- Apr 25, 2013
- 5,355
VPN users are facing a massive security flaw as websites can easily see their home IP-addresses through WebRTC. The vulnerability is limited to supporting browsers such as Firefox and Chrome, and appears to affect Windows users only. Luckily the security hole is relatively easy to fix.
The Snowden revelations have made it clear that online privacy is certainly not a given.
Just a few days ago we learned that the Canadian Government tracked visitors of dozens of popular file-sharing sites.
As these stories make headlines around the world interest in anonymity services such as VPNs has increased, as even regular Internet users don’t like the idea of being spied on.
Unfortunately, even the best VPN services can’t guarantee to be 100% secure. This week a very concerning security flaw revealed that it’s easy to see the real IP-addresses of many VPN users through a WebRTC feature.
With a few lines of code websites can make requests to STUN servers and log users’ VPN IP-address and the “hidden” home IP-address, as well as local network addresses.
The vulnerability affects WebRTC-supporting browsers including Firefox and Chrome and appears to be limited to Windows machines.
A demo published on GitHub by developer Daniel Roesler allows people to check if they are affected by the security flaw.
IP-address leak
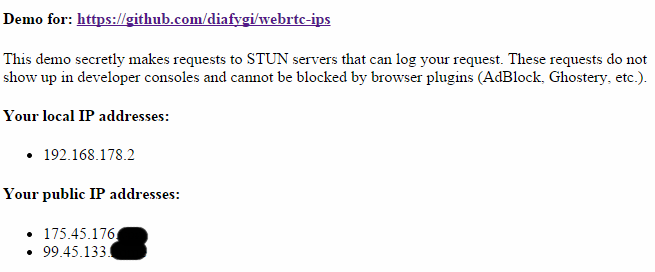
The demo claims that browser plugins can’t block the vulnerability, but luckily this isn’t entirely true. There are several easy fixes available to patch the security hole.
Chrome users can install the WebRTC block extension or ScriptSafe, which both reportedly block the vulnerability.
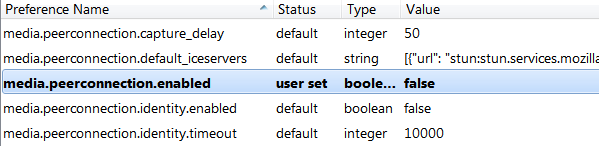
Firefox users should be able to block the request with the NoScript addon. Alternatively, they can type “about:config” in the address bar and set the “media.peerconnection.enabled” setting to false.
TF asked various VPN providers to share their thoughts and tips on the vulnerability.Private Internet Access told us that the are currently investigating the issue to see what they can do on their end to address it. (Update: PIA published an article on the issue today)
TorGuard informed us that they issued a warning in a blog post along with instructions on how to stop the browser leak. Ben Van Der Pelt, TorGuard’s CEO, further informed us that tunneling the VPN through a router is another fix.
“Perhaps the best way to be protected from WebRTC and similar vulnerabilities is to run the VPN tunnel directly on the router. This allows the user to be connected to a VPN directly via Wi-Fi, leaving no possibility of a rogue script bypassing a software VPN tunnel and finding one’s real IP,” Van der Pelt says.
“During our testing Windows users who were connected by way of a VPN router were not vulnerable to WebRTC IP leaks even without any browser fixes,” he adds.
While the fixes above are all reported to work, the leak is a reminder that anonymity should never be taken for granted.
As is often the case with these type of vulnerabilities, VPN and proxy users should regularly check if their connection is secure. This also includes testing against DNS leaks and proxy vulnerabilities.
Source
The Snowden revelations have made it clear that online privacy is certainly not a given.
Just a few days ago we learned that the Canadian Government tracked visitors of dozens of popular file-sharing sites.
As these stories make headlines around the world interest in anonymity services such as VPNs has increased, as even regular Internet users don’t like the idea of being spied on.
Unfortunately, even the best VPN services can’t guarantee to be 100% secure. This week a very concerning security flaw revealed that it’s easy to see the real IP-addresses of many VPN users through a WebRTC feature.
With a few lines of code websites can make requests to STUN servers and log users’ VPN IP-address and the “hidden” home IP-address, as well as local network addresses.
The vulnerability affects WebRTC-supporting browsers including Firefox and Chrome and appears to be limited to Windows machines.
A demo published on GitHub by developer Daniel Roesler allows people to check if they are affected by the security flaw.
IP-address leak

The demo claims that browser plugins can’t block the vulnerability, but luckily this isn’t entirely true. There are several easy fixes available to patch the security hole.
Chrome users can install the WebRTC block extension or ScriptSafe, which both reportedly block the vulnerability.
Firefox users should be able to block the request with the NoScript addon. Alternatively, they can type “about:config” in the address bar and set the “media.peerconnection.enabled” setting to false.

TF asked various VPN providers to share their thoughts and tips on the vulnerability.Private Internet Access told us that the are currently investigating the issue to see what they can do on their end to address it. (Update: PIA published an article on the issue today)
TorGuard informed us that they issued a warning in a blog post along with instructions on how to stop the browser leak. Ben Van Der Pelt, TorGuard’s CEO, further informed us that tunneling the VPN through a router is another fix.
“Perhaps the best way to be protected from WebRTC and similar vulnerabilities is to run the VPN tunnel directly on the router. This allows the user to be connected to a VPN directly via Wi-Fi, leaving no possibility of a rogue script bypassing a software VPN tunnel and finding one’s real IP,” Van der Pelt says.
“During our testing Windows users who were connected by way of a VPN router were not vulnerable to WebRTC IP leaks even without any browser fixes,” he adds.
While the fixes above are all reported to work, the leak is a reminder that anonymity should never be taken for granted.
As is often the case with these type of vulnerabilities, VPN and proxy users should regularly check if their connection is secure. This also includes testing against DNS leaks and proxy vulnerabilities.
Source

