- Apr 9, 2018
- 220
Greetings People! I know there are more important things going on right now, but all of us - as people from Poland and you, as a worldwide community, need to take care of our digital security. You know this, but your colleagues or family are not technical people. Therefore, as always, every other month we started with protection test of modern antivirus solutions on so-called samples in the wild that can be found in various areas of the Internet, also captured by our honeypots. This test is completely automated, so it can run continuously 24 hours a day.
In January 2022, we checked the following applications to protect PCs:
In our tests, we do not award negative or positive points for early blocking of threats. Simply put, security products must stop a threat in any way – designed by a developer. The final result is whether or not this has been achieved
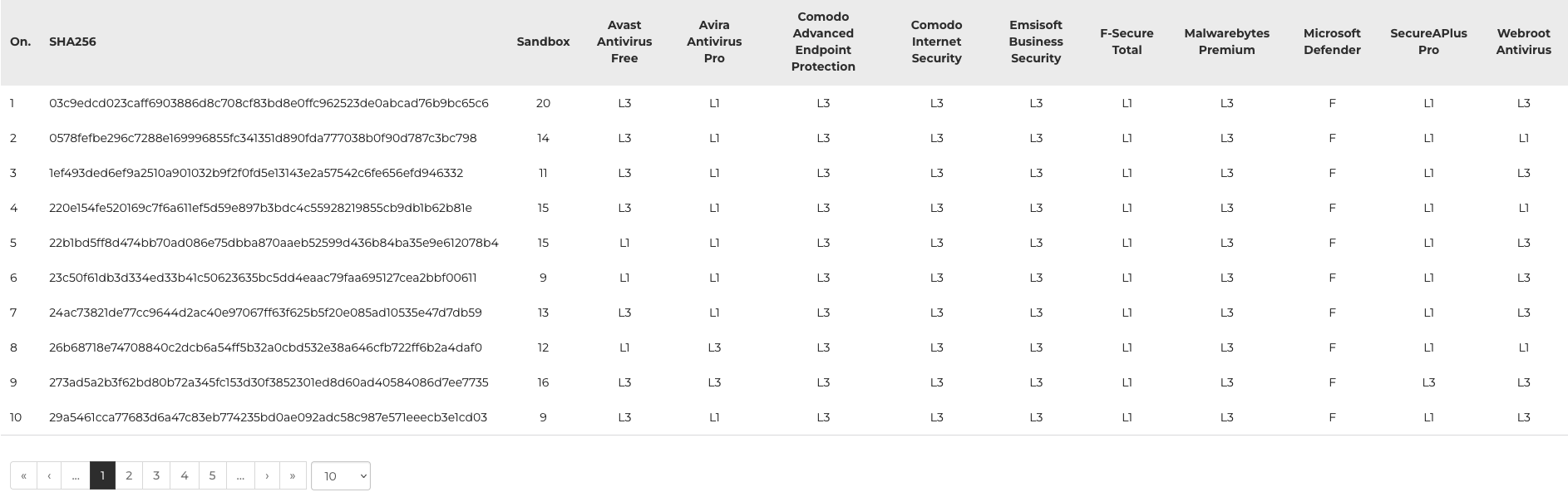
The so-called Level 1 shows early blocking of threats in a browser or on a hard drive.
If this fails, the next is Level 2: a virus is scanned by the antivirus based on signatures when moving from X to Y folder. Obviously, only if such protection exists. In this test, there are many test cases when samples have not been tested by developers yet, so the next level of analysis is crucial.
Level 3 represents modern protection without any signatures. In such cases, a virus is run in the operating system. It is the most dangerous situation but needed because it shows true effectiveness of protection against and 0-day files – a threat unknown to a developer of protection software.
Post Scriptum. We are gratefull you for voting for AVLab in the AV-Comparatives survey, as we were ranked 4th in 2020. In 2021 we are already 3rd (behind AV-Test and AV-C).
In January 2022, we checked the following applications to protect PCs:
- Avast Free Antivirus
- Avira Antivirus Pro
- Comodo Advanced Endpoint Protection
- Comodo Internet Security
- Emsisoft Business Security
- F-Secure Total (new)
- Malwarebytes Premium (new)
- Microsoft Defender
- SecureAPlus Pro
- Webroot Antivirus
Summary of January edition of the test
Notice the Level 3 of analysis because it shows real protection against 0-day samples. But beware! Certain antiviruses of the next generation intentionally do not have protection in a browser (Level 1). Sometimes they do not have traditional protection based on signatures (Level 1 and Level 2), so without proper interpretation, such tests could favor other protection solutions. Not ours!In our tests, we do not award negative or positive points for early blocking of threats. Simply put, security products must stop a threat in any way – designed by a developer. The final result is whether or not this has been achieved

The so-called Level 1 shows early blocking of threats in a browser or on a hard drive.
If this fails, the next is Level 2: a virus is scanned by the antivirus based on signatures when moving from X to Y folder. Obviously, only if such protection exists. In this test, there are many test cases when samples have not been tested by developers yet, so the next level of analysis is crucial.
Level 3 represents modern protection without any signatures. In such cases, a virus is run in the operating system. It is the most dangerous situation but needed because it shows true effectiveness of protection against and 0-day files – a threat unknown to a developer of protection software.
Post Scriptum. We are gratefull you for voting for AVLab in the AV-Comparatives survey, as we were ranked 4th in 2020. In 2021 we are already 3rd (behind AV-Test and AV-C).

