Gandalf_The_Grey
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Introduction
It is an often-heard view that macOS computers don’t need antivirus protection. Whilst it is certainly true that the population of macOS malware is very tiny compared to that for Windows and Android, there have still been many instances of macOS malware getting into the wild. Moreover, Apple Mac security needs to be considered in the wider context of other types of attacks.
In addition, it should be noted that Apple themselves ship some anti-malware capabilities within macOS. Firstly, there is “Gatekeeper”, which warns when apps without a digital signature are run. Then there is “XProtect”, which checks files against known-malware signatures. Finally, Apple provide the MRT (Malware Removal Tool). Gatekeeper and MRT are essentially invisible to users and have no direct user interface for the user. System updates are installed automatically using the update process. The effectiveness of Apple’s built-in anti-malware features have been questioned, however, and some security experts recommend strengthening the defences by adding in a third-party antivirus package. There are many good reasons for this. Firstly, the approach taken by Apple might be adequate for well-established malware, but might not respond quickly enough to emerging threats. Secondly, you might want a broader base of malware evaluation. Thirdly, macOS is not immune to bugs.
Some vendors’ macOS security products can detect malware aimed at other operating systems too. Hence an AV program on your macOS computer could effectively handle Windows and Android malware as well. There are scenarios where you might well benefit from scanning for such threats. For example, if you are given a USB stick of photos by one friend, who asks you to make a copy for a second friend. They both use Windows, but you are using a macOS computer. There is Windows malware on the USB stick, and you make a copy of all the files. In this scenario, it is useful to be able to ensure that malware is not inadvertently passed on from one friend to another, even if your own machine is not at risk.
Mac security programs can offer other capabilities too. For example, browser extensions can identify web sites which are potentially phishing locations. Readers should note that Mac users are just as vulnerable to phishing attacks as users of e.g. Windows, as phishing sites function by deceiving the user rather than by altering the operating system or browser.
Other packages might offer VPN (virtual private network) capabilities which can be useful when you need to operate your computer in an untrusted environment, or a public location such as an Internet café, where you are not sure of the integrity of the connection. You might also want to replace macOS’ built-in parental control capabilities with third party tools, if you believe this is more appropriate to your family needs.
Before purchasing a Mac security solution, you also need to decide on the size and scope of the protection you wish to deploy. It might be for a single computer, or for a laptop and desktop. Or you might have a family environment. There might be a mixture of macOS laptops and desktops, but also other devices too like Windows desktops and laptops, along with iOS and Android phones and tablets. For this environment, a broader and more flexible licensing package might well be appropriate.
This could allow you to purchase e.g. 5 licenses and then distribute them amongst your collection of devices. It could also give you the flexibility to transfer licensing from one device to a new item, e.g. if you need to replace an aging Windows laptop with a new MacBook. Some packages offer cloud-based management interfaces. Usually this is to cover the licensing of the packages, but some can also be used to initiate malware scans and device updates and manage parental control capabilities.
Then there are packages which are really aimed at the business and corporate space. Here the macOS support is but one component of a much larger deployment and management infrastructure. This will cover all devices and operating systems, often running thousands of managed devices. Although it might be tempting to go for a larger and stronger solution than is appropriate for your organizational size, be aware that the larger platforms have significant up-front design, management and deployment overheads. This is required to allow these tools to scale to the sizes that they can support, and they usually bring in a level of day-to-day commitment which, although entirely proper and required in a larger enterprise, is simply beyond the capabilities and resourcing of a small company.
Experienced and responsible Mac users who are careful about which programs they install, and which sources they obtain them from, may well argue – very reasonably – that they are not at risk from Mac malware. However, we feel that non-expert users, children, and users who frequently like to experiment with new software, could definitely benefit from having security software on their Mac systems, in addition to the security features provided by the macOS itself.
Readers who are concerned that third-party security software will slow their Mac down can be reassured that we considered this in our test; we did not observe any major performance reduction during the course of the test with any of the programs reviewed.
As with Windows computers, Macs can be made safer by employing good security practices. We recommend the following:
- Do not use an administrator account for day-to-day computing
- Keep your Mac operating system and third-party software up-to-date with the latest patches
- Use secure passwords (the Mac includes the KeyChain password manager)
- Deactivate any services such as Airport, Bluetooth or IPv6 that you don’t use
- Be careful about which programs you install and where you download them from
Results
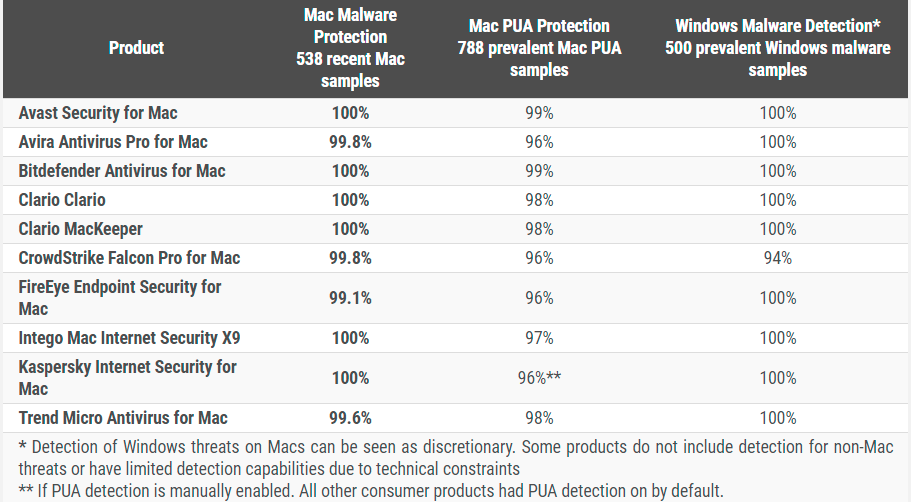

Mac Security Test & Review 2021
Read the Mac Security Test & Review 2021 to learn how well Mac security software products can protect against Malware
 www.av-comparatives.org
www.av-comparatives.org
