F
ForgottenSeer 85179
Thread author
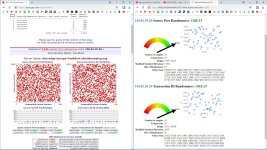
First, we check DNS leaks:
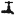 dnsleaktest.com
dnsleaktest.com
Then we test DNSSEC:
Connection test (This website test other stuff too)
With that site, we make some different tests (take a while):
 tenta.com
tenta.com
And last but not least, we test the security:
 www.grc.com
www.grc.com
 www.dns-oarc.net
www.dns-oarc.net
That's it.
You can share then your result here.
Also it's important that your DNS:
- don't has any leaks
- support DNSSEC
and have as good as possible these results on grc.com:

and on dns-oarc.net:

DNS leak test
Then we test DNSSEC:
Connection test (This website test other stuff too)
With that site, we make some different tests (take a while):
Browser Privacy - Test IP address, DNS, VPN leaks. Fast & no ads. Protect your online privacy.
Test your browser for data leaks, such as IP address, advanced DNS test, WebRTC leak test, IP geolocation, http headers and device information. Designed for mobile and desktop.
And last but not least, we test the security:
GRC | DNS Nameserver Spoofability Test
GRC's DNS Nameserver spoofability testing facility
Web-based DNS Randomness Test | DNS-OARC
That's it.
You can share then your result here.
Also it's important that your DNS:
- don't has any leaks
- support DNSSEC
and have as good as possible these results on grc.com:

and on dns-oarc.net: