LMT AntiMalware
- Thread starter LeMinhThanh
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Currenly it only monitor and control file I/O and processesHow many hooks(system wide) this does?
-sepik
Hi!
LMT Anti Logger 4.9.5 released
Changelog:
LMT Anti Logger 4.9.5 released
Changelog:
- Now LMT Anti Logger supports boot into Safe Mode to handle files that the software cannot handle in the normal environment.
- Improved Anti Exploit for Browsers.
- Fixes some minor bugs and contains small improvements.
Hi, LeMinhThanh
I have read an interesting article about detecting user-mode keyloggers. What do you think about this method?
(PDF) A Novel Approach of Unprivileged Keylogger Detection (researchgate.net)
Can your software protect against Mouse Underlaying technique?
Mouse Underlaying: Global Key and Mouse Listener Based on an Almost Invisible Window with Local Listeners and Sophisticated Focus (eudl.eu)
Are the other techniques included (from the above article)?
gpumemscan2013eurosec.pdf (forth.gr)
I have read an interesting article about detecting user-mode keyloggers. What do you think about this method?
(PDF) A Novel Approach of Unprivileged Keylogger Detection (researchgate.net)
Can your software protect against Mouse Underlaying technique?
Mouse Underlaying: Global Key and Mouse Listener Based on an Almost Invisible Window with Local Listeners and Sophisticated Focus (eudl.eu)
Are the other techniques included (from the above article)?
- Kernel-based Keyboard Filter Driver
- Windows Keyboard Hook Method
- Keyboard State Table Method
gpumemscan2013eurosec.pdf (forth.gr)
Last edited:
I installed the application and saw information about the anti-hook methods: GetKeyState, GetAsyncKeyState, GetKeyboardState, DirectX, SetWindowsHookEx, GetRawInputData.
I f I correctly understand this short info, then LMT Anti Logger can monitor the Windows Keyboard Hook Method but not Kernel-based Keyboard Filter Driver Method or Keyboard State Table Method (they do not apply an API for hooking keystrokes).
Of course, the known keyloggers (and many known keylogging methods) can be prevented by AI, YARA rules, Virus Total, etc.
Edit1.
I am really impressed how one person could make an application (in a short time) with so many features that require wide knowledge about Windows and coding.

Edit2
I wonder how many well-known (old) techniques are seen in the wild nowadays?

I f I correctly understand this short info, then LMT Anti Logger can monitor the Windows Keyboard Hook Method but not Kernel-based Keyboard Filter Driver Method or Keyboard State Table Method (they do not apply an API for hooking keystrokes).
Of course, the known keyloggers (and many known keylogging methods) can be prevented by AI, YARA rules, Virus Total, etc.
Edit1.
I am really impressed how one person could make an application (in a short time) with so many features that require wide knowledge about Windows and coding.
Edit2
I wonder how many well-known (old) techniques are seen in the wild nowadays?
Last edited:
Hi @Andy Ful, thanks for the interesting articles, I will read them when I have time, I am currently on Tet holidays in Vietnam
And yes, I think my app cannot prevent advanced keyloggers from stealing keyboard data, so I added Realtime Protection, hope it can block keyloggers and malwares.
If I remember correctly, I have tested with
Refog keylogger free, Best-free keylogger, IwantSoft keylogger, Actual
keylogger, Revealer Keylogger and my app can prevent them from reading keyboard data, look like they all are using keyboard hooking
And yes, I think my app cannot prevent advanced keyloggers from stealing keyboard data, so I added Realtime Protection, hope it can block keyloggers and malwares.
If I remember correctly, I have tested with
Refog keylogger free, Best-free keylogger, IwantSoft keylogger, Actual
keylogger, Revealer Keylogger and my app can prevent them from reading keyboard data, look like they all are using keyboard hooking
Hi!
LMT Anti Logger 5.0 released
Changelog:
LMT Anti Logger 5.0 released
Changelog:
- Port from .NET Framework to .NET 5 to use the the latest benefits from .NET 5. New features will be added in the next versions.
- Improved logging.
- Fixes some minor bugs.
@LeMinhThanh
What are you going to give back to the VT-community? Dan from Voodooshield only used the VT-results and was cut off last year. Lucky for Dan was that he developed a cloud whitelist to compensate for this missing executable evaluation. I can remember in 2019 one of the new AI based antivirus solutions was also cut off from VT-results.
Regards L
What are you going to give back to the VT-community? Dan from Voodooshield only used the VT-results and was cut off last year. Lucky for Dan was that he developed a cloud whitelist to compensate for this missing executable evaluation. I can remember in 2019 one of the new AI based antivirus solutions was also cut off from VT-results.
Regards L
Sorry but I don't really understand what you mean@LeMinhThanh
What are you going to give back to the VT-community? Dan from Voodooshield only used the VT-results and was cut off last year. Lucky for Dan was that he developed a cloud whitelist to compensate for this missing executable evaluation. I can remember in 2019 one of the new AI based antivirus solutions was also cut off from VT-results.
Regards L
Virus Total changed their policy in 2016 (link), so anti-malware programs could not use the results of VT (and benefit of the hard work of all the AV-companies on VT). In the past VT-blocked AI based AV-products to use their VT-scanner. In 2020 VoodooShield also was not allowed to use their API any more. As soon as your program gets some audience reach and you would launch a commercial version, you are probably no longer allowed to use VT.
took the liberty of changing a few words in CS explanation to make it friendlier to read for you
cruelsister said:In short, a company must have a native (their own) scanner that has been approved by the AMTSO BEFORE they can leech VT data to add to their scanners
I'm not a big fan of any AV, but it always seemed outrageous to me that any person could set up a Cloud with a VT API hook and create your own Malware-B-Gone product without any actual research department, whereas those AV-companies spend millions on new detections
took the liberty of changing a few words in CS explanation to make it friendlier to read for you
Last edited:
Wow, thanks for your infomation!Virus Total changed their policy in 2016 (link), so anti-malware programs could not use the results of VT (and benefit of the hard work of all the AV-companies on VT). In the past VT-blocked AI based AV-products to use their VT-scanner. In 2020 VoodooShield also was not allowed to use their API any more. As soon as your program gets some audience reach and you would launch a commercial version, you are probably no longer allowed to use VT.
took the liberty of changing a few words in CS explanation to make it friendlier to read for you
Hi!
LMT Anti Logger 5.1 released, please uninstall version 5.0, then install ver 5.1
Changelog:
Link filtering is done on your computer, the database from Urlhaus. I am also building a api to use for filtering url on my server, it will be added in the next version.
Video:
You can add your custom rules like this:
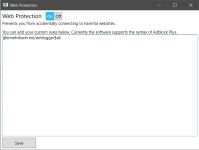
LMT Anti Logger 5.1 released, please uninstall version 5.0, then install ver 5.1
Changelog:
- Added Web Protection, block your connection to malicious websites. Currently only supports Chrome, MS Edge, Firefox and Opera. Best compatible with Firefox.
- Port from .NET 5 to .NET Framework to make sure the Web Protection feature is working properly
 )
) - Fixes some minor bugs.
Link filtering is done on your computer, the database from Urlhaus. I am also building a api to use for filtering url on my server, it will be added in the next version.
Video:
You can add your custom rules like this:

Last edited:
Just installed Kaspersky after 5 years using only Windows Defender, luckily it works well and doesn't block my software  )
)
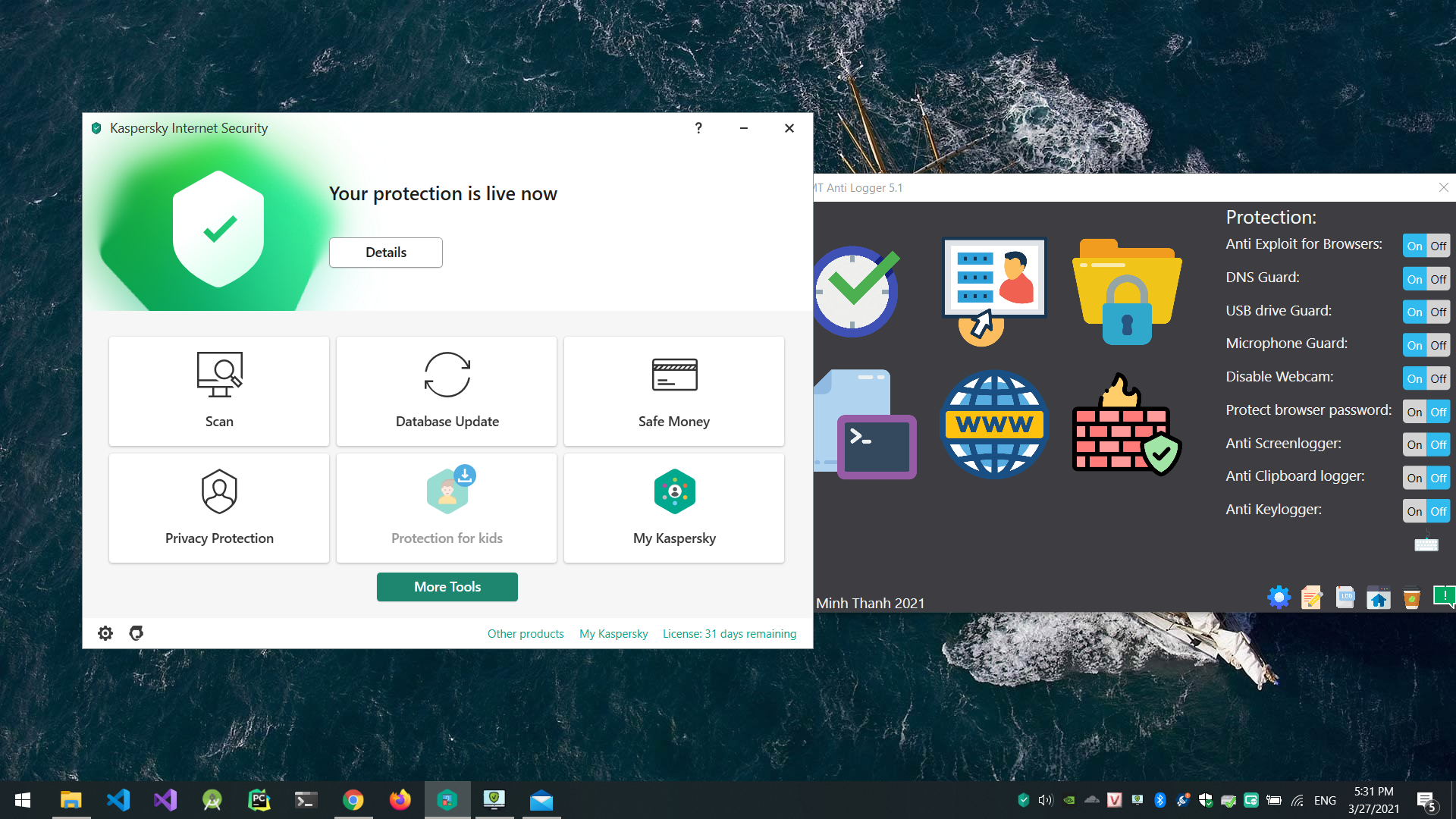
Updated: My Web Protection works ok with Kaspersky's Web Anti-Virus.
Updated: My Web Protection works ok with Kaspersky's Web Anti-Virus.
Last edited:
Hi!
LMT Anti Logger 5.1.1 released
Changelog:
LMT Anti Logger 5.1.1 released
Changelog:
- Web Protection feature will automatically filter the internet connection of all browsers on your computer. You can add the browser you want to exclude to Whitelist.
- Fixed a bug that could not return the line when adding custom rules on Web Protection.
Hi!
LMT Anti Logger 5.1.2 released
Changelog:
---------------------
When installing LMT Anti Logger, but meet this error, please turn off LMT Anti Logger's Self-defense, then restart the computer and install LMT Anti Logger again.
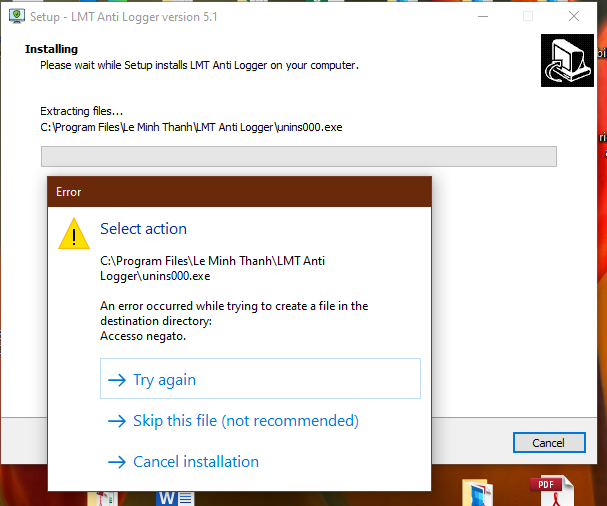
When installing LMT Anti Logger and meet this error, please click Skip:
LMT Anti Logger 5.1.2 released
Changelog:
- Create a online database for Web Protection feature, base on URLhaus, PhishTank, OpenPhish and ChongLuaDao.vn. Link filtering is done on your computer.
---------------------
When installing LMT Anti Logger, but meet this error, please turn off LMT Anti Logger's Self-defense, then restart the computer and install LMT Anti Logger again.
When installing LMT Anti Logger and meet this error, please click Skip:
Last edited:
Hi,
It seems that the network driver (WinDivert.sys) that I use in my software is reported to be malicious. WinDivert is safe.
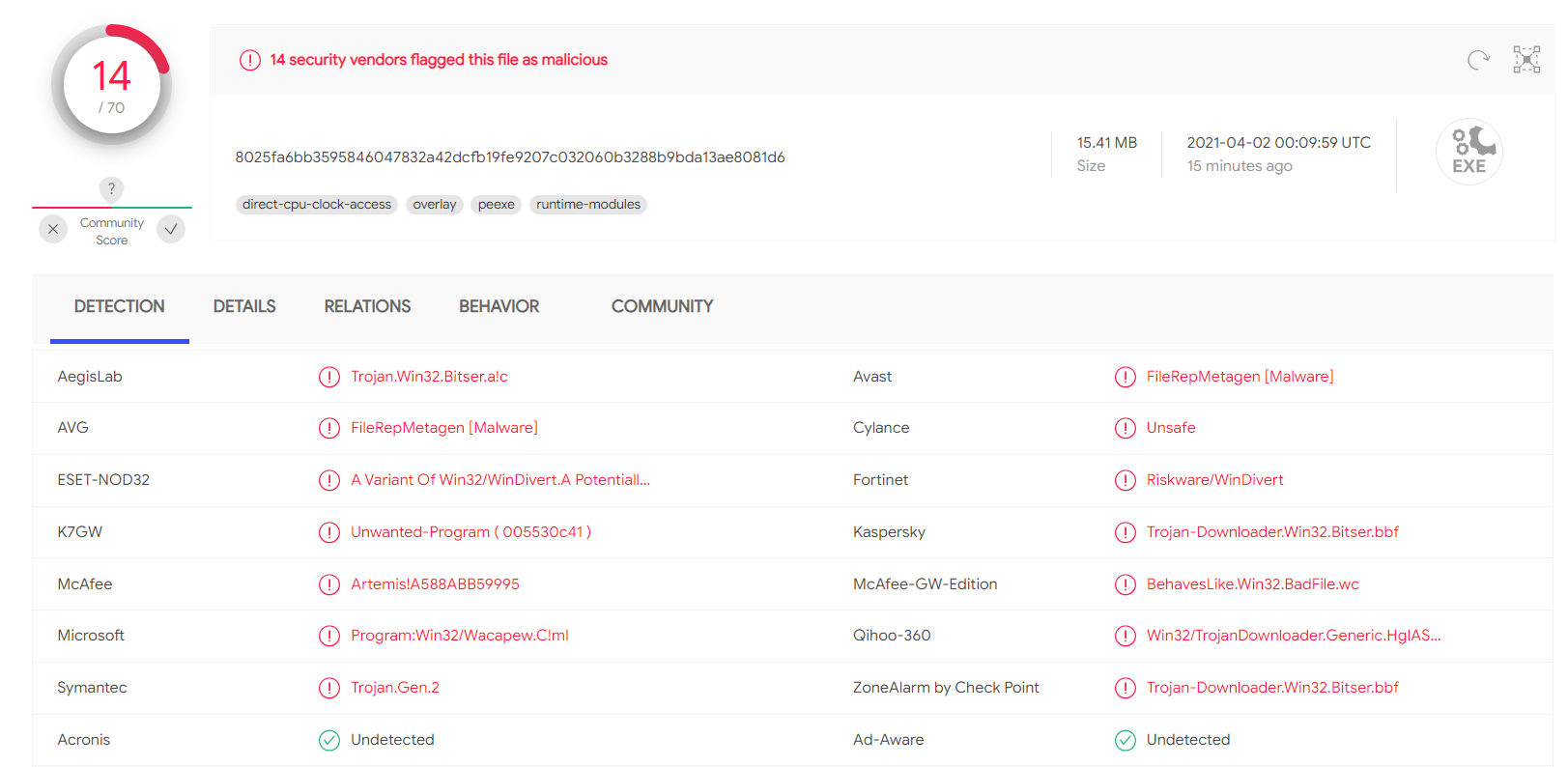
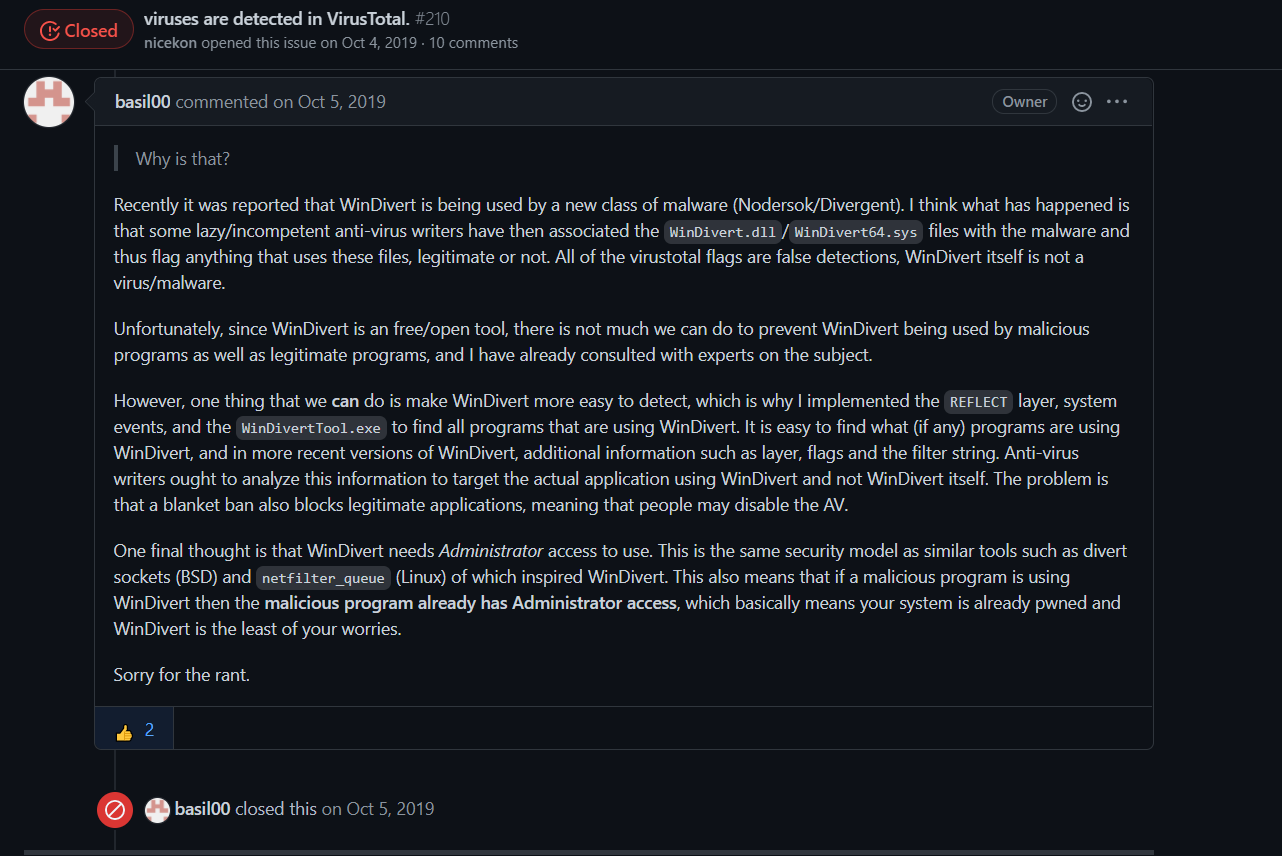
I will submit false positive to those antivirus software. If you still want to use my software please add it to your Antivirus software exclusions until the problem is resolved.
Regards,
Thanh
---------------------------
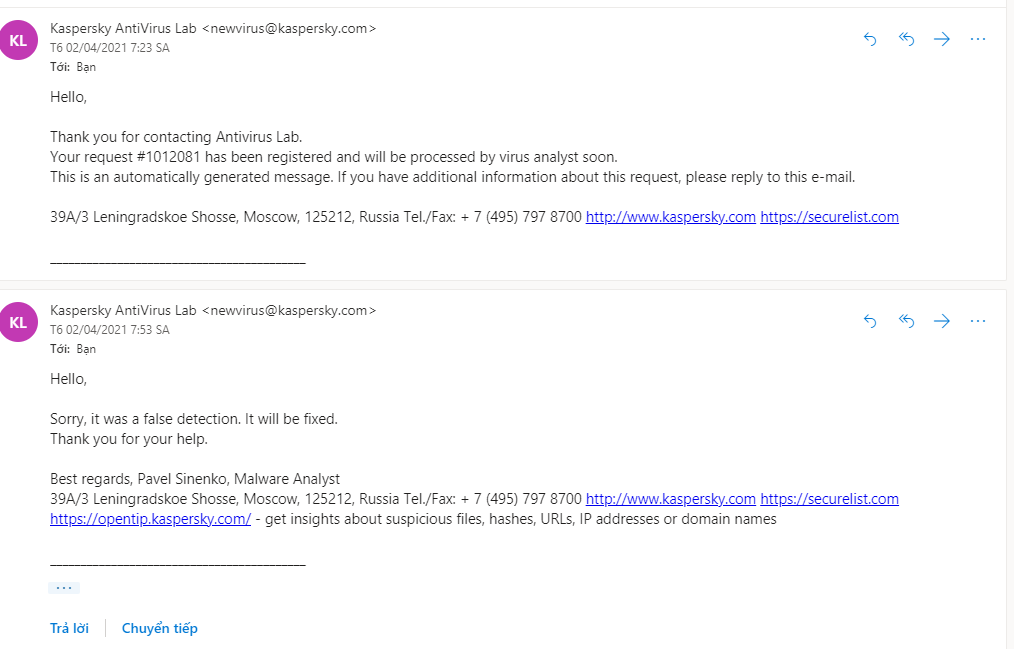
Updated: It will be fixed soon
It seems that the network driver (WinDivert.sys) that I use in my software is reported to be malicious. WinDivert is safe.
I will submit false positive to those antivirus software. If you still want to use my software please add it to your Antivirus software exclusions until the problem is resolved.
Regards,
Thanh
---------------------------
Updated: It will be fixed soon
Hi!
LMT Anti Logger 5.1.3 released
Changelog:
Web Protection will scan HTTP/HTTPS so it may affect your web-surfing experience, if you have any problems with Web Protection please email me!
LMT Anti Logger 5.1.3 released
Changelog:
- Fixed a bug prevent Chromium browsers unable to display media content when Web Protection is enabled.
Web Protection will scan HTTP/HTTPS so it may affect your web-surfing experience, if you have any problems with Web Protection please email me!
- Oct 25, 2014
- 2,636
- 7,291
- 3,588
- 40
Hi @LeMinhThanh
Can you report that Files to the detected vendors please
LMTAntiLoggerSetup5.1.1.exe
LMTAntiLogger 5.1.2.0.exe
LMTAntiLogger 5.1.3.0.exe
With best Regards
Mops21
Can you report that Files to the detected vendors please
LMTAntiLoggerSetup5.1.1.exe
LMTAntiLogger 5.1.2.0.exe
LMTAntiLogger 5.1.3.0.exe
With best Regards
Mops21
Hi @Mops21,
I have reported false positives of version 5.1.3 to Cylance, K7AntiVirus, Microsoft and Eset.
I have reported false positives of version 5.1.3 to Cylance, K7AntiVirus, Microsoft and Eset.
You may also like...
-
On Sale! Avast Premium Security 1 Device 1 Year 9.99€
- Started by Brownie2019
- Replies: 0
-
Serious Discussion A Habit-Based Guide to Internet Security
- Started by Divergent
- Replies: 2
-
-
Malware News Emojis in PureRAT’s Code Point to AI-Generated Malware Campaign
- Started by Brownie2019
- Replies: 11
-
Serious Discussion Simple Steps to Secure Your Windows 11 PC
- Started by Divergent
- Replies: 0