The first principle of Microsoft Security Division's best security practices has been the same for over 3 decades, and culminated in Windows 10 S (for consumers, education and enterprise) and Group Policy Object\AppLocker\Device Guard\Windows Defender Application Control templates (for education and enterprise). Microsoft's own Windows 10 S was developed with all of Microsoft's own research and experience protecting systems in many different environments going all the way back to the early 1990s. The foundation of all Microsoft security has always been attack surface reduction (ASR), which means disabling processes that are not needed in everyday baseline Windows environment.
Nowhere will anyone find Microsoft stating that "If it ships with Windows, then it should not be permanently disabled." That has never been Microsoft's official position. The exact opposite is true. Microsoft's position for the past 30 years has been "If you don't need it, then disable it permanently for your own good."
10 S is not a specialized version of Windows 10. It is marketed to education and enterprise and it is popular (just involved in a 17,500 endpoint deployment). For shrewd consumers, there is a method to activate 10 S mode. 10 S mode (no install of 3rd party programs) provides the best possible security per Microsoft's recommended best practices.
Microsoft has covered this numerous times across time in many different venues both online and in conferences - especially at its annual Microsoft Ignite galas. For the best security, Microsoft recommends disabling the following:
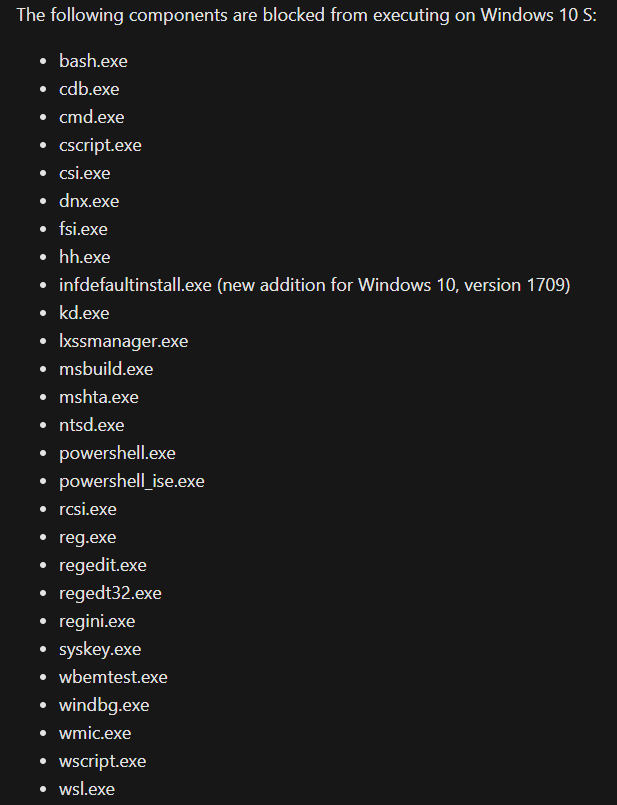
In addition to the above, Microsoft's Security Division recommends that the following be disabled if not needed:
Nowhere will anyone find Microsoft stating that "If it ships with Windows, then it should not be permanently disabled." That has never been Microsoft's official position. The exact opposite is true. Microsoft's position for the past 30 years has been "If you don't need it, then disable it permanently for your own good."
10 S is not a specialized version of Windows 10. It is marketed to education and enterprise and it is popular (just involved in a 17,500 endpoint deployment). For shrewd consumers, there is a method to activate 10 S mode. 10 S mode (no install of 3rd party programs) provides the best possible security per Microsoft's recommended best practices.
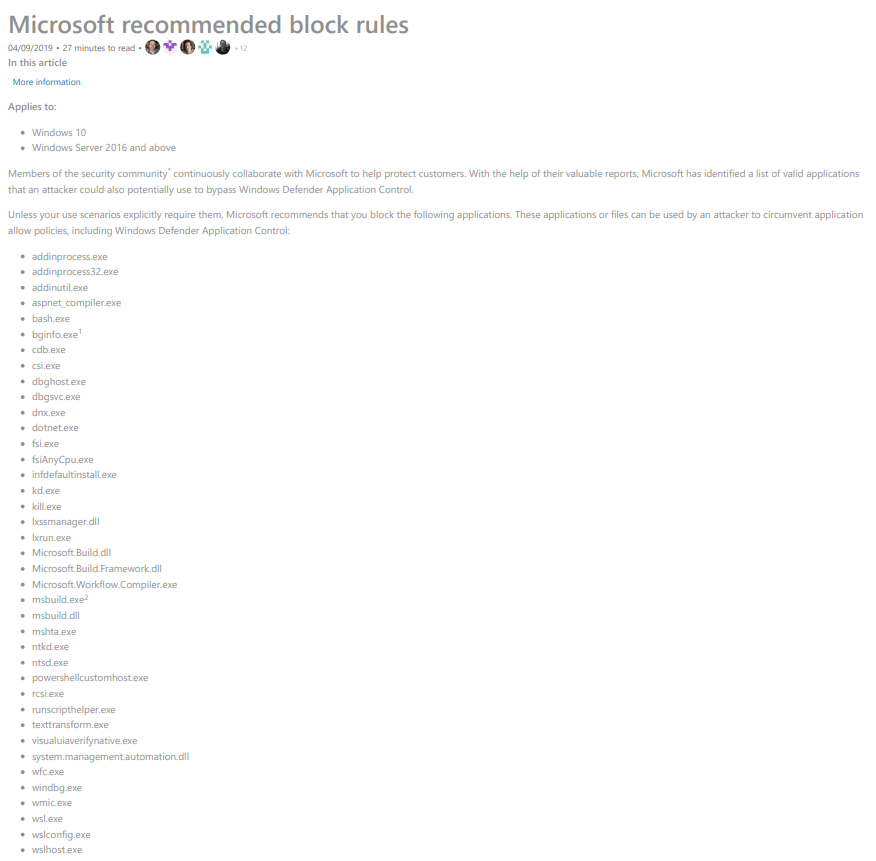
Microsoft has covered this numerous times across time in many different venues both online and in conferences - especially at its annual Microsoft Ignite galas. For the best security, Microsoft recommends disabling the following:
In addition to the above, Microsoft's Security Division recommends that the following be disabled if not needed:
Last edited:



