- Mar 17, 2023
- 503
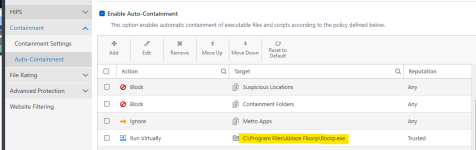
I used sandboxie and never used comodo. I quit sandboxie when it was abandoned by Sophos. I just recently saw the private open revitalization of the sandboxie project and am thinking of installing it and having it protect my chrome. But honestly I don't know if sandboxing chrome would defeat the chrome sandbox and make more vulnerable. does Comodo the sandbox differently from sandboxie? Can one sandbox chrome without compromising the chrome inherent sandbox?
Basically a breakdown of similarities and differences between comodo sandox and sandboxie or vail?
Basically a breakdown of similarities and differences between comodo sandox and sandboxie or vail?
Last edited: