silversurfer
Super Moderator
Thread author
Verified
Top Poster
Staff Member
Malware Hunter
Forum Veteran
- Aug 17, 2014
- 12,736
- 123,873
- 8,399
Microsoft August 2021 Patch Tuesday fixes 3 zero-days, 44 flaws
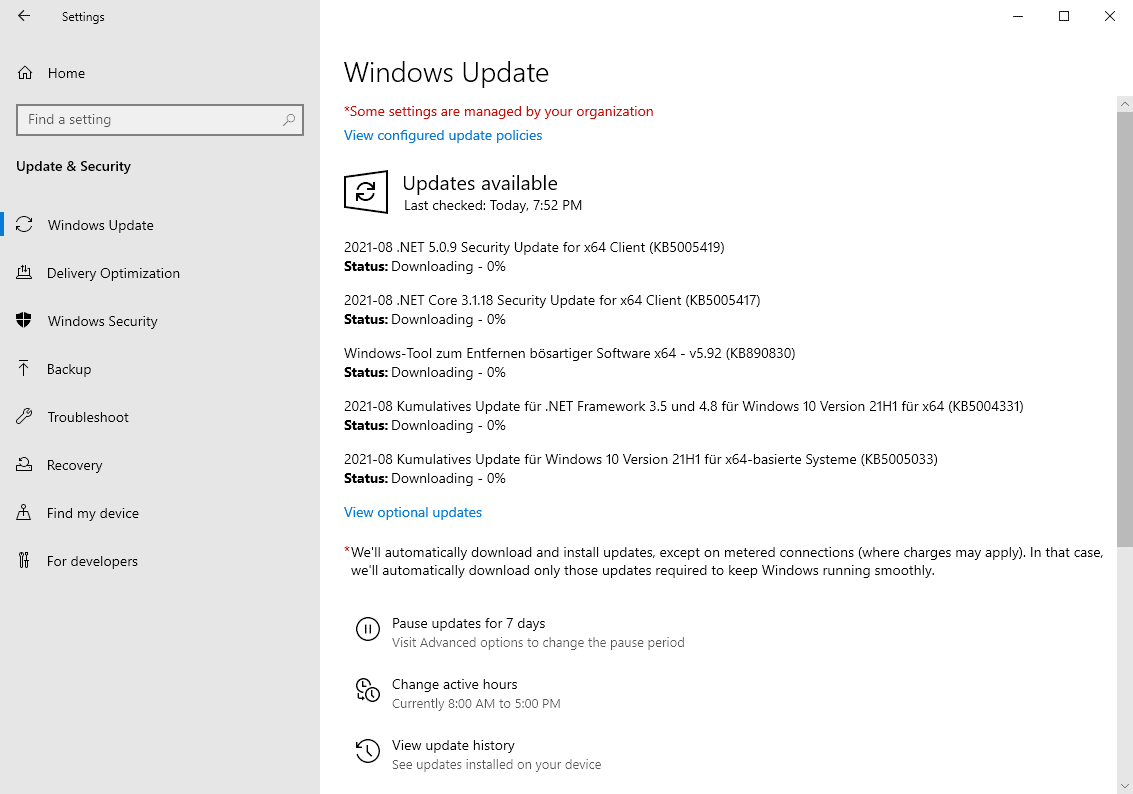
Today is Microsoft's August 2021 Patch Tuesday, and with it comes fixes for three zero-day vulnerabilities and a total of 44 flaws, so please be nice to your Windows admins as they scramble to installed patches.
Microsoft has fixed 44 vulnerabilities (51 including Microsoft Edge) with today's update, with seven classified as Critical and 37 as Important.
Of the 44 vulnerabilities, 13 are remote code execution, eight are information disclosure, two are denial of service, and four are spoofing vulnerabilities.
Microsoft fixes PrintNightmare and PetitPotam attacks
Microsoft has released security updates for two eagerly anticipated zero-day vulnerabilities that were discovered over the past month.
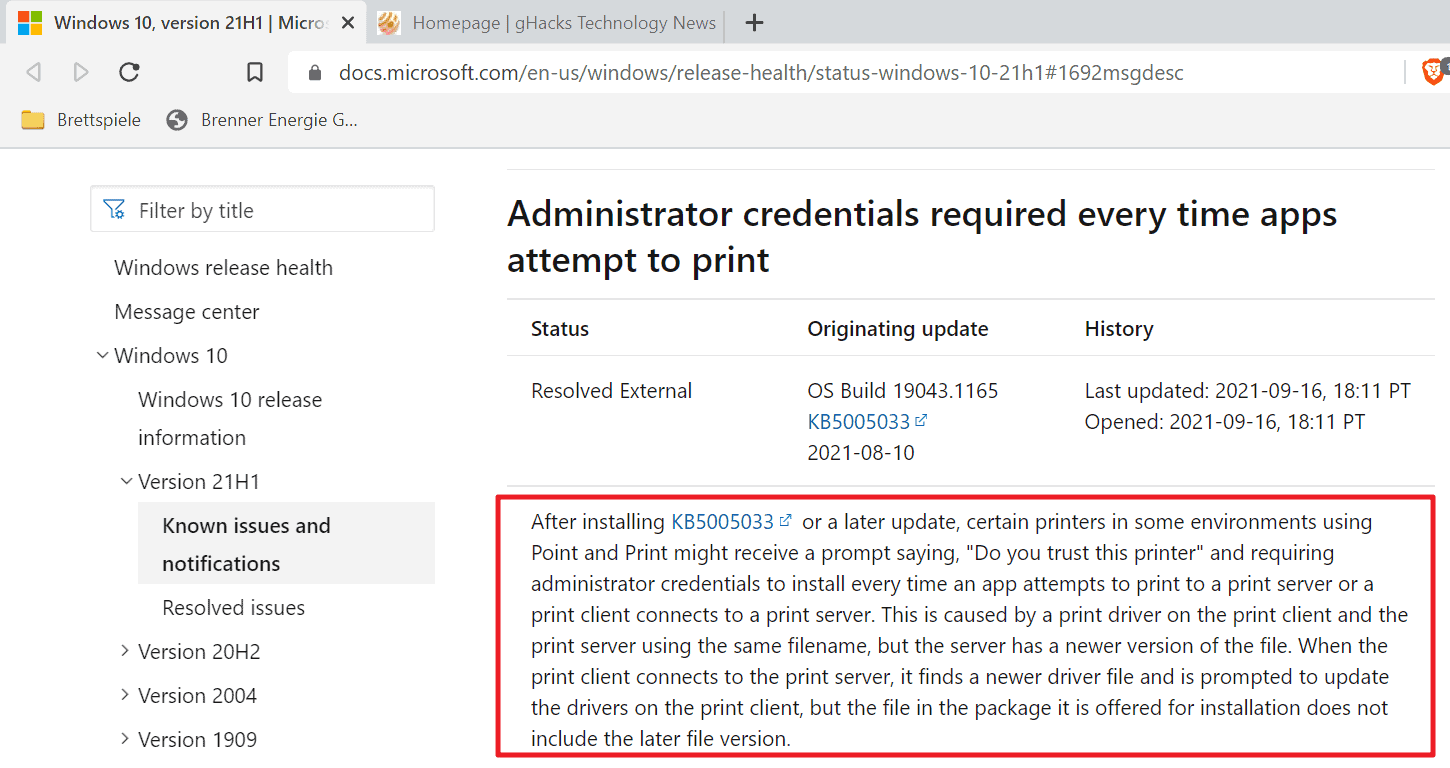
One of the security updates fixes the PrintNightmare vulnerabilities that allow threat actors to gain SYSTEM level privileges simply by connecting to a remote print server under their control. Microsoft has fixed this vulnerability by requiring users have administrative privileges to install printer drivers using the Point and Print Windows feature.
You can find more detailed information about the PrintNightmare vulnerability and the Point and Print mitigations in a dedicated article published today.
Microsoft also fixed the PetitPotam NTLM relay attack vector that uses the MS-EFSRPC API to force a device to negotiate with a remote relay server under an attacker's control.
A threat actor with low privileges could use this attack to take over a domain controller and thus the entire Windows domain.
Three zero-days fixed, with one actively exploited
August's Patch Tuesday includes three zero-day vulnerabilities, with one actively exploited in the wild.
Microsoft classifies a vulnerability as a zero-day if it is publicly disclosed or actively exploited with no official security updates or released.
The two publicly disclosed, but not actively exploited, zero-day vulnerabilities are:
The CVE-2021-36942 vulnerability is associated with the PetitPotam NTLM relay attack vector that allows the take over of domain controllers.
- CVE-2021-36936 - Windows Print Spooler Remote Code Execution Vulnerability
- CVE-2021-36942 - Windows LSA Spoofing Vulnerability
Finally, one actively exploited elevation of privileges vulnerability was discovered by the Microsoft Security Response Center (MSRC) and Microsoft Threat Intelligence Center (MSTIC).
It is unknown how threat actors used this vulnerability in attacks at this time.
- CVE-2021-36948 - Windows Update Medic Service Elevation of Privilege Vulnerability

Microsoft August 2021 Patch Tuesday fixes 3 zero-days, 44 flaws
Today is Microsoft's August 2021 Patch Tuesday, and with it comes fixes for three zero-day vulnerabilities and a total of 44 flaws, so please be nice to your Windows admins as they scramble to installed patches.
Last edited: