Gandalf_The_Grey
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
- Apr 24, 2016
- 7,845
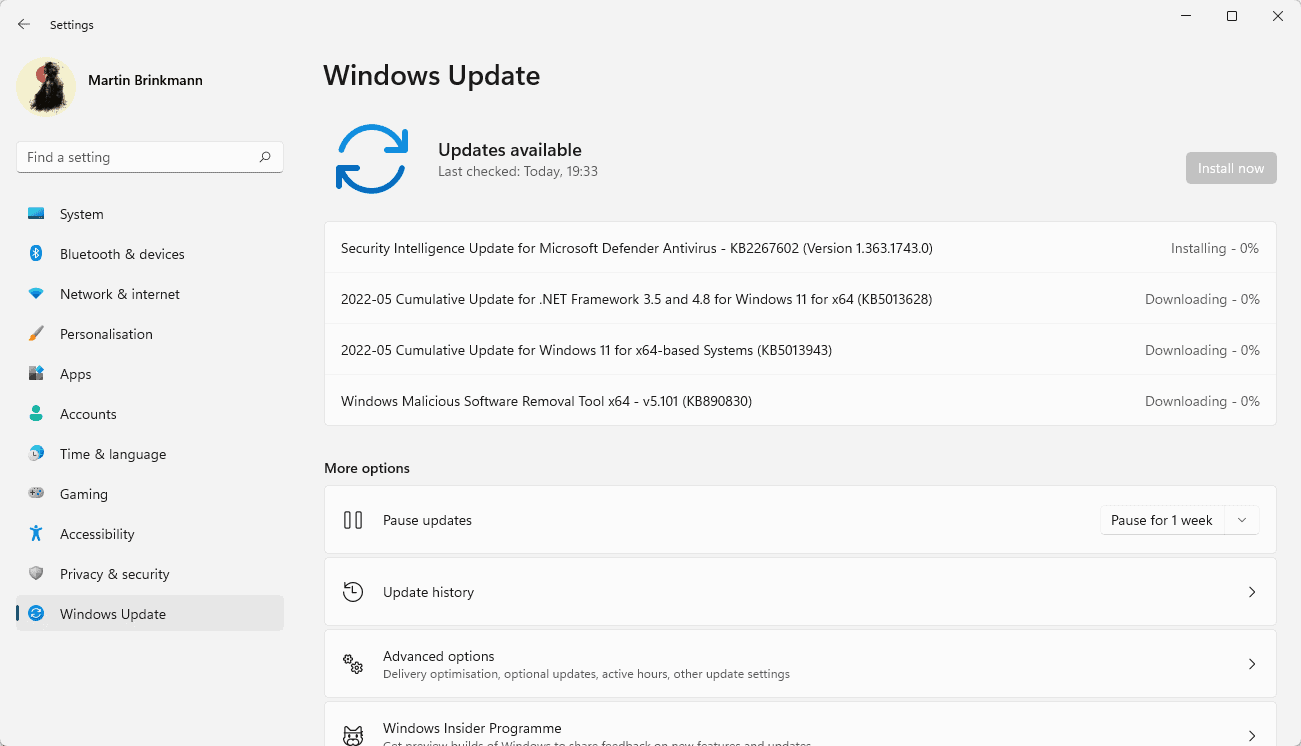
Today is Microsoft's May 2022 Patch Tuesday, and with it comes fixes for three zero-day vulnerabilities, with one actively exploited, and a total of 75 flaws.
Of the 75 vulnerabilities fixed in today's update, eight are classified as 'Critical' as they allow remote code execution or elevation of privileges.
The number of bugs in each vulnerability category is listed below:
For information about the non-security Windows updates, you can read about today's Windows 10 KB5013942 and KB5013945 updates.
- 21 Elevation of Privilege Vulnerabilities
- 4 Security Feature Bypass Vulnerabilities
- 26 Remote Code Execution Vulnerabilities
- 17 Information Disclosure Vulnerabilities
- 6 Denial of Service Vulnerabilities
- 1 Spoofing Vulnerability
- 0 Edge - Chromium Vulnerabilities
Three zero-days fixed, two actively exploited
This month's Patch Tuesday includes fixes for three zero-day vulnerabilities, with one actively exploited and the others publicly disclosed.
Microsoft classifies a vulnerability as a zero-day if it is publicly disclosed or actively exploited with no official fix available.
The actively exploited zero-day vulnerability fixed today is a new NTLM relay attack tracked as 'CVE-2022-26925 - Windows LSA Spoofing Vulnerability.'
"An unauthenticated attacker could call a method on the LSARPC interface and coerce the domain controller to authenticate to the attacker using NTLM. This security update detects anonymous connection attempts in LSARPC and disallows it," explains Microsoft in their advisory.
Using this attack, threat actors can intercept legitimate authentication requests and use them to gain elevated privileges, even as far as assuming the identity of a domain controller.
The two publicly exposed zero-days are a denial of service vulnerability in Hyper-V and a new remote code execution vulnerability in Azure Synapse and Azure Data Factory.
Now that Microsoft has issued patches for these vulnerabilities, admins should expect that threat actors will analyze the security updates to see what has changed. Then, using this information, they will create their own exploits to use in attacks
- CVE-2022-22713 - Windows Hyper-V Denial of Service Vulnerability
- CVE-2022-29972 - Insight Software: CVE-2022-29972 Magnitude Simba Amazon Redshift ODBC Driver
Therefore, it is strongly advised to install today's security updates as soon as possible.