Gandalf_The_Grey
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
A threat actor associated with the LockBit 3.0 ransomware operation is abusing the Windows Defender command line tool to load Cobalt Strike beacons on compromised systems and evade detection by security software.
Cobalt Strike is a legitimate penetration testing suite with extensive features popular among threat actors to perform stealthy network reconnaissance and lateral movement before stealing data and encrypting it.
However, security solutions have become better at detecting Cobalt Strike beacons, causing threat actors to look for innovative ways to deploy the toolkit.
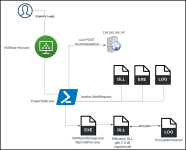
In a recent incident response case for a LockBit ransomware attack, researchers at Sentinel Labs noticed the abuse of Microsoft Defender’s command line tool “MpCmdRun.exe” to side-load malicious DLLs that decrypt and install Cobalt Strike beacons.
The initial network compromise in both cases was conducted by exploiting a Log4j flaw on vulnerable VMWare Horizon Servers to run PowerShell code.
Side-loading Cobalt Strike beacons on compromised systems isn’t new for LockBit, as there are reports about similar infection chains relying on the abuse of VMware command line utilities.

LockBit operator abuses Windows Defender to load Cobalt Strike
Security analysts have observed an affiliate of the LockBit 3.0 ransomware operation abusing a Windows Defender command line tool to decrypt and load Cobalt Strike beacons on the target systems.