- Mar 2, 2023
- 1,398
This is the part that caught my eye.
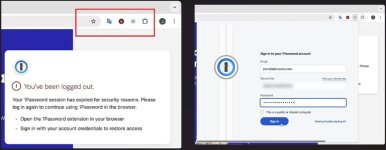
In SquareX's demonstration, the attackers impersonate the 1Password password manager extension by first disabling the legitimate one using the 'chrome.management' API, or if the permissions aren't available, user interface manipulation tactics to hide it from the user.
Simultaneously, the malicious extension switches its icon to mimic that of 1Password, changes its name accordingly, and displays a fake login popup that matches the appearance of the real one.
To force the user into entering their credentials, when attempting to log in to a site, a fake "Session Expired" prompt is served, making the victim think they were logged out.
This will prompt the user to log back into 1Password through a phishing form that sends inputted credentials back to the attackers.




