
More than two dozen malicious Android applications with over 2.1 million installs in total were observed by security researchers while displaying aggressive full-screen ads after downloading configuration files.
The 25 apps were found in the Play Store during late-August and, while immediately after being installed they did not exhibit any malicious behavior, the apps will subsequently download malware configuration files that would switch on their 'evil' mode.
These will tell the bundled malware components to enable modules designed to hide the apps' icons and to start displaying ads that will allow the malware developers to earn money using the infected Android devices.
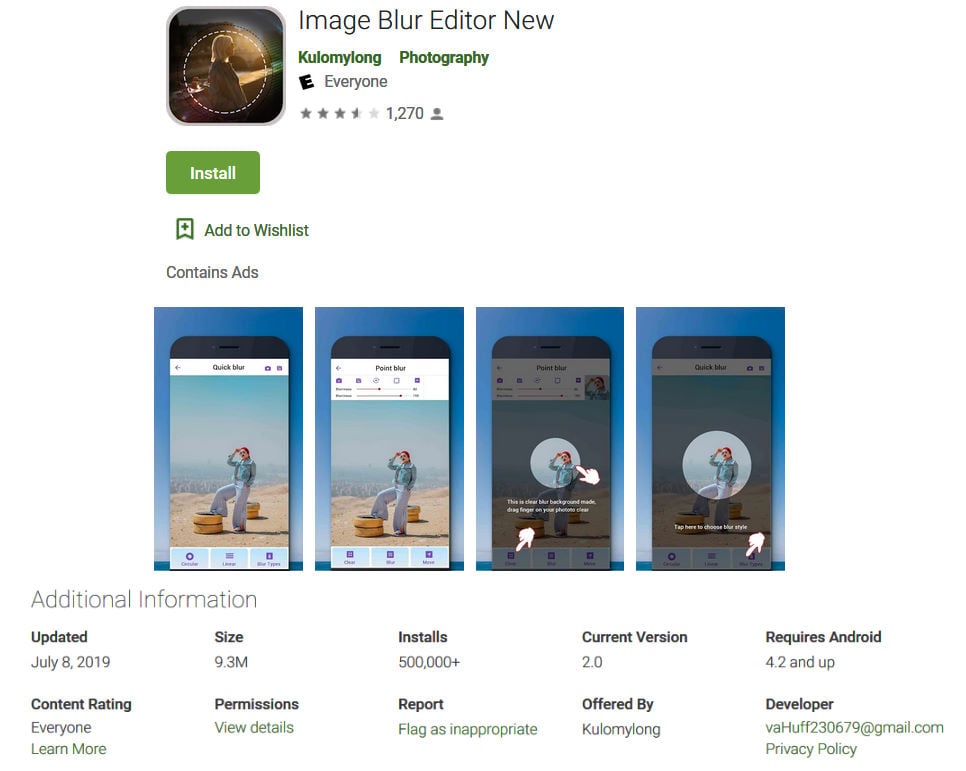
Google Play Protect bypassed
All the 25 apps—camouflaged as fashion and photo utilities—were removed after being reported to Google on September 2, after successfully landing on the Play Store by making sure that the malicious functions were not hardcoded in the APKs (Android Package Kits) submitted for review.
"Instead, the switch is controlled remotely via the downloaded configuration file, allowing the malware developer to evade Google Play’s rigorous security testing," says Symantec's Threat Intelligence team who discovered the apps.
"These 25 malicious hidden apps share a similar code structure and app content, leading us to believe that the developers may be part of the same organizational group or, at the very least, are using the same source code base."
To avoid having their apps being identified as malicious, the threat actors used initialization vectors and encryption keys to encode and encrypt some keywords in the malware's source code to be able to bypass the rule-based detection engines of potential anti-malware solutions installed on the devices.

Randomly displayed ads, abused top charts
The apps are designed to first hide from sight by removing their icons and then to start displaying ads on the compromised devices, even if the apps are closed.
"Full-screen advertisements are displayed at random intervals with no app title registered in the advertisement window, so users have no way of knowing which app is responsible for the behavior," says Symantec's report.
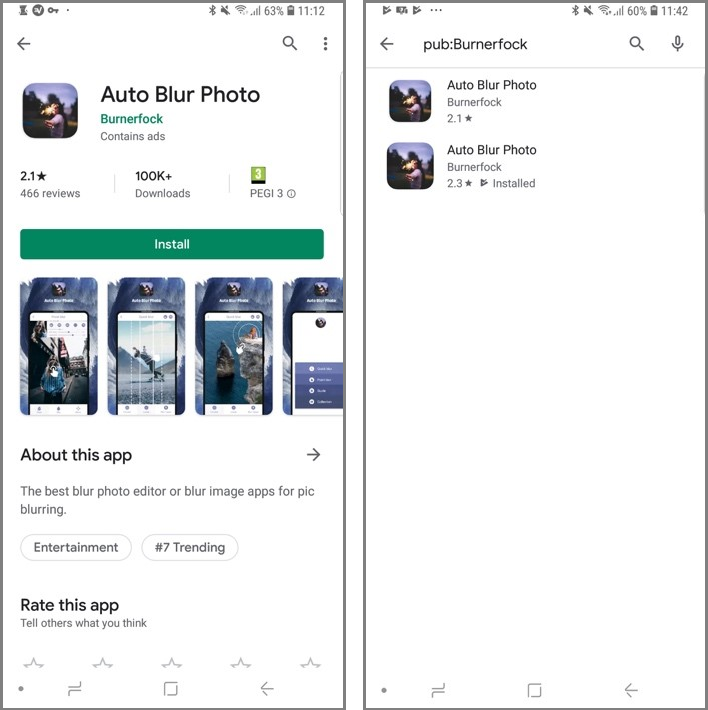
As a side note, one of the developers behind the apps used an innovative way to get a malicious app onto its targets' devices: he published two identical apps to the store, one clean and one with bundled malicious code.
The clean one was boosted to get into the Play Store's Top Trending Apps category, with the hope that the malicious copy would also be installed by accident and infect users with the aggressive ad-pushing malware.
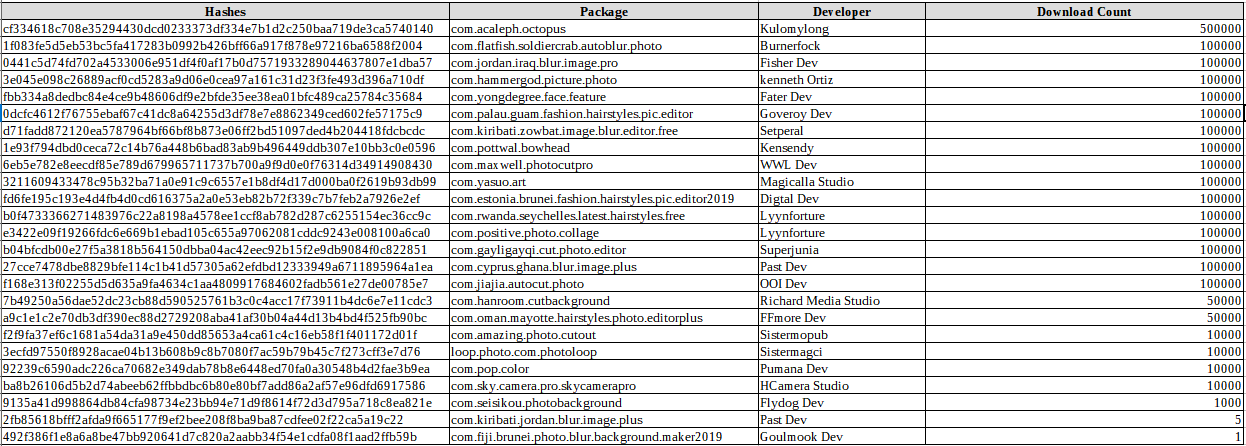
A full list of indicators of compromise (IOCs) including Application IDs (package names), hashes, developer names, and download counts for each of the 25 malicious apps are available at the end of Symantec Threat Intelligence team's analysis.
