Reports are coming in from multiple security researchers and security firms about increased activity from one of the groups spreading the Locky ransomware.
These spam waves have started on September 18 and are pushing the new Locky ransomware variant that encrypts files
with the .ykcol extension, which was also released on the same day.
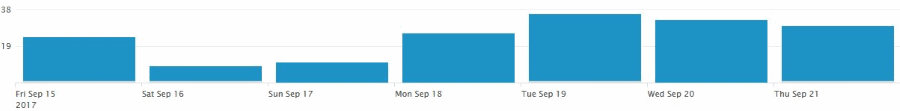
Six big spam waves detected
Six big spam waves pushing the Locky ykcol version were seen in the past few days. Locky versions distributed by these spam waves have embedded the #3 affiliate ID, belonging to the same group that was also busy pushing Locky spam
at the start of the month.
These Locky spam waves have been seen by
Fortinet (authors of the graph breakdown below),
Barkly,
Barracuda,
Brad Duncan, and My Online Security [
1,
2,
3].