A modular malware with worm capabilities exploits known vulnerabilities in servers running ElasticSearch, Hadoop, Redis, Spring, Weblogic, ThinkPHP, and SqlServer to spread from one server to another and mine for Monero cryptocurrency.
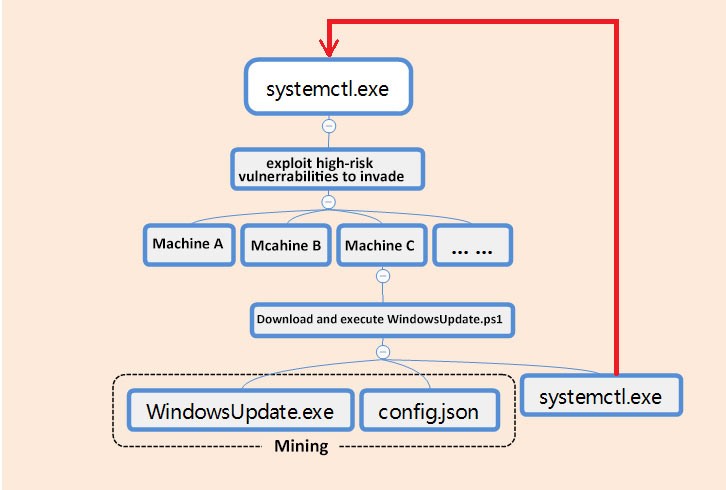
Systemctl.exe, the worm module of the malware named PsMiner by the 360 Total Security
researchers, is a Windows binary written in the Go language which bundles all the exploit modules used to hack into vulnerable servers it can find on the Internet.
Besides the exploits, PsMiner's worm module also has the capability to brute force its way in, whenever it finds targets that uses weak or default credentials, as well as crack user credentials using an additional brute force password cracking component.
Once it manages to infiltrate a victim's computer, PsMiner will execute a PowerShell command which downloads a WindowsUpdate.ps1 malicious payload, the malware's master module designed to drop the Monero miner as part of the final infection stage.
The infection process