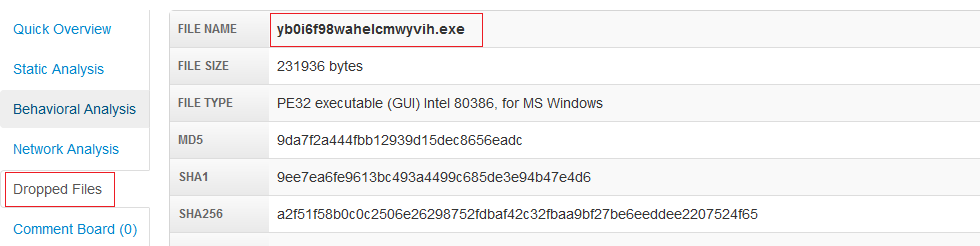
So, the next step is to launch the malware running the dynamic detection of antivirus.
If the antivirus does not detect any threat during the scan or the malware starts, it is possible to start a scan of the infected system to determine if security problems are found at this level.
So, good testing
As already mentioned, the only malware scan does not represent the actual detection capability of an antivirus/antimalware.
Because all security technologies are enabled, it is necessary to launch the malware.
Many things here are already known but it's always better to remember them.
Before we begin, we need to create a complete image of the system to recover quickly and smoothly the initial state if malware bypass the virtual machine (extremely difficult, but prevention is better
Some good backup/restore apps.
Aomei
Paragon B&R Free
I will not explain how to backup because it is not the reason for this thread.
To be able to test safely it is necessary to have a dedicated PC without data or personal information that might be shared by maware.
Alternately it is necessary to use a virtual machine like VirtualBox or VMware.
Virtual Machine
A virtual machine is a PC emulated within a host operating system that can run another system.
Example: I can use Windows 10 as native host system, and start a virtual machine running Windows XP; so XP is the guest system. The advantage: you really see the effects of a malware while remaining within the virtual operating system.
However the best results are obtained in the real/physical system.
My favorite is Virtualbox
Once installed the system, extensions and guest additions (driver) be careful not to create links (network drives or otherwise) between the host system and virtualized (guest).
To avoid having to clean up, or at least not risk leaving any traces of malware, you can create a snapshot of the virtual disk so you will be sure that the virtual system will always return in the initial state : How to Save Time by Using Snapshots in VirtualBox
Light virtualization
Shadow Defender create a virtual copy of the system partition (light virtualization) where you can test malware and applications ... on reboot it will be as if it never happened.
Warning: I highly recommend, in lightweight virtualization, to disconnect the internet or hide and encrypt your personal data (for example using Wise Hide Folder) during your malware test in order to avoid loss of data that may be shared by the malware itself.
Testing
Many samples are in. bin extension (short for "binary") and the best antivirus should detect the malware in this extension but it is better to rename the file with the correct extension: .exe, .doc, . vbs, . js, etc.
For example on Malwr you can see the actual extension on the samples:
Other important information: hash to uniquely identify a file, which is important to avoid duplicate samples in Hub.
Many malware have "dropped files", then it is very important to start the malware because the primary file may not be recognized but if the file appears to be designed to install (or ' drop ') a second file, the skipped file could trigger a detection.
So, the next step is to launch the malware running the dynamic detection of antivirus.
If the antivirus does not detect any threat during the scan or the malware starts, it is possible to start a scan of the infected system to determine if security problems are found at this level.
So, good testing