An increasing number of antiviruses and network appliances intercept TLS connections to gain visibility into encrypted traffic, but in many cases this weakens connection security and introduces vulnerabilities, according to a new study.
The study, focusing on the security impact of HTTPS interception, was carried out last summer by researchers at Mozilla, Google, CloudFlare, the University of Michigan, the University of Illinois Urbana-Champaign, the University of California Berkeley, and the International Computer Science Institute.
Experts have analyzed the TLS handshakes associated with web browsers, security products and malware, and created a set of heuristics designed to allow web servers to detect HTTPS interception and identify the product responsible.
Tests were conducted by deploying these heuristics on Mozilla’s Firefox update servers, the CloudFlare content distribution network (CDN), and some major e-commerce websites. The analysis showed that 4% of the Firefox connections, 6.2% of the e-commerce connections, and nearly 11% of US-based CloudFlare connections were intercepted.
Worryingly, 97% of the Firefox, 54% of the CloudFlare and 32% of the e-commerce connections that were intercepted became less secure. More than 62% of the middlebox connections were weakened and over 58% had severe vulnerabilities.
“Alarmingly, not only did intercepted connections use weaker cryptographic algorithms, but 10–40% advertised support for known-broken ciphers that would allow an active man-in-the-middle attacker to later intercept, downgrade, and decrypt the connection,” researchers said in their report.
The list of middlebox vendors whose products were tested includes A10 Networks, Blue Coat, Barracuda, Check Point, Cisco, Forcepoint, Fortinet, Juniper Networks, Microsoft, Sophos, Untangle and WebTitan. Only the Blue Coat product received an A grade (optimal TLS connection equivalent to modern browsers), while the others received a C (contains known vulnerability) or F (severely broken connection vulnerable to MitM attacks).
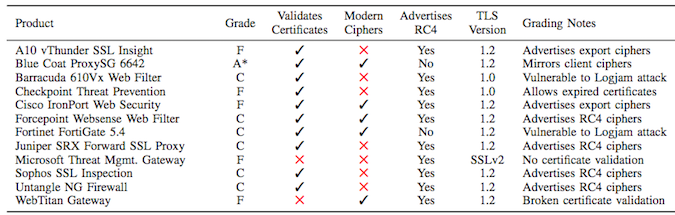
The antiviruses analyzed in the study include Windows and Mac products from Avast, AVG, Bitdefender, Bullguard, CYBERsitter, Dr. Web, ESET, G DATA, Kaspersky, KinderGate, Net Nanny, PC Pandora and Qustodio. Only two of the tested Avast products received an A grade.
The researchers said they reported their findings to the affected vendors, and while some of them addressed the issues or they plan on doing so, others ignored them or refused to update their products and shifted responsibility to customers.
The study was published shortly after a member of the Chrome security team and a former Mozilla employee said the only antivirus that is not terrible is the one made by Microsoft.