silversurfer
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Malware Hunter
Well-known
- Aug 17, 2014
- 10,178
A recent IcedID malware attack enabled the threat actor to compromise the Active Directory domain of an unnamed target less than 24 hours after gaining initial access, while also borrowing techniques from other groups like Conti to meet its goals.
"Throughout the attack, the attacker followed a routine of recon commands, credential theft, lateral movement by abusing Windows protocols, and executing Cobalt Strike on the newly compromised host," Cybereason researchers said in a report published this week.
The intrusion detailed by Cybereason is no different in that the infection chain begins with an ISO image file contained within a ZIP archive that culminates in the execution of the IcedID payload.
The malware then establishes persistence on the host via a scheduled task and communicates with a remote server to download next-stage payloads, including Cobalt Strike Beacon for follow-on reconnaissance activity.
It also carries out lateral movement across the network and executes the same Cobalt Strike Beacon in all those workstations, and then proceeds to install Atera agent, a legitimate remote administration tool, as a redundant remote access mechanism.
"Utilizing IT tools like this allows attackers to create an additional 'backdoor' for themselves in the event their initial persistence mechanisms are discovered and remediated," the researchers said. "These tools are less likely to be detected by antivirus or EDR and are also more likely to be written off as false positives."
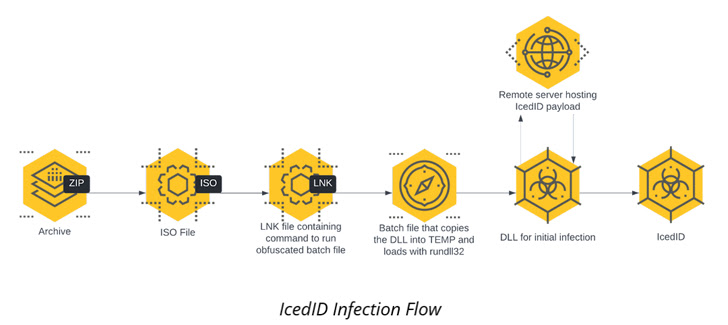

IcedID Malware Strikes Again: Active Directory Domain Compromised in Under 24 Hours
Beware of IcedID malware - it's using attack techniques borrowed from other hackers to quickly compromise Active Directory domains
