A fake 7-Zip website is distributing a trojanized installer of the popular archiving tool that turns the user’s computer into a residential proxy node.
Residential proxy networks use home user devices to route traffic with the goal of evading blocks and performing various malicious activities such as credential stuffing, phishing, and malware distribution.
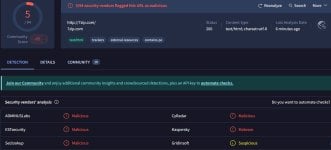
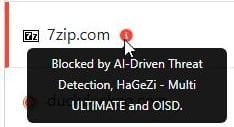
The new campaign became better known after a user reported that they downloaded a malicious installer from a website impersonating the 7-Zip project while following instructions in a YouTube tutorial on building a PC system. BleepingComputer can confirm that the malicious website, 7zip[.]com, is still live.
The website is blocked by uBOL and ControlD DNS (hagezi tif); it's detected on VT by only two vendors.
The attacker copied the text and mimicked the structure of the original 7-Zip website located at 7-zip.org.
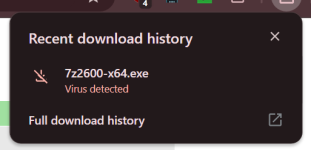
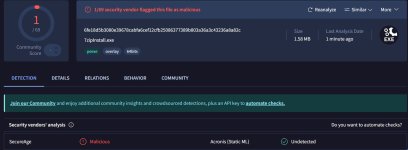
The installer file was analyzed by researchers at cybersecurity company Malwarebytes, who found that it is digitally signed with a now-revoked certificate originally issued to Jozeal Network Technology Co., Limited.
The malicious copy also contains the 7-Zip program, thus providing the regular functions of the tool. However, the installer drops three malicious files:
- Uphero.exe – service manager and update loader
- hero.exe – main proxy payload
- hero.dll – support library

Malicious 7-Zip site distributes installer laced with proxy tool
A fake 7-Zip website is distributing a trojanized installer of the popular archiving tool that turns the user's computer into a residential proxy node.www.bleepingcomputer.com