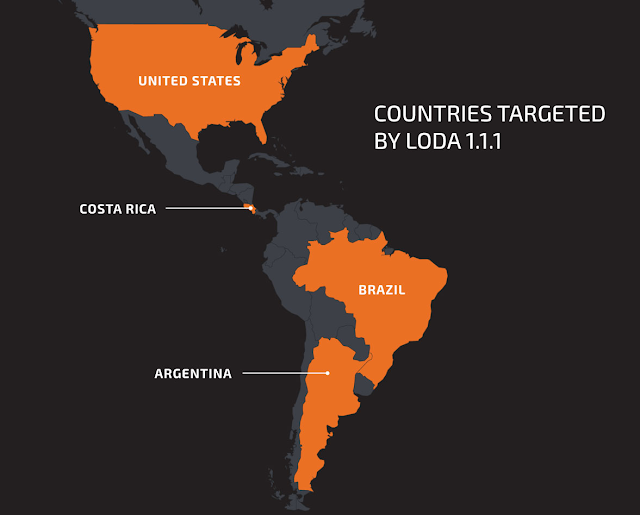
Loda is a simple, yet effective, RAT that has matured over time. This RAT is a good example of how effective relatively simple techniques combined with basic obfuscation can be. The techniques this malware employs are of fairly low complexity and show that slight changes in implementation can significantly reduce detection rates. Telemetry from Cisco Umbrella shows that this campaign is quite active and seems to be targeting countries in South America, Central America and the U.S. The majority of the queries to the C2 domain "4success[.]zapto[.]org" originate from Brazil, Costa Rica and the United States. Similarly, the queries to "success20[.]hopto[.]org" originate from Argentina, Brazil and the United States. Our telemetry also shows that C2 communications go as far back as the last quarter of 2019.