For more than four weeks, the only source of Locky ransomware infections has been through spam campaigns that distributed the Kovter click-fraud malware, as the primary source of Locky infections, the Necurs botnet, has been offline for the Christmas and New Year holidays.
This Locky spam dip has been seen by multiple observers, such as security firms Avast and Check Point, and security researchers Kevin Beaumont, MalwareTech, MalwareHunterTeam, and others.
According to Check Point, who recently released a report on December's most active malware families, Locky spam numbers have gone down 81%. Previously, in October, Locky had been ranked as the top malware threat in the world, while now, in December, Locky is not even in the top 10 anymore.
The same thing can also be seen in a chart released by Avast. Even if the chart doesn't cover the last ten days, Locky spam numbers have remained at the same low levels as during the holidays.
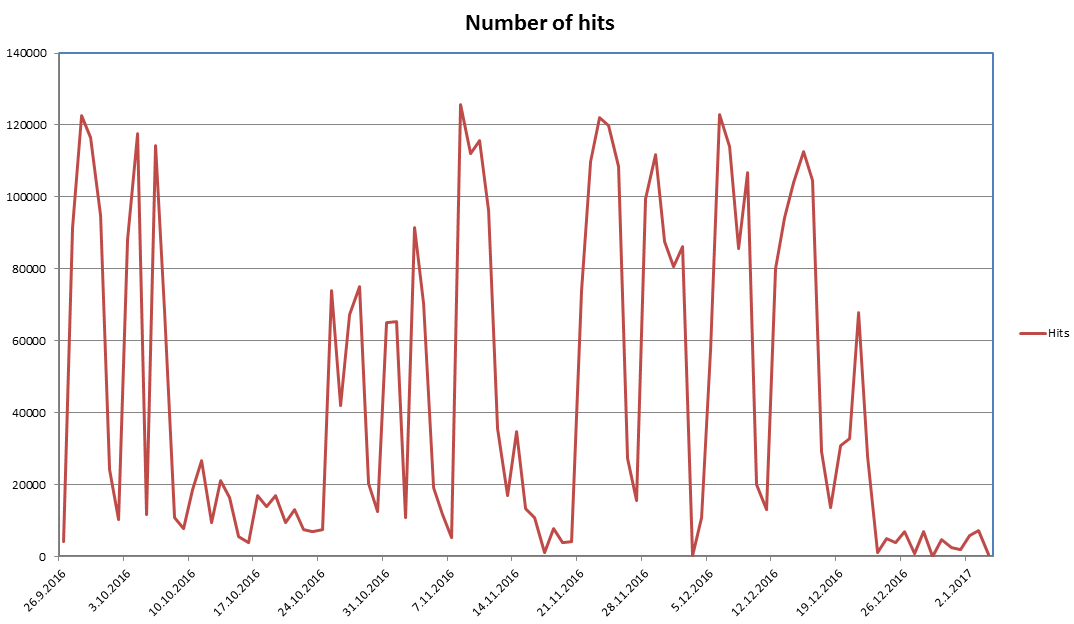
The only tiny trail of activity in the chart above is the Locky ransomware delivered as a second-stage download for Kovter campaigns.
Locky finds a home with Kovter
Kovter is a click-fraud malware that infects computers and clicks on invisible ads on the user's behalf. This malware has been around for years, and recently, it started distributing a wide range of secondary payloads.
In January 2016, Kovter downloaded and installed a proxy client on infected PCs, transforming infected hosts into proxy servers for the ProxyGate web proxy service. This allowed the Kovter gang to make a side profit by routing web traffic through infected PCs, while also earning money from its main activity: click-fraud.
In the same month, Kovter also started distributing a version of the Nemucod ransomware, for which Fabian Wosar of Emsisoft had successfully created a decrypter.
Read more: Locky Ransomware Activity Goes Down by 81%
This Locky spam dip has been seen by multiple observers, such as security firms Avast and Check Point, and security researchers Kevin Beaumont, MalwareTech, MalwareHunterTeam, and others.
According to Check Point, who recently released a report on December's most active malware families, Locky spam numbers have gone down 81%. Previously, in October, Locky had been ranked as the top malware threat in the world, while now, in December, Locky is not even in the top 10 anymore.
The same thing can also be seen in a chart released by Avast. Even if the chart doesn't cover the last ten days, Locky spam numbers have remained at the same low levels as during the holidays.

The only tiny trail of activity in the chart above is the Locky ransomware delivered as a second-stage download for Kovter campaigns.
Locky finds a home with Kovter
Kovter is a click-fraud malware that infects computers and clicks on invisible ads on the user's behalf. This malware has been around for years, and recently, it started distributing a wide range of secondary payloads.
In January 2016, Kovter downloaded and installed a proxy client on infected PCs, transforming infected hosts into proxy servers for the ProxyGate web proxy service. This allowed the Kovter gang to make a side profit by routing web traffic through infected PCs, while also earning money from its main activity: click-fraud.
In the same month, Kovter also started distributing a version of the Nemucod ransomware, for which Fabian Wosar of Emsisoft had successfully created a decrypter.
Read more: Locky Ransomware Activity Goes Down by 81%