- Apr 28, 2015
- 9,397
- 1
- 84,815
- 8,389
The LOLBins used are trusted by KSN, so... unless You manually put previously those LOLBins in Untrusted group...
Yeah, assuming attacker doesn’t know what’s on the list this will suspend the attack. Otherwise, you will restrict few, they will use few others.The LOLBins used are trusted by KSN, so... unless You manually put previously those LOLBins in Untrusted group...
I tested KIS which is currently becoming an obsolete product, so I did not make a video - @harlan4096 helped me to contact the Kaspersky staff.Where is the test video? It's not there in the review segment.
There is nothing stupid about showing these folks the main underlying issue in security as it has always been when it comes to Windows and the swiss cheese of security holes it has always been. There is a reason constant updates and security patches are implemented into this operating system. If one were to consider how many times in the past, things have been embedded in legit programs bypassing security suites, they could quickly realize that a POC as such could be weaponized easily. Pointing out such flaws is helpful in every way as stated before. Although its up to security vendors and OS engineers to take these findings seriously before they do end up being exploited especially in a business environment.You are right. If this attack is treated as a full attack, it is kinda stupid.
The presented method is not a full attack, and it is not probable that it can affect home users. However, it can probably be used as a part of targeted attacks in businesses.
Interestingly, Tamper protection was bypassed in the video.
Andy, thank you for those disclaimers as to help the normal home user like myself, not go into panic mode. My takeaway from all of this, is to bump my UAC up to the next level.The best method to stop such attacks, is the prevention against UAC bypasses. One can use SUA which can probably stop almost all of them. Also, the UAC set to max setting can prevent most such attempts. Of course, one can use additional security layers that can restrict scripting, exploits, etc.
The problem still can be with lateral movement in Enterprises. (my Bold added)
Generally, there are more popular attack vectors, so the chances of being attacked in this way are rather small.
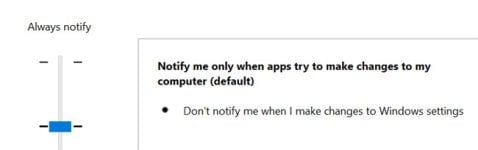
Yep, and now I know why, it definitely makes sense.ThanksWe always recommend in Security Configs forum section UAC SET TO ALWAYS NOTIFY...
This policy is included in the H_C (No Elevation on SUA). Is as Strong as SUA, but simply you will not see the UAC credential prompt. If something can bypass UAC on SUA, it can also bypass this policy.@Andy Ful or anyone else for that matter,
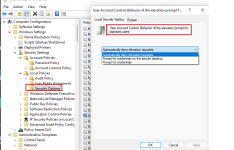
would setting the "User Account Control Behaviour of the elevation prompt for standard users" under Group Policy in Win 10/11 Pro to 'Automatically deny elevation requests" help to thwart this type of threat, or would a UAC bypass defeat it?
View attachment 282242
I suppose what I'm also trying to get at is it's my understanding anyways that the safest way to use a SUA is to run it only as sua and never elevate any task from it. Rather, all elevation tasks should be done from a separate Admin account.
Andy, thank you for those disclaimers as to help the normal home user like myself, not go into panic mode. My takeaway from all of this, is to bump my UAC up to the next level.
View attachment 282243
I’ve forgotten, on always notify, are admin rights inherited from the parent process?
The protected processes are User-mode AV services. Code Integrity protects them against thread injection and writing into their virtual memory.Thanks, although most home users have memory integrity enabled (is on by default, see link) also would protected processes prevent shutting doen the service?
BTW glad I am using your WHHL, WDAC-ISG uses higher integrity level than admin rights
(discussed on reddit)
At least in the case of this bypass demo, UAC seems kind of dumb to me.
I guess (sorry bear with me, I may way off on this) the kDefender file you launch elevated is a shortcut that runs a script via Windows Command Processor, which of course UAC correctly sees as a signed Microsoft publisher file as seen with the grey background UAC prompt, but why can it not recognize, for instance, the "I_am_nice_and_clean.dat" file and alert on it, or anything else that may be a part of the payload? Is it because it's a .dat file and not an executable?
If using a HIPS or similar program, could it not be possible and effective protection to alert on any child processes command prompt and other signed parent processes such as powershell attempt to launch?