This script is detected only by Kaspersky; the rest of major vendors didn't flag it as malicious?
Should I use it?

Should I use it?
It's from the officialy site directly.If you downloaded it from the official site (which I won't link as some might say it's piracy), it's completely safe. I'll recommend you to use PowerShell command from the official site instead running the script manually.
I'm repeating the check by virustotal daily waiting for that; seems the rest of vendors are still in hibernation.Cracks allowed when they don't harm the system, but this is different... and probably soon that script will be detected by additional antivirus firms...
This isn't even a crack. This is a script that's taking advantage of Microsoft's own activation system and activates Windows using generic keys Microsoft themselves published on their website. It simply fools Microsoft activation servers by using installation ID of genuine key to obtain a digital license, and does everything without any 3rd party component.Cracks allowed when they don't harm the system, but this is different... and probably soon that script will be detected by additional antivirus firms...
Don't worry, they aren't hibernating. They simply have no reason to detect clean and safe script. It doesn't do anything your Windows installation doesn't do during and after installation. Though, I'd expect Microsoft to flag it as malicious, but even they don't want to do that. So much... about piracy.I'm repeating the check by virustotal daily waiting for that; seems the rest of vendors are still in hibernation.
So it can be considered as a false positive by Kaspersky?This isn't even a crack. This is a script that's taking advantage of Microsoft's own activation system and activates Windows using generic keys Microsoft themselves published on their website. It simply fools Microsoft activation servers by using installation ID of genuine key to obtain a digital license, and does everything without any 3rd party component.
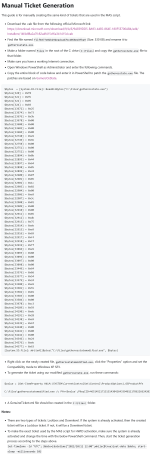
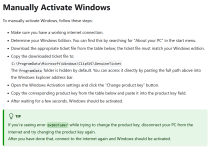
If you don't trust the script, they wrote a guide how to do it manually:
View attachment 288504 View attachment 288505
The script was first released in 2015, not long since Windows 10 was released. Ever since the first version it is hosted on Github, Azure DevOps and their own, self-hosted git. Heck, even Copilot recommended you to activate Windows this way.
Antivirus didn't detect it for 10 years, why would they suddenly started detecting it now? It's not like it's very unpopular tool. Pretty much everyone I know is using it.
Don't worry, they aren't hibernating. They simply have no reason to detect clean and safe script. It doesn't do anything your Windows installation doesn't do during and after installation.
It only hacks MicrosoftI know the script, still, it is a "hack tool"...
It bit my arm!This script is detected only by Kaspersky; the rest of major vendors didn't flag it as malicious?
Should I use it?View attachment 288502
Completely.So it can be considered as a false positive by Kaspersky?
It certainly doesn't do that. The way it works is script contacts Microsoft's servers saying "Hey! I have a totally legit key I totally bought in a totally real shop. Can I get a digital license?" and Microsoft's servers reply "I don't care where you got it, and how you got it, here's your permanent digital license you asked for". *boom* your Windows has 100% legit digital license.It only hacks Microsoft
Microsoft don't care because it want Windows to be the predominant OS worldwide; revenue comes from corporate sectorCompletely.
Judging by the "threat" name, I'd say Kaspersky is bothered by KMS activation script (no one uses today). Though, activating Windows through KMS is also completely legal. They even created a guide how to create your own KMS (Key Management Service) server.
You could try reporting it to Kaspersky, but I doubt they'll care enough to mark the script safe.
It certainly doesn't do that. The way it works is script contacts Microsoft servers saying "Hey! I have a totally legit key I totally bought in a real shop. Can I get a digital license?" and Microsoft's servers reply "I don't care where you got it, and how you got it, here's your permanent digital license you asked for". *boom* your Windows has 100% legit digital license.
Exactly! I mean, they are still earning money on users by including ads, sponsored apps and telemetry. You're paying for Windows by using it. Bleeping Computer asked Microsoft about their support agents using MAS for activating troubled systems and they said it's totally against their policy and won't happen again. They still refuse to take the code down from their servers though.Microsoft don't care because it want Windows to be the predominant OS worldwide; revenue comes from corporate sector

For home sector, they get their money from your data, just as GoogleExactly! I mean, they are still earning money on users by including ads, sponsored apps and telemetry. You're paying for Windows by using it. Bleeping Computer asked Microsoft about their support agents using MAS for activating troubled systems and they said it's totally against their policy and won't happen again. They still refuse to take the code down from their servers though.

Microsoft support 'cracks' Windows for customer after activation fails
In an unexpected twist, a Microsoft support engineer resorted to running an unofficial 'crack' on a customer's Windows PC after a genuine copy of the operating system failed to activate normally. It seems, this isn't the first time either that a Microsoft support professional has employed such...www.bleepingcomputer.com
After starting to use IoT LTSC versions, I didn't come back to Pro, or even EntThis must be a rather new signature on this tool by Kaspersky. This one never in its existence as far as I can remember was detected by Kaspersky. Even ESET whose PUA (not PUP) detection is quite aggressive doesn't detect this.
As mentioned by @Marko :) you should use the PowerShell command instead. BTW, I even used this tool to change my Windows edition from Pro to Enterprise because only in editions like Enterprise and Education, the group policy to disable start menu's recommend section works
Stop pirating software.This script is detected only by Kaspersky; the rest of major vendors didn't flag it as malicious?
Should I use it?View attachment 288502
I'll do that when MS stop using my dataStop pirating software.
Someone here once used a similar activation script and it turned out to be ransomware.
Open the script in Notepad, then copy-pasta the code into Co-Pilot and ask it what the script does.