- Apr 9, 2018
- 228
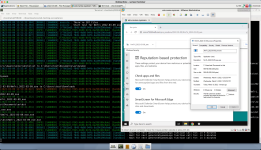
Instead of saying this, please check it. Download any EXE file via Google Chrome and use the right-click Explorer (file Explorer and not IE) context menu. You should see something like that:
As I mentioned above there is no such thing after downloading the file. No MOTW indicator.