L
LabZero
Thread author
Source : my school informations
Hello,
Usually do not have access to the source code of the malware, then we must carry out an analysis of the binary file (the executable file), where static analysis through the disassembler there has provided enough information, you need to use a debugger, to be able to control the low-level code(assembly).
The assembly is a low-level language, very near to the machine language.
In machine language, specific sequences of bits are associated with basic istructions.
Assembly language mnemonic instruction associated with these opcodes (opcodes).
For each different architecture exists then a different Language Assembly, we are going to the
intel x 86 architecture to 32 bits.
The topic is very extended, we will see more important features.
The registers
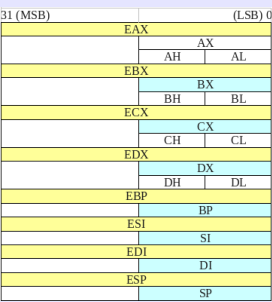
The registers are "containers", as the language of high level variables.
The first eight logs called "General-purpose registers,"can be used in a generic way, but also have specific uses.
EAX: accumulator
EBX: data pointer
ECX: counter
EDX: i/o pointer
ESI: source pointer for string operations
EDI: target pointer for string operations
ESP: stack pointer
EBP: data pointer onto the stack
EIP is a special register contains the address of the next statement must be executed.
EFLAGS is a registry that contains flags, us concern are the status flag and flag df.
Status flags indicate the result of arithmetic operations, those that most are used :
CF, carry flag-indicates whether an instruction had to carry a bit.
ZF, zero flag: indicates if the result is zero.
SF, sign flag: indicates whether the result is positive or negative.
There is also a flag DF, direction controls the direction of read/write for instructions on
strings.
Is a structure of type LIFO (Last-In, first-out) in memory, the stack pointer points to this memory area, which usually is manipulated through the push and pop istructions.
In addition to contain data also contains the return address of the call.
In fact, when you run a CALL statement to call a sub procedure, you put the address of the stack next statement with respect to the call. In this way, once the procedure, through the RET, the program resumes running from the next statement.
The instructions
In the Intel syntax, the first operand is the destination, the according to the data source.
MOV EAX, EBX, ebx content copy in eax.
MOV EAX, [EBX] copy the dword pointed to by the address contained inebx in eax.
JMP $1234, is an unconditional jump to the address 1234.
CMP EAX, EBX compares the contents of EAX and EBX, and edit the status flags accordingly.
There are also conditional jumps the jump is executed or not according to the corresponding flag.
JNZ/JNE jumps only if the result of the last operation is different (if eax and ebx in cmp are different).
JLE, jump if less than or equal.
Well. These are the main information about the assembly language.
This argument is difficult, but I really like because it allows you to understand the main malware's processes and functions.
Enjoy with Malware Analysis
Hello,
Usually do not have access to the source code of the malware, then we must carry out an analysis of the binary file (the executable file), where static analysis through the disassembler there has provided enough information, you need to use a debugger, to be able to control the low-level code(assembly).
The assembly is a low-level language, very near to the machine language.
In machine language, specific sequences of bits are associated with basic istructions.
Assembly language mnemonic instruction associated with these opcodes (opcodes).
For each different architecture exists then a different Language Assembly, we are going to the
intel x 86 architecture to 32 bits.
The topic is very extended, we will see more important features.
The registers
The registers are "containers", as the language of high level variables.
The first eight logs called "General-purpose registers,"can be used in a generic way, but also have specific uses.
EAX: accumulator
EBX: data pointer
ECX: counter
EDX: i/o pointer
ESI: source pointer for string operations
EDI: target pointer for string operations
ESP: stack pointer
EBP: data pointer onto the stack
EIP is a special register contains the address of the next statement must be executed.
EFLAGS is a registry that contains flags, us concern are the status flag and flag df.
Status flags indicate the result of arithmetic operations, those that most are used :
CF, carry flag-indicates whether an instruction had to carry a bit.
ZF, zero flag: indicates if the result is zero.
SF, sign flag: indicates whether the result is positive or negative.
There is also a flag DF, direction controls the direction of read/write for instructions on
strings.
Is a structure of type LIFO (Last-In, first-out) in memory, the stack pointer points to this memory area, which usually is manipulated through the push and pop istructions.
In addition to contain data also contains the return address of the call.
In fact, when you run a CALL statement to call a sub procedure, you put the address of the stack next statement with respect to the call. In this way, once the procedure, through the RET, the program resumes running from the next statement.
The instructions
In the Intel syntax, the first operand is the destination, the according to the data source.
MOV EAX, EBX, ebx content copy in eax.
MOV EAX, [EBX] copy the dword pointed to by the address contained inebx in eax.
JMP $1234, is an unconditional jump to the address 1234.
CMP EAX, EBX compares the contents of EAX and EBX, and edit the status flags accordingly.
There are also conditional jumps the jump is executed or not according to the corresponding flag.
JNZ/JNE jumps only if the result of the last operation is different (if eax and ebx in cmp are different).
JLE, jump if less than or equal.
Well. These are the main information about the assembly language.
This argument is difficult, but I really like because it allows you to understand the main malware's processes and functions.
Enjoy with Malware Analysis
Last edited by a moderator: